利用句柄表实现反调试
作者:Evan 编辑:白帽子社区运营团队
"白帽子社区在线CTF靶场BMZCTF,欢迎各位在这里练习、学习,BMZCTF全身心为网络安全赛手提供优质学习环境,链接(http://www.bmzclub.cn/)
"



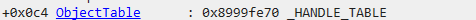
ntdll!_HANDLE_TABLE+0x000 TableCode : Uint4B+0x004 QuotaProcess : Ptr32 _EPROCESS+0x008 UniqueProcessId : Ptr32 Void+0x00c HandleTableLock : [4] _EX_PUSH_LOCK+0x01c HandleTableList : _LIST_ENTRY+0x024 HandleContentionEvent : _EX_PUSH_LOCK+0x028 DebugInfo : Ptr32 _HANDLE_TRACE_DEBUG_INFO+0x02c ExtraInfoPages : Int4B+0x030 FirstFree : Uint4B+0x034 LastFree : Uint4B+0x038 NextHandleNeedingPool : Uint4B+0x03c HandleCount : Int4B+0x040 Flags : Uint4B+0x040 StrictFIFO : Pos 0, 1 Bit

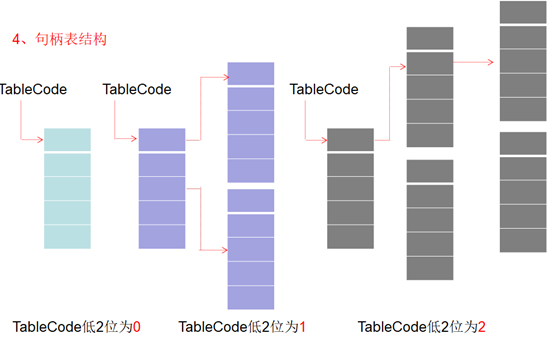

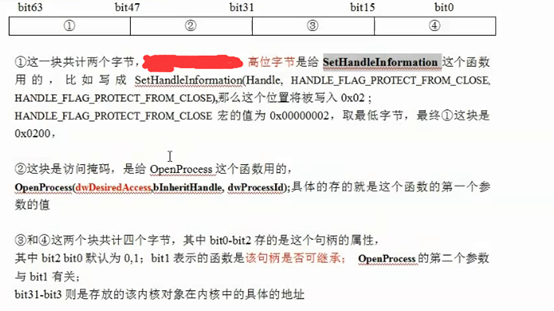

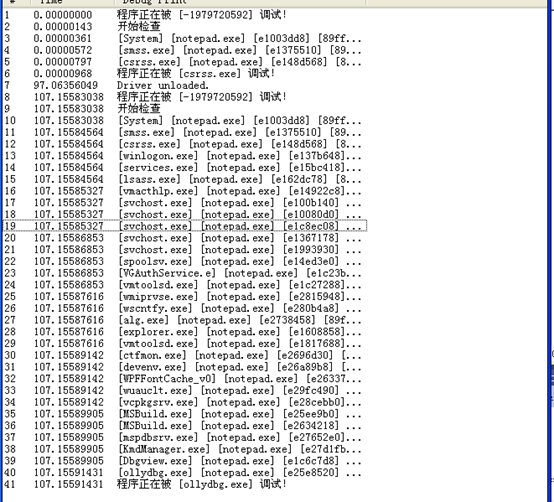
#include <ntddk.h>#include <ntstatus.h>ULONG GetProcessEprocess(char* ProcessName){PEPROCESSpEprocess,pCurEProcess;//获取进程的EProcess__asm{moveax,fs:[0x124]moveax,[eax+0x220]movpEprocess,eax}pCurEProcess=pEprocess;do{PCHARImageFileName=(PCHAR)pCurEProcess+0x174;if(strcmp(ImageFileName,ProcessName)==0){return (ULONG)pCurEProcess;}pCurEProcess=(PEPROCESS)(*(PULONG)((ULONG)pCurEProcess+0x88)-0x88);}while(pCurEProcess!=pEprocess);return0;}BOOLEAN CheckProcessDebug(ULONG CheckedProcess){PEPROCESSpEprocess,pCurEProcess;PULONG table;PEPROCESS eps;ULONG ObTable;int i,j,k;//获取进程的EProcess__asm{moveax,fs:[0x124]moveax,[eax+0x220]movpEprocess,eax}DbgPrint("开始检查\n");pCurEProcess=pEprocess;do{PCHARImageFileName=(PCHAR)pCurEProcess+0x174;ULONGObjectTable=*(PULONG)((ULONG)pCurEProcess+0xc4);if(ObjectTable!=0){DbgPrint("[%s]\t[%s]\t[%x]\t[%x]\n",ImageFileName,((PCHAR)CheckedProcess+0x174),ObjectTable,CheckedProcess);ObTable=(ULONG)ObjectTable;switch(ObTable&0x3){case0:table=(PULONG)((*(PULONG)ObTable)&0xfffffffc);for(i=0;i<512;i+=2){eps=(PEPROCESS)((table[i]&0xfffffff8)+0x18);//DbgPrint("程序正在被 [%x] 检查!\n", (ULONG)eps);if(strcmp(ImageFileName,"csrss.exe")!=0&&eps==(PEPROCESS)CheckedProcess){DbgPrint("程序正在被 [%s] 调试!\n", ImageFileName);return TRUE;}}break;case1:for(i=0;i<1024;i++){table=(PULONG)(*(PULONG)ObTable)+i;if(MmIsAddressValid((PVOID)table))for(j=0;j<512;j++){eps=(PEPROCESS)((ULONG)(table+j*2)&0xfffffff8+0x18);DbgPrint("程序正在被 [%s] 检查!\n", (PCHAR)eps+0x174);if(eps==(PEPROCESS)CheckedProcess){DbgPrint("程序正在被 [%s] 调试!\n", ImageFileName);return TRUE;}}}break;case2:for(i=0;i<1024;i++){table=(PULONG)(*(PULONG)ObTable)+i;if(MmIsAddressValid((PVOID)table))for(j=0;j<1024;j++){table=(PULONG)(*(PULONG)ObTable)+j;if(MmIsAddressValid((PVOID)table))for(k=0;k<512;k++){eps=(PEPROCESS)((ULONG)(table+k*2)&0xfffffff8+0x18);DbgPrint("程序正在被 [%s] 检查!\n", (PCHAR)eps+0x174);if(eps==(PEPROCESS)CheckedProcess){DbgPrint("程序正在被 [%s] 调试!\n", ImageFileName);return TRUE;}}}}break;default:DbgPrint("NoPass");}}pCurEProcess=(PEPROCESS)(*(PULONG)((ULONG)pCurEProcess+0x88)-0x88);}while(pCurEProcess!=pEprocess);DbgPrint("Processing is not debug");return FALSE;}VOID DriverUnload(PDRIVER_OBJECT pDriver){DbgPrint("Driver unloaded.\n");}NTSTATUS DriverEntry(PDRIVER_OBJECT pDriver,PUNICODE_STRING reg_path){ULONG addr;pDriver->DriverUnload = DriverUnload;//获取需要保护的进程的EProcessaddr=GetProcessEprocess("notepad.exe");DbgPrint("程序正在被 [%d] 调试!\n", addr);CheckProcessDebug(addr);return STATUS_SUCCESS;}
评论
