截止4月11日hvv情报分享
作者:护网专题小组 编辑:白帽子社区运营团队
"白帽子社区在线CTF靶场BMZCTF,欢迎各位在这里练习、学习,BMZCTF全身心为网络安全赛手提供优质学习环境,链接(http://www.bmzclub.cn/)
"
HW专题篇(二)
首先还是先送上一部分封禁IP信息,相当可靠
119.45.165.175 |
218.28.13.98 |
118.190.103.114 |
120.77.244.249 |
61.148.244.78 |
120.77.244.249 |
221.122.70.7 |
221.122.70.6 |
221.122.70.5 |
221.122.70.3 |
221.122.70.2 |
121.4.173.142 |
223.104.39.176 |
218.206.233.26 |
212.32.236.219 |
38.68.37.88 |
目前可信度较高漏洞如下:
1 | 天擎前台SQL注入 |
2 | 泛微OA v8前台SQL注入 |
3 | 奇安信NS-NGFW 网康防火墙 前台RCE |
4 | 致远OA命令执行漏洞 |
5 | 用友NC6.5版本存在反序列化命令执行漏洞 |
6 | 泛微OA v9命令执行 |
7 | 亿邮电子邮件远程命令执行 |
8 | 泛微OA8的泛微e-mobile命令执行漏洞 |
9 | 金山终端安全系统存在文件上传漏洞 |
10 | 奇治堡垒机任意用户登录 |
11 | 浪潮 ClusterEngineV4.0 任意命令执行 |
附带部分脱敏exp:

Host: X.X.X.XUser-Agent:Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML,like Gecko) Version/12.0.3 Safari/605.1.15Content-Length: 155Content-Type:application/jsonX-Requested-With:XMLHttpRequestAccept-Encoding: gzip{"action":"SSLVPN_Resource","method":"此处手动屏蔽payload信息","data": [{"data":["此处手动屏蔽payload信息"]}],"type":"此处手动屏蔽payload信息","tid": 17}

POST/webadm/?q=moni_detail.do&action=gragh HTTP/1.1Host: 127.0.0.1User-Agent: Mozilla/5.0 (Windows NT10.0; WOW64; rv:46.0) Gecko/20100101Firefox/46.0Accept:text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language:zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateDNT: 1Connection: closeContent-Type:application/x-www-form-urlencodedContent-Length: 25type=此处手动屏蔽payload信息


POST /login HTTP/1.1Host: 127.0.0.1:8443User-Agent: Mozilla/5.0 (Windows NT10.0; WOW64; rv:46.0) Gecko/20100101Firefox/46.0Accept: application/json,text/javascript, */*; q=0.01Accept-Language:zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateDNT: 1Content-Type:application/x-www-form-urlencoded; charset=UTF-8X-Requested-With: XMLHttpRequestReferer:https://118.26.69.83:8443/module/login/login.htmlContent-Length: 43Cookie:Connection: closeop=此处手动屏蔽payload信息&username=此处手动屏蔽payload信息

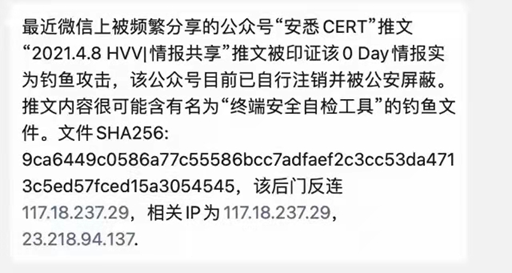


评论
