Linux 10个帮助你调试的命令


点击「阅读原文」查看良许原创精品视频。
来自:嵌入式Linux
文章目录
#file
#ldd
#ltrace
#hexdump
#strings
#readelf
#objdump
#strace
#nm
#gdb
磨刀不误砍柴工,Linux下也是一样,你掌握了正确的调试手段,对你的开发会非常有帮助。总结的这几个命令非常经典。
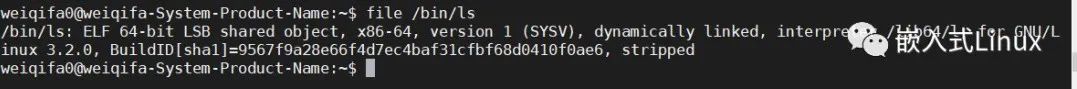
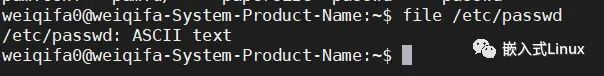
这个命令可以查看文件的确切文件类型
如何找到可执行文件所依赖的库?这就是ldd命令出现的原因,有人的地方就有江湖,有需要我的地方就应该出现我。针对动态链接的二进制文件运行它会显示其所有依赖的库及其路径。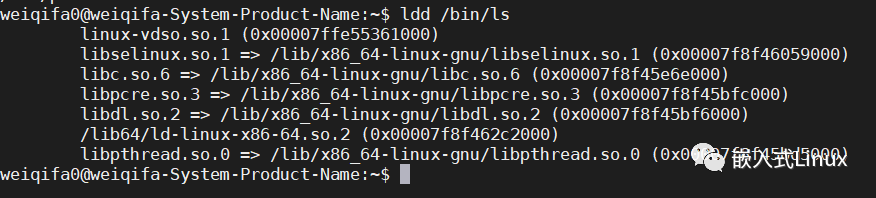
这个命令可以追踪命令运行的时候跑了哪些函数,可以作为堆栈调用跟踪调试使用。ltrace能够跟踪进程的库函数调用,它会显现出哪个库函数被调用。
详细链接:
https://www.cnblogs.com/machangwei-8/p/10388938.html
-a 对齐具体某个列的返回值。
-c 计算时间和调用,并在程序退出时打印摘要。
-C 解码低级别名称(内核级)为用户级名称。
-d 打印调试信息。
-e 改变跟踪的事件。
-f 跟踪子进程。
-h 打印帮助信息。
-i 打印指令指针,当库调用时。
-l 只打印某个库中的调用。
-L 不打印库调用。
-n, --indent=NR 对每个调用级别嵌套以NR个空格进行缩进输出。
-o, --output=file 把输出定向到文件。
-p PID 附着在值为PID的进程号上进行ltrace。
-r 打印相对时间戳。
-s STRLEN 设置打印的字符串最大长度。
-S 显示系统调用。
-t, -tt, -ttt 打印绝对时间戳。
-T 输出每个调用过程的时间开销。
-u USERNAME 使用某个用户id或组ID来运行命令。
-V, --version 打印版本信息,然后退出。
-x NAME treat the global NAME like a library subroutine.weiqifa0@weiqifa-System-Product-Name:~$ ltrace ls
strrchr("ls", '/') = nil
setlocale(LC_ALL, "") = "zh_CN.UTF-8"
bindtextdomain("coreutils", "/usr/share/locale") = "/usr/share/locale"
textdomain("coreutils") = "coreutils"
__cxa_atexit(0x5594e2fd9ca0, 0, 0x5594e31ed008, 0x736c6974756572) = 0
isatty(1) = 1
getenv("QUOTING_STYLE") = nil
getenv("COLUMNS") = nil
ioctl(1, 21523, 0x7fff061929c0) = 0
getenv("TABSIZE") = nil
getopt_long(1, 0x7fff06192af8, "abcdfghiklmnopqrstuvw:xABCDFGHI:"..., 0x5594e31ec2e0, -1) = -1
getenv("LS_BLOCK_SIZE") = nil
getenv("BLOCK_SIZE") = nil
getenv("BLOCKSIZE") = nil
getenv("POSIXLY_CORRECT") = nil
getenv("BLOCK_SIZE") = nil
__errno_location() = 0x7f3801ac0258
memcpy(0x5594e4a91a50, "\003\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0"..., 56) = 0x5594e4a91a50
__errno_location() = 0x7f3801ac0258
memcpy(0x5594e4a91a90, "\003\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0"..., 56) = 0x5594e4a91a90
getenv("TZ") = nil
strlen(".") = 1
memcpy(0x5594e4a969c0, ".\0", 2) = 0x5594e4a969c0
__errno_location() = 0x7f3801ac0258
opendir(".") = 0x5594e4a969e0
readdir(0x5594e4a969e0) = 0x5594e4a96a10
__errno_location() = 0x7f3801ac0258
__ctype_get_mb_cur_max() = 6
strlen("Desktop") = 7
strlen("Desktop") = 7
memcpy(0x5594e4a9ea20, "Desktop\0", 8) = 0x5594e4a9ea20
readdir(0x5594e4a969e0) = 0x5594e4a96a30
readdir(0x5594e4a969e0) = 0x5594e4a96a50
readdir(0x5594e4a969e0) = 0x5594e4a96a70
readdir(0x5594e4a969e0) = 0x5594e4a96a90
readdir(0x5594e4a969e0) = 0x5594e4a96ab0
__errno_location() = 0x7f3801ac0258
__ctype_get_mb_cur_max() = 6
strlen("examples.desktop") = 16
strlen("examples.desktop") = 16
memcpy(0x5594e4a9ea40, "examples.desktop\0", 17) = 0x5594e4a9ea40
readdir(0x5594e4a969e0) = 0x5594e4a96ad8
readdir(0x5594e4a969e0) = 0x5594e4a96af8
readdir(0x5594e4a969e0) = 0x5594e4a96b20
__errno_location() = 0x7f3801ac0258
__ctype_get_mb_cur_max() = 6
strlen("Public") = 6
strlen("Public") = 6
memcpy(0x5594e4a9ea60, "Public\0", 7) = 0x5594e4a9ea60
readdir(0x5594e4a969e0) = 0x5594e4a96b40
readdir(0x5594e4a969e0) = 0x5594e4a96b68
__errno_location() = 0x7f3801ac0258
__ctype_get_mb_cur_max() = 6
strlen("Pictures") = 8
strlen("Pictures") = 8
memcpy(0x5594e4a9ea80, "Pictures\0", 9) = 0x5594e4a9ea80
readdir(0x5594e4a969e0) = 0x5594e4a96b88
readdir(0x5594e4a969e0) = 0x5594e4a96ba8
readdir(0x5594e4a969e0) = 0x5594e4a96bc0
readdir(0x5594e4a969e0) = 0x5594e4a96bd8
readdir(0x5594e4a969e0) = 0x5594e4a96bf8
readdir(0x5594e4a969e0) = 0x5594e4a96c28
__errno_location() = 0x7f3801ac0258
__ctype_get_mb_cur_max() = 6
strlen("Videos") = 6
strlen("Videos") = 6
memcpy(0x5594e4a9eaa0, "Videos\0", 7) = 0x5594e4a9eaa0
readdir(0x5594e4a969e0) = 0x5594e4a96c48
__errno_location() = 0x7f3801ac0258
__ctype_get_mb_cur_max() = 6
strlen("Music") = 5
strlen("Music") = 5
memcpy(0x5594e4a9eac0, "Music\0", 6) = 0x5594e4a9eac0
readdir(0x5594e4a969e0) = 0x5594e4a96c68
readdir(0x5594e4a969e0) = 0x5594e4a96c80
readdir(0x5594e4a969e0) = 0x5594e4a96ca0
readdir(0x5594e4a969e0) = 0x5594e4a96cc0
readdir(0x5594e4a969e0) = 0x5594e4a96ce0
readdir(0x5594e4a969e0) = 0x5594e4a96d00
readdir(0x5594e4a969e0) = 0x5594e4a96d20
__errno_location() = 0x7f3801ac0258
__ctype_get_mb_cur_max() = 6
strlen("c") = 1
strlen("c") = 1
memcpy(0x5594e4a9eae0, "c\0", 2) = 0x5594e4a9eae0
readdir(0x5594e4a969e0) = 0x5594e4a96d38
readdir(0x5594e4a969e0) = 0x5594e4a96d58
readdir(0x5594e4a969e0) = 0x5594e4a96d78
readdir(0x5594e4a969e0) = 0x5594e4a96d98
readdir(0x5594e4a969e0) = 0x5594e4a96db8
readdir(0x5594e4a969e0) = 0x5594e4a96de0
readdir(0x5594e4a969e0) = 0x5594e4a96e00
__errno_location() = 0x7f3801ac0258
__ctype_get_mb_cur_max() = 6
strlen("Templates") = 9
strlen("Templates") = 9
memcpy(0x5594e4a9eb00, "Templates\0", 10) = 0x5594e4a9eb00
readdir(0x5594e4a969e0) = 0x5594e4a96e20
readdir(0x5594e4a969e0) = 0x5594e4a96e48
readdir(0x5594e4a969e0) = 0x5594e4a96e68
readdir(0x5594e4a969e0) = 0x5594e4a96e88
readdir(0x5594e4a969e0) = 0x5594e4a96eb0
readdir(0x5594e4a969e0) = 0x5594e4a96ed0
readdir(0x5594e4a969e0) = 0x5594e4a96ee8
__errno_location() = 0x7f3801ac0258
__ctype_get_mb_cur_max() = 6
strlen("Downloads") = 9
strlen("Downloads") = 9
memcpy(0x5594e4a9eb20, "Downloads\0", 10) = 0x5594e4a9eb20
readdir(0x5594e4a969e0) = 0x5594e4a96f08
__errno_location() = 0x7f3801ac0258
__ctype_get_mb_cur_max() = 6
strlen("Documents") = 9
strlen("Documents") = 9
memcpy(0x5594e4a9eb40, "Documents\0", 10) = 0x5594e4a9eb40
readdir(0x5594e4a969e0) = 0
closedir(0x5594e4a969e0) = 0
_setjmp(0x5594e31ed300, 0x7f3801f3f3f0, 0x5594e4a96a30, 0x5594e4a92330) = 0
__errno_location() = 0x7f3801ac0258
strcoll("Downloads", "Documents") = 4
__errno_location() = 0x7f3801ac0258
strcoll("Templates", "Documents") = 3
__errno_location() = 0x7f3801ac0258
strcoll("Templates", "Downloads") = 3
memcpy(0x5594e4a96a28, "\330 \251\344\224U\0\0", 8) = 0x5594e4a96a28
__errno_location() = 0x7f3801ac0258
strcoll("Music", "c") = 1
memcpy(0x5594e4a96a38, "H\037\251\344\224U\0\0", 8) = 0x5594e4a96a38
__errno_location() = 0x7f3801ac0258
strcoll("c", "Documents") = -9
__errno_location() = 0x7f3801ac0258
strcoll("Music", "Documents") = 1
__errno_location() = 0x7f3801ac0258
strcoll("Music", "Downloads") = 1
__errno_location() = 0x7f3801ac0258
strcoll("Music", "Templates") = -2
__errno_location() = 0x7f3801ac0258
strcoll("Pictures", "Videos") = -2
__errno_location() = 0x7f3801ac0258
strcoll("Public", "Pictures") = 2
__errno_location() = 0x7f3801ac0258
strcoll("Public", "Videos") = -2
__errno_location() = 0x7f3801ac0258
strcoll("Desktop", "examples.desktop") = -12
__errno_location() = 0x7f3801ac0258
strcoll("Desktop", "Pictures") = -2
__errno_location() = 0x7f3801ac0258
strcoll("examples.desktop", "Pictures") = -2
memcpy(0x5594e4a96a40, "\270\035\251\344\224U\0\0\360\034\251\344\224U\0\0\200\036\251\344\224U\0\0", 24) = 0x5594e4a96a40
__errno_location() = 0x7f3801ac0258
strcoll("Desktop", "c") = 9
__errno_location() = 0x7f3801ac0258
strcoll("Desktop", "Documents") = -2
__errno_location() = 0x7f3801ac0258
strcoll("examples.desktop", "Documents") = 12
__errno_location() = 0x7f3801ac0258
strcoll("examples.desktop", "Downloads") = 12
__errno_location() = 0x7f3801ac0258
strcoll("examples.desktop", "Music") = -1
__errno_location() = 0x7f3801ac0258
strcoll("Pictures", "Music") = 1
__errno_location() = 0x7f3801ac0258
strcoll("Pictures", "Templates") = -1
__errno_location() = 0x7f3801ac0258
strcoll("Public", "Templates") = -1
__errno_location() = 0x7f3801ac0258
strcoll("Videos", "Templates") = 1
memcpy(0x5594e4a96a28, "\200\036\251\344\224U\0\0", 8) = 0x5594e4a96a28
realloc(0, 480) = 0x5594e4a96ae0
strlen("c") = 1
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("Desktop") = 7
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("Documents") = 9
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("Downloads") = 9
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("examples.desktop") = 16
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("Music") = 5
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("Pictures") = 8
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("Public") = 6
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("Templates") = 9
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("Videos") = 6
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("c") = 1
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("c") = 1
fwrite_unlocked("c", 1, 1, 0x7f3801f3f760) = 1
__overflow(0x7f3801f3f760, 32, 2, 8) = 32
__overflow(0x7f3801f3f760, 32, 3, 8) = 32
strlen("Desktop") = 7
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("Desktop") = 7
fwrite_unlocked("Desktop", 1, 7, 0x7f3801f3f760) = 7
__overflow(0x7f3801f3f760, 32, 3, 8) = 32
__overflow(0x7f3801f3f760, 32, 4, 8) = 32
strlen("Documents") = 9
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("Documents") = 9
fwrite_unlocked("Documents", 1, 9, 0x7f3801f3f760) = 9
__overflow(0x7f3801f3f760, 32, 6, 8) = 32
__overflow(0x7f3801f3f760, 32, 7, 8) = 32
strlen("Downloads") = 9
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("Downloads") = 9
fwrite_unlocked("Downloads", 1, 9, 0x7f3801f3f760) = 9
__overflow(0x7f3801f3f760, 32, 1, 8) = 32
__overflow(0x7f3801f3f760, 32, 2, 8) = 32
strlen("examples.desktop") = 16
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("examples.desktop") = 16
fwrite_unlocked("examples.desktop", 1, 16, 0x7f3801f3f760) = 16
__overflow(0x7f3801f3f760, 32, 3, 8) = 32
__overflow(0x7f3801f3f760, 32, 4, 8) = 32
strlen("Music") = 5
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("Music") = 5
fwrite_unlocked("Music", 1, 5, 0x7f3801f3f760) = 5
__overflow(0x7f3801f3f760, 32, 2, 8) = 32
__overflow(0x7f3801f3f760, 32, 3, 8) = 32
strlen("Pictures") = 8
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("Pictures") = 8
fwrite_unlocked("Pictures", 1, 8, 0x7f3801f3f760) = 8
__overflow(0x7f3801f3f760, 32, 4, 8) = 32
__overflow(0x7f3801f3f760, 32, 5, 8) = 32
strlen("Public") = 6
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("Public") = 6
fwrite_unlocked("Public", 1, 6, 0x7f3801f3f760) = 6
__overflow(0x7f3801f3f760, 32, 4, 8) = 32
__overflow(0x7f3801f3f760, 32, 5, 8) = 32
strlen("Templates") = 9
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("Templates") = 9
fwrite_unlocked("Templates", 1, 9, 0x7f3801f3f760) = 9
__overflow(0x7f3801f3f760, 9, 7, 8) = 9
strlen("Videos") = 6
__ctype_get_mb_cur_max() = 6
__ctype_get_mb_cur_max() = 6
strlen("Videos") = 6
fwrite_unlocked("Videos", 1, 6, 0x7f3801f3f760) = 6
__overflow(0x7f3801f3f760, 10, 0x1d15f2f23c04cf00, 0x736f6564c Desktop Documents Downloads examples.desktop Music Pictures Public Templates Videos
) = 10
__fpending(0x7f3801f3f760, 0, 0x5594e2fd9ca0, 1) = 0
fileno(0x7f3801f3f760) = 1
__freading(0x7f3801f3f760, 0, 0x5594e2fd9ca0, 1) = 0
__freading(0x7f3801f3f760, 0, 2052, 1) = 0
fflush(0x7f3801f3f760) = 0
fclose(0x7f3801f3f760) = 0
__fpending(0x7f3801f3f680, 0, 0x7f3801f3f960, 3072) = 0
fileno(0x7f3801f3f680) = 2
__freading(0x7f3801f3f680, 0, 0x7f3801f3f960, 3072) = 0
__freading(0x7f3801f3f680, 0, 4, 3072) = 0
fflush(0x7f3801f3f680) = 0
fclose(0x7f3801f3f680) = 0
+++ exited (status 0) +++
weiqifa0@weiqifa-System-Product-Name:~$
从名字可以看出这个是用来查看文件的十六进制的。
weiqifa0@weiqifa-System-Product-Name:~$ hexdump /bin/ls |head
0000000 457f 464c 0102 0001 0000 0000 0000 0000
0000010 0003 003e 0001 0000 5850 0000 0000 0000
0000020 0040 0000 0000 0000 03a0 0002 0000 0000
0000030 0000 0000 0040 0038 0009 0040 001c 001b
0000040 0006 0000 0005 0000 0040 0000 0000 0000
0000050 0040 0000 0000 0000 0040 0000 0000 0000
0000060 01f8 0000 0000 0000 01f8 0000 0000 0000
0000070 0008 0000 0000 0000 0003 0000 0004 0000
0000080 0238 0000 0000 0000 0238 0000 0000 0000
0000090 0238 0000 0000 0000 001c 0000 0000 0000
weiqifa0@weiqifa-System-Product-Name:~$
这个之前在文件dts解析里面有说过,是一个非常不错的命令,用来查看Bin里面有什么字符串。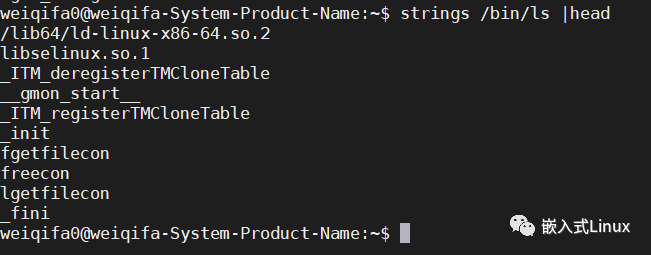
一般用于查看ELF格式的文件信息,常见的文件如在Linux上的可执行文件,动态库(* .so)或者静态库(* .a) 等包含ELF格式的文件。以下命令的使用是基于android编译出来的so文件上面去运行。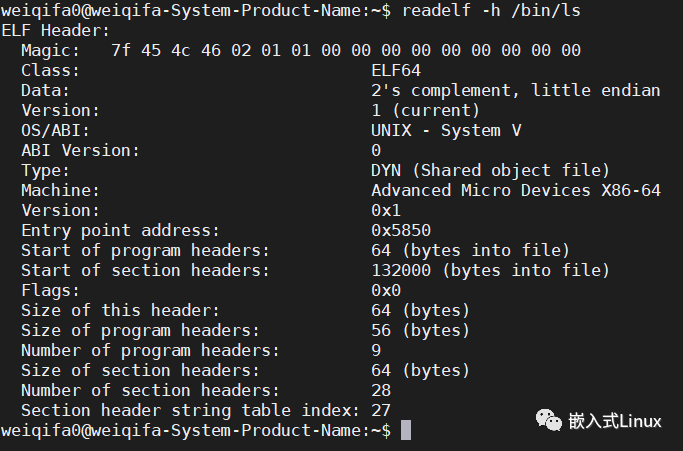
这个命令主要用来反汇编格式。
weiqifa0@weiqifa-System-Product-Name:~/c$ cat 1.c
#include "stdio.h"
int main(void)
{
printf("hello,world\n");
return (0);
}
weiqifa0@weiqifa-System-Product-Name:~/c$ gcc 1.c -o 1.o
weiqifa0@weiqifa-System-Product-Name:~/c$ objdump -h 1.o
1.o: file format elf64-x86-64
Sections:
Idx Name Size VMA LMA File off Algn
0 .interp 0000001c 00000000000002a8 00000000000002a8 000002a8 2**0
CONTENTS, ALLOC, LOAD, READONLY, DATA
1 .note.gnu.build-id 00000024 00000000000002c4 00000000000002c4 000002c4 2**2
CONTENTS, ALLOC, LOAD, READONLY, DATA
2 .note.ABI-tag 00000020 00000000000002e8 00000000000002e8 000002e8 2**2
CONTENTS, ALLOC, LOAD, READONLY, DATA
3 .gnu.hash 00000024 0000000000000308 0000000000000308 00000308 2**3
CONTENTS, ALLOC, LOAD, READONLY, DATA
4 .dynsym 000000a8 0000000000000330 0000000000000330 00000330 2**3
CONTENTS, ALLOC, LOAD, READONLY, DATA
5 .dynstr 00000082 00000000000003d8 00000000000003d8 000003d8 2**0
CONTENTS, ALLOC, LOAD, READONLY, DATA
6 .gnu.version 0000000e 000000000000045a 000000000000045a 0000045a 2**1
CONTENTS, ALLOC, LOAD, READONLY, DATA
7 .gnu.version_r 00000020 0000000000000468 0000000000000468 00000468 2**3
CONTENTS, ALLOC, LOAD, READONLY, DATA
8 .rela.dyn 000000c0 0000000000000488 0000000000000488 00000488 2**3
CONTENTS, ALLOC, LOAD, READONLY, DATA
9 .rela.plt 00000018 0000000000000548 0000000000000548 00000548 2**3
CONTENTS, ALLOC, LOAD, READONLY, DATA
10 .init 00000017 0000000000001000 0000000000001000 00001000 2**2
CONTENTS, ALLOC, LOAD, READONLY, CODE
11 .plt 00000020 0000000000001020 0000000000001020 00001020 2**4
CONTENTS, ALLOC, LOAD, READONLY, CODE
12 .plt.got 00000008 0000000000001040 0000000000001040 00001040 2**3
CONTENTS, ALLOC, LOAD, READONLY, CODE
13 .text 00000161 0000000000001050 0000000000001050 00001050 2**4
CONTENTS, ALLOC, LOAD, READONLY, CODE
14 .fini 00000009 00000000000011b4 00000000000011b4 000011b4 2**2
CONTENTS, ALLOC, LOAD, READONLY, CODE
15 .rodata 00000010 0000000000002000 0000000000002000 00002000 2**2
CONTENTS, ALLOC, LOAD, READONLY, DATA
16 .eh_frame_hdr 0000003c 0000000000002010 0000000000002010 00002010 2**2
CONTENTS, ALLOC, LOAD, READONLY, DATA
17 .eh_frame 00000108 0000000000002050 0000000000002050 00002050 2**3
CONTENTS, ALLOC, LOAD, READONLY, DATA
18 .init_array 00000008 0000000000003db8 0000000000003db8 00002db8 2**3
CONTENTS, ALLOC, LOAD, DATA
19 .fini_array 00000008 0000000000003dc0 0000000000003dc0 00002dc0 2**3
CONTENTS, ALLOC, LOAD, DATA
20 .dynamic 000001f0 0000000000003dc8 0000000000003dc8 00002dc8 2**3
CONTENTS, ALLOC, LOAD, DATA
21 .got 00000048 0000000000003fb8 0000000000003fb8 00002fb8 2**3
CONTENTS, ALLOC, LOAD, DATA
22 .data 00000010 0000000000004000 0000000000004000 00003000 2**3
CONTENTS, ALLOC, LOAD, DATA
23 .bss 00000008 0000000000004010 0000000000004010 00003010 2**0
ALLOC
24 .comment 00000023 0000000000000000 0000000000000000 00003010 2**0
CONTENTS, READONLY
weiqifa0@weiqifa-System-Product-Name:~/c$
strace是一个非常简单的工具,它可以跟踪系统调用的执行。最简单的方式,它可以从头到尾跟踪binary的执行,然后以一行文本输出系统调用的名字,参数和返回值。
详细链接:
https://blog.csdn.net/uisoul/article/details/83143290
weiqifa0@weiqifa-System-Product-Name:~/c$ strace /bin/ls
execve("/bin/ls", ["/bin/ls"], 0x7ffdb4868620 /* 23 vars */) = 0
brk(NULL) = 0x55ebe6544000
access("/etc/ld.so.preload", R_OK) = -1 ENOENT (No such file or directory)
openat(AT_FDCWD, "/etc/ld.so.cache", O_RDONLY|O_CLOEXEC) = 3
fstat(3, {st_mode=S_IFREG|0644, st_size=109714, ...}) = 0
mmap(NULL, 109714, PROT_READ, MAP_PRIVATE, 3, 0) = 0x7fc672283000
close(3) = 0
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libselinux.so.1", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0 h\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0644, st_size=158928, ...}) = 0
mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7fc672281000
mmap(NULL, 170192, PROT_READ, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7fc672257000
mprotect(0x7fc67225d000, 131072, PROT_NONE) = 0
mmap(0x7fc67225d000, 98304, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x6000) = 0x7fc67225d000
mmap(0x7fc672275000, 28672, PROT_READ, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1e000) = 0x7fc672275000
mmap(0x7fc67227d000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x25000) = 0x7fc67227d000
mmap(0x7fc67227f000, 6352, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7fc67227f000
close(3) = 0
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libc.so.6", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\3\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\200l\2\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=2000480, ...}) = 0
mmap(NULL, 2008696, PROT_READ, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7fc67206c000
mmap(0x7fc672091000, 1519616, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x25000) = 0x7fc672091000
mmap(0x7fc672204000, 299008, PROT_READ, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x198000) = 0x7fc672204000
mmap(0x7fc67224d000, 24576, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1e0000) = 0x7fc67224d000
mmap(0x7fc672253000, 13944, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7fc672253000
close(3) = 0
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libpcre.so.3", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0 \25\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0644, st_size=464824, ...}) = 0
mmap(NULL, 2560264, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7fc671dfa000
mprotect(0x7fc671e6a000, 2097152, PROT_NONE) = 0
mmap(0x7fc67206a000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x70000) = 0x7fc67206a000
close(3) = 0
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libdl.so.2", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0000\21\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0644, st_size=18656, ...}) = 0
mmap(NULL, 20752, PROT_READ, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7fc671df4000
mmap(0x7fc671df5000, 8192, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1000) = 0x7fc671df5000
mmap(0x7fc671df7000, 4096, PROT_READ, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x3000) = 0x7fc671df7000
mmap(0x7fc671df8000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x3000) = 0x7fc671df8000
close(3) = 0
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libpthread.so.0", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\3\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\200|\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=149840, ...}) = 0
mmap(NULL, 132288, PROT_READ, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7fc671dd3000
mmap(0x7fc671dda000, 61440, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x7000) = 0x7fc671dda000
mmap(0x7fc671de9000, 20480, PROT_READ, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x16000) = 0x7fc671de9000
mmap(0x7fc671dee000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1a000) = 0x7fc671dee000
mmap(0x7fc671df0000, 13504, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7fc671df0000
close(3) = 0
mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7fc671dd1000
arch_prctl(ARCH_SET_FS, 0x7fc671dd23c0) = 0
mprotect(0x7fc67224d000, 12288, PROT_READ) = 0
mprotect(0x7fc671dee000, 4096, PROT_READ) = 0
mprotect(0x7fc671df8000, 4096, PROT_READ) = 0
mprotect(0x7fc67206a000, 4096, PROT_READ) = 0
mprotect(0x7fc67227d000, 4096, PROT_READ) = 0
mprotect(0x55ebe4612000, 8192, PROT_READ) = 0
mprotect(0x7fc6722c8000, 4096, PROT_READ) = 0
munmap(0x7fc672283000, 109714) = 0
set_tid_address(0x7fc671dd2690) = 15038
set_robust_list(0x7fc671dd26a0, 24) = 0
rt_sigaction(SIGRTMIN, {sa_handler=0x7fc671dda6c0, sa_mask=[], sa_flags=SA_RESTORER|SA_SIGINFO, sa_restorer=0x7fc671de6f40}, NULL, 8) = 0
rt_sigaction(SIGRT_1, {sa_handler=0x7fc671dda760, sa_mask=[], sa_flags=SA_RESTORER|SA_RESTART|SA_SIGINFO, sa_restorer=0x7fc671de6f40}, NULL, 8) = 0
rt_sigprocmask(SIG_UNBLOCK, [RTMIN RT_1], NULL, 8) = 0
prlimit64(0, RLIMIT_STACK, NULL, {rlim_cur=8192*1024, rlim_max=RLIM64_INFINITY}) = 0
statfs("/sys/fs/selinux", 0x7ffdfa4ebb30) = -1 ENOENT (No such file or directory)
statfs("/selinux", 0x7ffdfa4ebb30) = -1 ENOENT (No such file or directory)
brk(NULL) = 0x55ebe6544000
brk(0x55ebe6565000) = 0x55ebe6565000
openat(AT_FDCWD, "/proc/filesystems", O_RDONLY|O_CLOEXEC) = 3
fstat(3, {st_mode=S_IFREG|0444, st_size=0, ...}) = 0
read(3, "nodev\tsysfs\nnodev\trootfs\nnodev\tr"..., 1024) = 423
read(3, "", 1024) = 0
close(3) = 0
access("/etc/selinux/config", F_OK) = -1 ENOENT (No such file or directory)
openat(AT_FDCWD, "/usr/lib/locale/locale-archive", O_RDONLY|O_CLOEXEC) = 3
fstat(3, {st_mode=S_IFREG|0644, st_size=8841488, ...}) = 0
mmap(NULL, 8841488, PROT_READ, MAP_PRIVATE, 3, 0) = 0x7fc671562000
close(3) = 0
ioctl(1, TCGETS, {B38400 opost isig icanon echo ...}) = 0
ioctl(1, TIOCGWINSZ, {ws_row=27, ws_col=116, ws_xpixel=0, ws_ypixel=0}) = 0
openat(AT_FDCWD, ".", O_RDONLY|O_NONBLOCK|O_CLOEXEC|O_DIRECTORY) = 3
fstat(3, {st_mode=S_IFDIR|0775, st_size=4096, ...}) = 0
getdents64(3, /* 4 entries */, 32768) = 96
getdents64(3, /* 0 entries */, 32768) = 0
close(3) = 0
fstat(1, {st_mode=S_IFCHR|0620, st_rdev=makedev(136, 0), ...}) = 0
write(1, "1.c 1.o\n", 91.c 1.o
) = 9
close(1) = 0
close(2) = 0
exit_group(0) = ?
+++ exited with 0 +++
weiqifa0@weiqifa-System-Product-Name:~/c$这个命令可以看到链接库的地址,实际使用的时候会发现非常爽。
weiqifa0@weiqifa-System-Product-Name:~/c$ cat 1.c
#include "stdio.h"
int main(void)
{
printf("hello,world\n");
return (0);
}
weiqifa0@weiqifa-System-Product-Name:~/c$ gcc 1.c -o 1.o
weiqifa0@weiqifa-System-Product-Name:~/c$ nm 1.o
0000000000004010 B __bss_start
0000000000004010 b completed.7963
w __cxa_finalize@@GLIBC_2.2.5
0000000000004000 D __data_start
0000000000004000 W data_start
0000000000001080 t deregister_tm_clones
00000000000010f0 t __do_global_dtors_aux
0000000000003dc0 t __do_global_dtors_aux_fini_array_entry
0000000000004008 D __dso_handle
0000000000003dc8 d _DYNAMIC
0000000000004010 D _edata
0000000000004018 B _end
00000000000011b4 T _fini
0000000000001130 t frame_dummy
0000000000003db8 t __frame_dummy_init_array_entry
0000000000002154 r __FRAME_END__
0000000000003fb8 d _GLOBAL_OFFSET_TABLE_
w __gmon_start__
0000000000002010 r __GNU_EH_FRAME_HDR
0000000000001000 t _init
0000000000003dc0 t __init_array_end
0000000000003db8 t __init_array_start
0000000000002000 R _IO_stdin_used
w _ITM_deregisterTMCloneTable
w _ITM_registerTMCloneTable
00000000000011b0 T __libc_csu_fini
0000000000001150 T __libc_csu_init
U __libc_start_main@@GLIBC_2.2.5
0000000000001135 T main
U puts@@GLIBC_2.2.5
00000000000010b0 t register_tm_clones
0000000000001050 T _start
0000000000004010 D __TMC_END__
weiqifa0@weiqifa-System-Product-Name:~/c$
gdb我觉得大家应该不会陌生了吧,可以说是Linux下的调试神器了。
weiqifa0@weiqifa-System-Product-Name:~/c$ gcc -c -g 1.c
weiqifa0@weiqifa-System-Product-Name:~/c$ ls
1.c 1.o -g
weiqifa0@weiqifa-System-Product-Name:~/c$ gcc 1.o -o 1
weiqifa0@weiqifa-System-Product-Name:~/c$ gdb 1
GNU gdb (Ubuntu 8.1-0ubuntu3.2) 8.1.0.20180409-git
Copyright (C) 2018 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
Find the GDB manual and other documentation resources online at:
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from 1...done.
(gdb) list
1 #include "stdio.h"
2
3 int main(void)
4 {
5 printf("hello,world\n");
6 return (0);
7 }
(gdb) b main
Breakpoint 1 at 0x1139: file 1.c, line 5.
(gdb) run
Starting program: /home/weiqifa0/c/1
Breakpoint 1, main () at 1.c:5
5 printf("hello,world\n");
(gdb)
使用详情:
https://www.cnblogs.com/arnoldlu/p/9633254.html
--END--
推荐阅读:
神器面世:让你快速在 iOS 设备上安装 Windows、Linux 等操作系统!
5T技术资源大放送!包括但不限于:C/C++,Linux,Python,Java,PHP,人工智能,单片机,树莓派,等等。在公众号内回复「1024」,即可免费获取!!
